- A simple, flexible solution that adapts to the requirements of your business, regardless of its size and the platforms used in your IT infrastructure.
- Multi-layered protection based on a unique combination of big data on threats, machine learning as well as the knowledge and experience of experts.
- A single console that simplifies management of all aspects of your security system, saving resources and lowering your cost of ownership.
- Strong encryption of sensitive information at the disk level or individual files and folders.
- Many convenient tools that increase the efficiency of IT systems management
- The most effective protection of workplaces, confirmed by the results of independent tests.
Cybercriminals use a variety of attack methods to gain financial gain, steal valuable data, or shut down a company. That's why businesses need a solution that combines advanced security technologies with tools that simplify security management. Kaspersky Endpoint Security Avdanced is a comprehensive solution that provides security in a complex, changing environment. Continuous network monitoring for vulnerabilities and patch management, control and data protection tools - all this helps to counter attacks of any scale and ensures the protection of confidential information.
Protection against current threats
Kaspersky Endpoint Security for Business Advanced provides multi-layered protection against known, unknown, and advanced threats with a unique combination of big threat intelligence, machine learning, and deep expertise. Powerful Tools controls help manage applications, block the use of unauthorized removable devices, and enforce Internet access policies.
Protection of confidential information
If you lose your laptop or mobile device, sensitive data can fall into the wrong hands. Encryption features allow you to encrypt files, folders, drives, and removable media. Data encryption is easily configured and managed from the same console that is used to manage all the security technologies installed on your network.
Mobile Security
Kaspersky Security for Business Advanced allows mobile device users to securely perform their work tasks. Modern technologies protect popular mobile platforms from malware, phishing, spam and other threats. And the functions of managing mobile devices (Mobile Device Management, MDM) and mobile applications (Mobile Application Management, MAM) from a single interface save you time and simplify the task of implementing uniform security policies for mobile devices.
Improving the efficiency of IT systems management
Today's corporate environments are so complex that IT administrators spend the lion's share of their time and resources on day-to-day tasks. Management tools automate execution a wide range daily administrative tasks and greatly simplifies IT security management. You get a complete picture of the state of your IT network and can manage all aspects of protection from a single console.
Centralized management of IT infrastructure
Managing security for the ever-growing number of devices in a company can be a complex, time-consuming task. A single console of Kaspersky Security Center allows you to centrally administer Kaspersky Lab's security solutions, providing a simple and convenient control IT security system.
For smaller companies, pre-configured policies are available to quickly implement security solution to your corporate network and start enjoying all its benefits. At the same time, the extensive customization options allow you to tailor the solution to your security needs.
Additional Solutions
Opportunities
Kaspersky Endpoint Security for Business ADVANCED provides tools to improve the efficiency of system administration and advanced security technologies. A single management console combines the simplicity and convenience of protecting corporate IT infrastructure.
Protecting workstations from malware
Malware Protection
The effectiveness of Kaspersky Lab's anti-malware technologies is recognized all over the world. Product Kaspersky Endpoint Security for Business ADVANCED combines signature-based, proactive and cloud technologies to provide your enterprise with the highest degree of protection against malware.
Protection for multi-platform environments*
ADVANCED provides malware protection for a wide range of platforms, including Mac, Linux, and Windows (including Windows 8). This will allow you to provide comprehensive security for your multi-platform network.
Protection against the latest threats
So-called "zero-day" threats constantly appear in the world, for which protective mechanisms have not yet been developed. Kaspersky Lab releases updates to the corresponding database much more frequently than many other security vendors. Template signature technology improves threat detection and allows you to create smaller update files. This provides strong protection and reduces the load on your systems.
Rapid Threat Detection System
Information about new malware appears in the Rapid Detection System (UDS) database even before the release of signatures, which provides timely and effective protection against the latest IT security threats.
Program Behavior Analysis
The proactive protection feature Kaspersky Lab System Monitor analyzes the behavior of each application that runs on a computer on the corporate network. If suspicious activity is detected, the program will be automatically blocked.
Deeper protection
Kaspersky Lab's active infection disinfection technology neutralizes malicious objects by working at the lowest levels of the operating system.
Opportunities cloud technologies
Millions of users of Kaspersky Lab products have allowed cloud network Kaspersky Security Network automatically collects information about possible malware infections or suspicious behavior of programs on their systems. Every day we receive more than 25 million real-time samples, analyze new IT threats and develop updates for databases and program modules necessary for effective protection. In addition, the use of Kaspersky Security Network minimizes false positives. The product reacts only to malware, without interfering with the user's work.
Prevention of hacker attacks
Host-based Intrusion Prevention System (HIPS) and Firewall control incoming and outgoing outgoing traffic, setting options for individual ports, IP addresses, or programs.
Protection against network attacks
The Network Attack Prevention feature monitors suspicious network activity. When an attack attempt is detected, it reacts according to predefined criteria.
* Kit available functions platform dependent.
File server protection
Support for multi-platform environments
Kaspersky Endpoint Security for Business ADVANCED provides protection for file servers running Windows, Linux, Novell NetWare and FreeBSD, terminal servers, such as Citrix or Microsoft, and also runs on clustered servers. Thanks to a powerful antivirus engine and an optimized scan process, the solution does not have a significant impact on system performance.
Robust malware protection
If the system crashes or is forcibly shut down, anti-malware technologies automatically kick in when the system restarts.
Easy management and reporting
Flexible management and reporting capabilities help you effectively secure your file servers while reducing administration and reporting time.
Virtualization support
Kaspersky Lab's file server security solution has received VMware Ready certification.
System administration tools
Control information resources: hardware, software and licenses
In today's complex IT environments, it is difficult to keep track of all the hardware and software running on a network. If the administrator does not keep track of all resources, how can he best manage and protect them?
Kaspersky Endpoint Security for Business ADVANCED allows you to automatically detect all devices and programs on the network and enter into the registry. Accounting for your software and hardware makes it easier to assess each system's security and ensure protection. And since the software registry contains information about licenses and their expiration dates, Kaspersky Endpoint Security for Business ADVANCED allows you to centrally provision licenses and track their life cycle.
Patch Management and Vulnerability Monitoring
Kaspersky Endpoint Security for Business ADVANCED can automatically find vulnerabilities and then install the necessary patches, thus helping to keep systems stable and secure. It works with base Microsoft data WSUS and Kaspersky Lab's own database of vulnerabilities for applications and operating systems.
Operating system deployment
Kaspersky Endpoint Security for Business ADVANCED automates the creation and cloning of images of operating systems. This saves time and streamlines the deployment process. Images are placed in a special storage, which allows deployment at any convenient time.
Installing programs
Kaspersky Endpoint Security for Business ADVANCED allows you to optimize the installation of application software and make the deployment process completely invisible to users.
Remote troubleshooting and deployment
Providing remote access to any computer in the corporate network, Kaspersky Endpoint Security for Business ADVANCED helps administrators to solve various problems effectively. What's more, if you need to deploy new software to another office, you can designate one of the local workstations as a node to receive and distribute updates to the entire office, thus reducing the load on your network.
Network access control
When connecting guest devices to your network, Kaspersky Endpoint Security for Business ADVANCED protect it from malware penetration. All devices automatically discovered on the network are divided into personal and guest devices. Personal devices of employees are checked for compliance with security policies, and access restrictions are determined for guest devices. Guest access can be configured, for example, allowing only access to the Internet, and not to the corporate local network, or completely deny access.
Encryption
Effective Encryption Methods
To ensure data security in case of unauthorized access to files in Kaspersky Endpoint Security for Business ADVANCED data encryption is possible.
Full disk encryption and file encryption
Kaspersky Endpoint Security for Business ADVANCED allows you to use both full disk encryption and file encryption. Full Disk Encryption works with the physical sectors of disks, that is, "on the border" of hardware and software. This method is extremely useful when you need to encrypt all data at once. In contrast, the ability to encrypt files and folders allows administrators to encrypt individual files when necessary for secure communication within a corporate network.
For guard hard drives Kaspersky Endpoint Security for Business ADVANCED allows you to combine both encryption methods. With this approach, the computer's hard drive is encrypted completely, and thanks to the encryption of individual files, they can be safely transferred over the company's local network. For example, for a group of computers, you can use the full hard encryption disks on each machine and data encryption on any connected removable devices. In this case, both data on computers and data on removable media will be encrypted, which can be safely used outside the corporate network.
Integration with other Kaspersky Lab technologies
Many other encryption products are not integrated into end-to-end desktop security solutions. Unlike them, Kaspersky Lab's encryption technologies are part of a single security platform developed by in-house experts. This degree of integration and a single console Kaspersky controls Security Center allow you to apply uniform policies security.
Invisibility of encryption for users
All encryption and decryption tasks are performed on the fly. Kaspersky Lab's encryption technologies prevent unencrypted versions of protected data from appearing on your hard drive. Encryption and decryption processes are invisible to users: they do not have a significant impact on the performance of their computers, thus do not reduce labor efficiency.
Application activity control When encrypting files, Application Privilege Control allows administrators to set clear encryption rules for accessing data regarding individual programs and data usage scenarios. The flexible settings feature allows administrators to determine whether the program will be denied access to encrypted data, whether it will be able to work with encrypted data, or it will be allowed to work only with unencrypted data. The decryption process is invisible to programs.
Application Privilege Control simplifies the process of creating secure backups. This is because data remains encrypted during transmission, storage, and recovery, regardless of the policy settings applied at the workplace where the data is being recovered. In addition, Privilege Control effectively prevents attempts to exchange encrypted files via instant messaging or Skype, without restricting common use these services.
Transferring data outside the corporate network
Users can create password-protected encrypted self-extracting archives of files and folders. This allows you to securely transfer important data using removable devices, email or the Internet.
Encryption keys
If one of your systems has experienced a hardware or software failure, you can decrypt the data stored on it using a key that is unique for each device and stored in Kaspersky Security Center. Thus, administrators can access important data in the event of a system failure, even if the operating system does not start.
Password recovery
If the user loses or forgets the account password, he will be able to recover it using the question-and-answer mechanism.
Mobile Device Protection**
Application control on mobile devices
You can restrict the launch of applications on mobile devices that have access to the corporate network. Default Allow mode blocks only blacklisted programs, while Default Deny mode blocks all non-whitelisted programs. In addition, there is a function to automatically detect attempts to gain root access or unauthorized flashing.
Encryption of corporate data
To ensure data security in case of unauthorized access to files, Kaspersky Endpoint Security for Business ADVANCED provides the ability to encrypt data on mobile devices. Encryption of individual files or folders is possible, and on devices running iOS, full disk or partition encryption is available.
Separate data storage
If your organization uses personal devices for work, you might want to create isolated containers on mobile devices. In this case, corporate and personal data will be stored separately on the device. You can configure automatic container encryption, as well as determine which programs can access certain device resources.
Protect corporate data in case of theft or loss of the device
If your mobile device is stolen or lost, you can block it, locate it, or remove any corporate data from the device. When you replace the SIM card in a stolen device, you will not only know the phone number of the new “owner”, but you will still be able to use the remote anti-theft protection features.
** Available only for mobile platforms specified in the list of supported platforms by Kaspersky Lab. On some mobile platforms Not all features are available.
Mobile device management***
Flexible control options
Kaspersky Endpoint Security for Business ADVANCED includes mobile device management (MDM) capabilities, including support for Active Directory, Microsoft Exchange ActiveSync and Apple MDM Server.
Kaspersky mobile device management technologies simplify deployment special application for security and control mobile applications and operating systems. The security application can be transferred to devices using wireless communication or through user workstations. In addition, you can monitor whether users have completed the download process for security tools, as well as prevent unsecured devices from accessing systems and data.
*** Available only for mobile platforms specified in the list of supported platforms by Kaspersky Lab. Not all features are available on some mobile platforms.
Control of applications, devices and web resources −
Application Control
The Application Control feature allows you to carefully monitor applications running on corporate systems.
Dynamic whitelists
Kaspersky Lab's Dynamic Whitelisting Service performs security assessments of commonly used applications. Your system receives whitelist updates via the cloud-based Kaspersky Security Network, so it always has the latest information at its disposal. Kaspersky Lab is the only company with its own whitelisting division.
Device control
Users can connect various devices to corporate systems, and to ensure security, you need to control this process. Kaspersky Device Control allows you to:
Internet access control
Kaspersky Lab's Web Control tools allow you to control the activity of employees on the Internet and filter web resources. You can allow, block, restrict, or track user access to specific websites or categories, including social media, online gaming sites and sites with gambling. This will help maintain productivity and prevent access to infected sites or sites with inappropriate content from the corporate network.
- control device access depending on the connection method, type or serial number of the device;
- establish a timetable for the application of such measures. For example, you can allow users to connect removable devices only during business hours;
Single management console
You can view, control and protect your IT infrastructure from an easy-to-use centralized management console - Kaspersky Security Center. With a single console, you don't have to spend time learning multiple interfaces for various security and system administration tools.
Encryption ransomware viruses Lately have become one of the main threats and we learn daily about new attacks, new ransomware viruses or their versions, and, unfortunately, about victims from whom cybercriminals demand a ransom in order to regain access to encrypted data. That's why Kaspersky Lab In the System Watcher component (Activity Monitoring) of the latest products, Kaspersky Cryptomalware Countermeasures Subsystem has included a special anti-encrypting malware subsystem. Thanks to a set of unique technologies, in Latvia and worldwide among users of the latest Kaspersky products who correctly used the capabilities provided by the products, there are practically no victims of encryption ransomware attacks! And this is not magic or a conspiracy, as even experts sometimes say, seeing how, unlike users of other antiviruses, fans of Kaspersky products remain unscathed in the attacks of encrypting ransomware viruses. These are simply technologies invented and implemented by the developers of Kaspersky Lab!
What products include System Watcher and Kaspersky Cryptomalware Countermeasures Subsystem?
Specific anti-ransomware technologies are included in the current versions of the following products for the Windows operating system or their Windows components.
Small Business Products:
Products corporate protection:
* All products 30-day free full-featured trial available with local technical support. To try and install as well.
How does System Watcher and Kaspersky Cryptomalware Countermeasures Subsystem work?
Kaspersky Lab processes an average of 315,000 new malware samples daily. With such a large influx of new malware antivirus companies very often you have to protect users from malware attacks that they are not yet aware of. By analogy with the real world, this would be the same as identifying a criminal before his fingerprints, photograph, and other data are obtained. How to do it? Observing and analyzing behavior. This is exactly what the component called System Watcher (Activity Monitoring), which is built into the latest products of Kaspersky Lab, continuously monitors the computer system and does.
System Watcher observes the processes taking place in the system and detects malicious activities, using Behavior Stream Signatures (BSS) signatures and thus allowing to identify and stop completely new and unknown malware by their behavior. But that's not all. As long as it becomes clear that some program is malicious, it may have time to do something. Therefore, another feature of System Watcher is the ability to roll back changes in the system made by malware.
In order to roll back the changes made by the new encrypting malware, Kaspersky Lab specialists added to the System Watcher component an anti-encrypting malware subsystem. Kaspersky viruses Cryptomalware Countermeasures Subsystem, which backs up files if they are opened suspicious program, and subsequently, if necessary, restores them from saved copies. Thus, even if the encrypting virus is new, that is, the antivirus does not have its "fingerprints", and it is not identified by other mechanisms, System Watcher detects it by its behavior and, using the already mentioned subsystem, returns computer system with the state it was before the malware attack.
Recognizing an unknown encrypting malware by its behavior, stopping its operation and rolling back the changes made by it (replacing encrypted files with non-encrypted copies) can be seen in the demo video below.
Here it is necessary to clarify that for each specific user, situations when it is necessary to use Kaspersky Cryptomalware Countermeasures Subsystem can occur extremely rarely, since information about each incident with an unknown malware in a matter of seconds gets into the cloud of Kaspersky Security Network and other users of Kaspersky solutions from this moment already reserved against new threat early detection system. This means that any further attempt to infect computers of Kaspersky users will be blocked by an early signature. It is the action of such unique mechanisms that explains the fact that in Latvia there were practically no victims among users of the latest Kaspersky products, as it works like a global immune system for all 400 million Kaspersky users worldwide!
For more information about System Watcher and Kaspersky Cryptomalware Countermeasures Subsystem, visit English language can be found in PDF documents:
What else do you need to know about System Watcher and Kaspersky Cryptomalware Countermeasures Subsystem?
System Watcher and together with it automatically Kaspersky Cryptomalware Countermeasures Subsystem in accordance with the initial settings of the manufacturer are enabled by default. After installing the products, the user does not need to make any additional actions to use the technologies described above.
It should be especially noted that System Watcher is not included in the product Kaspersky Anti-Virus for Windows Workstation 6.0 (released 2007), which is still occasionally used. Users of this product are encouraged to use the free upgrade to more new Kaspersky Endpoint Security for Windows. Legal users can download and install the latest versions of products for free, for example, from the " " section of this site.
- There will not be much demagoguery, since the article will turn out to be quite large anyway! Let's see what can be done if your computer is infected with an encryptor: First you need to find out what kind of encryptor did this bad job with your files. Below at the end of the article there are links to Services that will give all the information on your evil harm that is operating on your computer. If the name of your evil harm coincided with the names in this article, then this is half the trouble, and so we read further what Kaspersky offers us in the fight against ransomware encryptors. To be honest, these viruses are quite strong, you really have problems. You can remove this muck from your computer, this is not a problem, but returning the files is a question:
- I list the name of the ransomware and at the end you post the name of the program that might help you:
- When Trojan-Ransom.Win32.Rannoh is infected, names and extensions are locked- . .
- When Trojan-Ransom.Win32.Cryakl is infected, (CRYPTENDBLACKDC) is added to the end of files.
- The Trojan-Ransom.Win32.AutoIt extension changes with the pattern @_.
- For example, _.RZWDTDIC.
- When Trojan-Ransom.Win32.CryptXXX is infected, it changes to the .crypt template.
- We check for reliability by the service that I will post at the end of the article and if everything matches, then download the utility:
- .from the official website of Kaspersky .
- .with cloud verified by Kaspersky
- After clicking on the button to start scanning, a window will open in which you need to show the encrypted file.
- Then the program itself will do everything. If he does!))) But let's not talk about the bad, everything will be fine!
- Designed to fight viruses with encoders: Trojan-Ransom.Win32.Xorist, Trojan-Ransom.MSIL.Vandev
- You can recognize the encoder by the following steps: Displays a window something like the one below:
- On drive C:/ makes files called "Read Me - how to decrypt files". Having opened such a file, it will contain content similar to the one in the picture below.
- Also in Windows folder there is a file named CryptLogFile.txt. It records everything that was encrypted.
-
File decryption
- from the official website of Kaspersky
- cloud verified by kaspersky
- Run and show the encrypted file and wait while the utility tries to decrypt the file.
- If the XoristDecryptor utility does not detect the file, it will offer to send it by mail. Kaspersky Lab will study the file and update the XoristDecryptor anti-virus database. That with re-treatment there is an option to return your files.
The next utility is called RectorDecryptor
- As stated above, it is from Kaspersky and is used to decrypt files infected with ransomware: Trojan-Ransom.Win32.Rector
- jpg, .doc, .pdf, .rar.
- File names after encryption:
- vscrypt, .infected, .bloc, .korrektor
- Author's signature in the form ††KOPPEKTOP†† and contact with him can be kept:
- ICQ: 557973252 or 481095
- In some cases, the attacker asks to leave a message in the guest book of one of his sites that are not working or working at the right time for him:
- https://trojan....sooot.cn/
- https://malware....66ghz.com/
- Also, a banner on the desktop of the form below indicates that your files are encrypted with this encoder:
- How to try to get your files back:
- Download a utility from Kaspersky called
- from the official website of Kaspersky
- cloud verified by kaspersky
- As in all other above utilities from Kaspersky. Run the downloaded utility and by clicking the Start scan button in the opened window specify the encrypted file.
- You can find a report on the work done, as in the examples above with programs, at: C:\RectorDecryptor.2.3.7.0_10.05.2010_15.45.43_log.txt Time and date are approximate, you will have yours.
- To combat ransomware from Kaspersky:
- Trojan-Ransom.Win32.Rakhni, Trojan-Ransom.Win32.Autoit, Trojan-Ransom.Win32.Agent.iih, Trojan-Ransom.Win32.Aura, Trojan-Ransom.AndroidOS.Pletor, Trojan-Ransom.Win32.Rotor, Trojan-Ransom.Win32.Lamer, Trojan-Ransom.MSIL.Lortok, Trojan-Ransom.Win32.Cryptokluchen, Trojan-Ransom.Win32.Democry,Trojan-Ransom.Win32.Bitman versions 3 and 4,Trojan-Ransom.Win32. Libra,Trojan-Ransom.MSIL.Lobzik and Trojan-Ransom.Win32.Chimera
Trojan-Ransom.Win32.Rannoh, Trojan-Ransom.Win32.AutoIt, Trojan-Ransom.Win32.Fury, Trojan-Ransom.Win32.Crybola, Trojan-Ransom.Win32.Cryakl or Trojan-Ransom.Win32.CryptXXX versions 1 and 2 .
What will be the names of your files after encryption:
XoristDecryptor
What files does it encrypt:
RakhniDecryptor Utility
Umnik_ADS January 18, 2010 at 01:51 pm
Kaspersky KryptoStorage inside and out
- Information Security
In December 2009, Kaspersky Lab announced the commercial release of Kaspersky KryptoStorage. This program was created on the basis of InfoWatch CryptoStorage and adapted for use on home PCs. In this article, I will try to go beyond the usual review and describe the program as fully as possible, warn about pitfalls, and give general advice on its use. Kaspersky KryptoStorage is needed for:
- protection of confidential information from third parties;
- prevent data leakage while saving the operating system service information on disk (for example, memory dumps);
- deletion of data without the possibility of recovery.
- Protected folder. This is a special folder created by the program in the NTFS file system. When connected, you can work with it as with a regular folder, with some reservations.
- W protected container. This program-generated special file. When you connect a container, you can work with it as a logical drive. This file can be copied to flash, burned to CD/DVD, sent via e-mail, put it on a file hosting service and use it on any PC where the program is installed and the password for connecting the container is known.
- Protected partition (disk). This existing section disk or a disk converted (encrypted) by the program. After connecting a protected partition/disk using Kaspersky KryptoStorage, it becomes possible to work with it as with a normal partition/disk. It is also possible to encrypt system and/or boot partitions and Mass Storage class devices (Flash drives, USB storage devices, etc.).
Installing Kaspersky CryptoStorage
Before installing the program, you need to make sure that the platform on which the program will run meets the requirements.Hardware requirements:
- CPU Intel Celeron 1 GHz or higher or equivalent
- 256 MB free RAM
- 10 MB free disk space to install the application
- operating system Windows 2000 SP4 (with all updates)...
- ...or Windows XP SP2...
- ...or Windows 2003 Server...
- ...or Windows Vista SP1...
- ... or Windows 7
We launch the program installer. The installation process is no different from installing any other application, the user goes through the same steps of accepting the license agreement, choosing the installation location (%ProgramFiles%\Kaspersky Lab\KryptoStorage\ is suggested by default), and completing the installation wizard. At the end, it is proposed to restart the computer and after the reboot, the application is completely ready for use. Important! During the reboot process, it is highly recommended not to turn off the computer. This can cause a crash and an error on each subsequent reboot! If for some reason the failure still occurred, then you need to use the option to download the latest successful configuration and reinstall the app.
Let's start with the program. Here's what the main window looks like:
Group Data encryption. This group contains three buttons with which you can create protected folder, protected container, or encrypt disk (disk partition). Let's do it!
Folder encryption in Kaspersky KryptoStorage
Let's create protected folder. Click on desired button. A window appears where you need to specify the folder (disk) where it will be located. protected folder, name for protected folder, password and password hint. By default, it is proposed to create a "New Secure Folder" in the "My Documents" of the current user.By clicking on OK, the folder is created. What you need to know about protected folder?
- All files and folders inside the protected folder are also encrypted and protected. That is, if you copy protected folder file that lies outside it, then the copy will be protected.
- Performing any action on protected folder(copying, moving, deleting, renaming, archiving, writing, reading) and its contents is possible only when this folder is connected.
- Access to protected folder over the network is prohibited, but the connected folder is available to all users and programs that can work with the computer locally on behalf of the connected folder. For example, you can work with a connected folder via RDP.
- If the file is copied from protected folder outside, the copy becomes unprotected. At the same time, protection source file is saved.
- The program does not allow you to protected folders and their content listed actions:
- delete to trash
- moving within a single volume of files and folders containing files. When you try to move to the destination will be created empty folder with the same name as the original
- However, some file managers(for example, Total Commander) when moving, first makes a copy of the object, and then deletes the original one. In this case, the transfer will be successful.
- Within the same volume, you can move unprotected folders that contain protected folders to other unprotected folders without restrictions. Connection protected folder this is not required, but protection is maintained. In other words, there is regular folder"A" containing protected folder"B" is the usual folder "C". Moving "A" to "B" will take place without any restrictions. Connection "B" is not required, and the protection will be preserved.
- An unprotected folder with subfolders protected folders can be moved to trash if nested protected folders connected. A folder moved to the trash can be deleted and restored. When recovering protected folders will be connected.
- Some file managers (for example, Total Commander) cannot move such a folder to the trash.
- Work with the protected folder possible if the subsystem is enabled Protected Folders. The status can be viewed in the main window in the block CryptoStorage Subsystems.
- Creation protected folder only possible on media that is not write-protected.
- The user must have rights to create the folder.
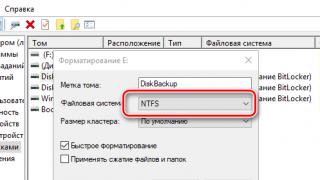
- Protected folder can only be created on the NTFS file system.
- Length complete The folder name must not exceed 255 characters.
- Protected folder impossible to create inside another protected folder.
- Protected folder cannot be created inside an EFS protected folder.
- Protected folder can be created on a hard disk, removable media, as well as on a disk protected by the program or in encrypted container(when the disk or container is connected).
- The password can be up to eight characters long.
That is, in a free space (not on a folder, not on a file), right-click, Create - Folder Kaspersky KryptoStorage.
- the password must be at least six characters (maximum, I remind you, eight)
- the password can include numbers, latin letters, spaces and special characters
- it is desirable that the password consists of both numbers and letters (in the upper and lower case), and special characters.
- common words and stable combinations
- a set of characters that are combinations of keys arranged in a row on the keyboard (qwertyui, 12345678, qazxswed, etc.)
- personal data (names, surnames, dates of birth, passport numbers, insurance numbers, etc.)
- passwords from other programs and services (mail, forums, etc.)
So the folder has been created. Let's try to protect the photos, the role of which will be played by the desktop wallpaper.
Video #1
Let me explain what happened in the video.
- Copied the objects that need to be protected to the clipboard (moving, as I described above, is not possible)
- Connected a protected folder
- I entered incorrect data to demonstrate the hint. As you can see, the hint meets two main requirements: it is clear to me, it does not say anything to others.
- Inserted files into protected folder
- Dismantled protected folder
- launched irrevocable deleting source files
Creating a secure container in Kaspersky KryptoStorage
What you need to know about protected container?- The device on which the container (container file) is created must not be write-protected.
- The container cannot be created on a CD/DVD, but it can be written there as a file once it has been created.
- The user creating the container must have permissions to create files.
- Working with a container is possible only if the system has Kaspersky KryptoStorage installed and the subsystem Protected containers.
- A container can be created on a hard drive, on flash, inside another container (when attached), inside protected folder(when connected), inside protected disk(when connected) and also copied to all these places.
- The container size limit is imposed only by the file system itself:
- for FAT16 - 2 GB
- for FAT32 - 4 GB
- for exFAT - 256 TB
- for NTFS - 16 TB
- You can create a container in the same way as protected folder two ways:
- from the program window
- from the context menu
- By default, containers are prompted to give the .kde extension. This extension is associated in the system with the program at the installation stage. If you use this extension, then you can mount the container double click mouse or from the context menu. If another extension is used, then the container can only be mounted from the context menu of the container file (Kaspersky KryptoStorage - Mount container).
- There is no auto unmount feature.
- The connected container can be shared (moreover, the system will remember the sharing if the same letter is used for mounting). Accordingly, the following scenario is possible: the user logs in to the system, connects the container and logs out, and the container remains shared and accessible over the network.
- Because container is a regular file, then you can protect it from deletion by placing it in protected folder or at protected disk.
After creating the container, the program will offer to format it. Without formatting, nothing can be written to the container. If you refuse to format at this stage, then the prompt will appear every time after mounting and when accessing the mounted disk from Explorer (try to open it).
When formatting, keep in mind:
- if choose fast mode formatting and the FAT16/FAT32/exFAT file system, then the container file will have the minimum possible size and grow to the size specified during creation as it is filled. This will save space where the container file resides.
- When choosing file system NTFS container file will immediately have the specified size
- with full formatting, regardless of the file system, the container file will immediately have the size specified during creation
The container is connected as a disk (hard or removable) and therefore it needs to be assigned a letter. The "Logical drive" drop-down menu will list all available drive letters. Mount mode will not be available until the container is formatted.
Container connection modes:
- only for reading. In this mode, nothing can be written to the mounted container and nothing can be deleted from it
- the checkbox is checked automatically and cannot be unchecked if the container file has the "Read Only" attribute
- In MS Windows 2000, it is not possible to work in read-only mode with containers formatted in NTFS
- connect as removable drive. If the checkbox is checked, then the disk is connected as removable. If the checkbox is cleared, then the disk is connected as a fixed one (hard disk).
- In MS Windows Vista, the container can only be connected as a removable disk
Demonstration of work with protected container:
Video #2
Please note that dismantling takes some time. However, you can restart or shut down the computer while the containers are mounted; after booting the OS, they will be unmounted.
Disk encryption in Kaspersky KryptoStorage
What you need to know about disk encryption?- If protection is placed on a partition that is boot/system, then you will need to authorize to access it before loading the operating system.
- If the system and boot partition we are on different logical drives and both are protected, then you need to connect each of these sections.
- Installing protection on the system partition hard drive provides protection for the memory dump file (crash dump), as well as the contents of RAM during the transition to sleep (hibernate) mode.
- Working with a protected disk or removable media is possible if a computer with installed system subsystem started Protected drives.
- If the computer has a protected system and/or boot partition of the hard disk, the system configurator does not allow disabling the subsystem Protected drives. In this case, in the main program window in the section CryptoStorage Subsystems block Protected drives not available for changes.
- It is not recommended to use it on computers with multiple operating systems and at the same time protect the disk partitions necessary to boot the installed operating systems.
- Data about all protected logical partitions of the physical media (physical hard drive, Flash-drive, etc.) are located in the root directory of the first logical partition of the physical media in the file iwcs.bin. When formatting a partition containing a file iwcs.bin, or if this file is deleted, replaced, or damaged, access to all protected logical partitions of the physical media may be lost.
- Installing protection on logical partitions of hard drives and removable media is possible if the corresponding device has a sector size 512 bytes (standard sector size for most devices of this type).
- Installing protection on dynamic partitions is not supported.
- Protection can only be installed on local drives. Network drive protection is not supported.
- On the same physical disk, protection installation/removal/reinstallation for several logical partitions cannot be started at the same time. You can work with logical partitions of different disks simultaneously.
- Protecting the logical partition of the hard drive on which the system is installed is only allowed if this partition is a system and/or boot partition.
- Protection can be set provided that the protected partition is writable.
- You can start installing protection on a removable drive only if the files on the removable drive are not being used by any programs. It is possible to use files on a removable drive during protection installation.
- IN Kaspersky CryptoStorage protection not supported CD/DVD-disks.
- Changing the size of hard disk logical partitions (just like their division, merging) can lead to data loss. If these changes are necessary, then unprotect partitions before starting work.
There are two ways to set protection:
- From the main program window, the button Encrypt disk.
- From the context menu of the object, select Kaspersky KryptoStorage - Set disk protection.
Upon successful completion, the user is notified.
Until the protection is installed, you can click on the "Stop" button. Then an authorization window will appear (where you need to enter the password for accessing the object). The next window will be a message about the successful interruption of the protection installation.
If the protection setting is interrupted (manually, or the system went into standby/hibernation mode, or the computer was powered off), the object remains partially encrypted, but is considered protected. Therefore, working with this object is possible only when it is connected and the password is entered. Of course, if the protection has not been fully established, then some of the information remains unencrypted. In a situation that has arisen, you can either resume the installation of protection, or cancel its installation.
To resume the installation of protection, you need to connect the object (if it was disabled) and in its context menu select Kaspersky KryptoStorage - Continue installing disk protection. The installation process will continue.
To cancel the protection of an object, in the context menu of the object, select Kaspersky KryptoStorage - Cancel installation of disk protection. Authorization is required to perform the operation.
To work with a protected object, you must first connect it. To do this, in the context menu of the object, select the item Kaspersky KryptoStorage - Connect Disk. The procedure requires authorization. At the end of work with the object, it is recommended to turn it off, because the connected object is not a protected object. To do this, select the item in the context menu. Kaspersky KryptoStorage - Disable Disk. Objects will also be disabled if the OS was rebooted.
Booting from a protected system and/or boot disk is only possible after authorization. An authorization request will appear during the PC boot process before the OS boots: 
After successful authorization, the OS will be loaded. If you make a mistake when entering the password, a message about the incorrect password and a suggestion to press any key will appear. If a hint was specified when setting protection, it will be displayed: 
You can try to enter again. If the hint was not set, then to repeat the authorization procedure, you will need to restart the computer using the Ctrl + Alt + Del combinations.
To remove protection from an object, select the item in its context menu. Kaspersky KryptoStorage - Remove disk protection. The procedure requires authorization, and the object must be previously connected. The unprotection process, as well as the installation of protection, can be interrupted and resumed. The work algorithm is also similar to the algorithms for setting protection.
Kaspersky CryptoStorage settings
Let's go back to the main window. Under the block Data encryption there is a block Subsystems. Each of the subsystems provides protection for objects of a certain type: disks, containers, folders. If the subsystem of some type of object is stopped, then the ability to work with this type of object is lost. The status of the subsystem (on or off) is indicated in the second column of the block. The third column allows you to change this status. To stop the subsystem working with protected folders, you need to uncheck the "Autostart" checkbox for this subsystem and restart the computer. To start the subsystem, you must check this box and also restart the computer.In the block Object connection settings there is only one setting that is responsible for auto-opening connected objects in Explorer. You can either disable opening objects at once by unchecking Open objects with File Explorer in a new window after connecting, or enable for all at once. Set up auto-open protected folder and at the same time prohibition of auto-opening for protected container impossible.
The button opens the license management window:
The license can be in the form of an activation code, it can be a file. The license file is created automatically when activated with a code. The license is perpetual for the operation of the program. Expiration means that there will be no user support, but the functionality is retained.
The button is needed to free up space on the hard disk, logical partition, flash, etc., when access to them is lost. Operations require local Administrator rights. This situation may arise if:
- the access keys to the protected partition have been lost, so it is impossible to connect it or remove protection
- protected partition was formatted after deletion with subsystem running Protected drives. After reinstalling the program with the subsystem running by default Protected drives access to the formatted object becomes impossible
- the size of the protected partition has been changed. As a result, there was a discrepancy between the considered size and the actual size of the protected partition. For correct resizing, you must first unprotect the object, resize it, and then re-protect it.
- complete all operations related to installation, reinstallation and removal of protection on all partitions of a physical disk or removable media
- disable protected partitions of the physical disk, information about which you want to delete from
To do accessible space on the disk occupied by the protected partition you need:
- In the main window, click the button
- In the Disk Recovery window, specify the protected partition whose information you want to delete from the disk
- In the context menu of the section select Remove encrypted area information
- In the window with a warning about the loss of encrypted information, click "Yes".

On this I consider my article finished and I will gladly read your comments. Additionally, I inform you that I am included in the composition Kaspersky PURE, the commercial release of which is just around the corner.
Actively used to write the article
22.04.2013 Vladimir Bezmaly
In cryptography, encryption is the process of encoding information in such a way that only authorized users can read the data. In an encryption scheme, information or "plain text" is protected by an encryption algorithm, turning it into unreadable "ciphertext". This is usually done by applying an encryption key which specifies how the data should be encoded.
Unauthorized users can see the ciphertext but cannot read the original data. Authorized users can decode the ciphertext using a decryption algorithm, which usually requires a secret decryption key that only they have access to. An encryption scheme typically needs a key generation algorithm to generate arbitrary keys.
Full Disk Encryption (FDE) is one of the most effective ways protecting data stored on laptops from theft or loss along with the device. Whatever happens to the device, the FDE mechanism makes it possible to ensure that all information stored on it is inaccessible to the person in whose hands the device fell into.
When using FDE, all data on the hard drive is encrypted. In fact, every sector is encrypted. However, access can only be authorized user who knows the password. In addition, this technology can be applied to removable media such as USB drives. Let's take a look at how the encryption system works using the example of Kaspersky Security for Business.
How does FDE work?
FDE is used before the system boots. This means that the applied technology starts its work immediately after pressing the power button on the device. Disk encryption can be run either directly on the user's computer or centrally using the Security Center module. In this case, the program encrypts all selected drives and installs the authorization module in the boot environment. When the computer is turned on, the operating system starts to boot in an encrypted environment (Figure 1). Encryption slightly slows down system performance, which is common with all implementations of encryption software from any vendor. All encryption (decryption) operations occur transparently to the user, regardless of the software they use. It encrypts all hard disk (paging file, hibernation file, temporary files, also often containing important data). And if the user loses the password to the encrypted hard drive, the information can be decrypted using a secret key known only to the product administrator. The FDE function is included in the distribution of Kaspersky Endpoint Security. Security administrators can centrally manage this complex using the Security Center.
| Figure 1. Scheme of FDE operation |
Benefits of FDE
Forced encryption of sensitive data. The end user does not have the ability to reconfigure the encryption mechanism. FDE prevents unauthorized access to data through an authentication mechanism (name/password). When you enter the correct username/password combination, the system extracts the key needed to decrypt the files on your hard drive. In fact, this adds additional level security, since the encrypted data will be useless to the attacker after the destruction of the cryptographic key.
Centralized key management. All encryption keys are stored in the Security Center and are only available to the security administrator.
Centralized encryption management. Decryption key management, mobile device access control, reporting, and lost password recovery are available only to the security administrator and only when the Security Center is running.
Simplicity and flexibility. From the point of view of the end user, encryption is completely transparent. After successful authorization, the encryption/decryption process occurs seamlessly and does not affect the user experience.
Centralized data recovery. In the event of password loss or media damage, data can be recovered and decrypted using a special, centrally managed disaster recovery procedure.
Disadvantages of FDE Technology
Please note that FDE only encrypts information stored on encrypted media, so if you send it by email or copy it to another medium, you are copying it in the clear.
The decryption key must be available before you receive a password request in the interface to access the system. Therefore, if your hard drive is damaged, it can be very difficult to recover data, even using special software.
You can use FDE for encryption SSD drives, however, you should take into account that you lose in speed - one of the main advantages of using an SSD.
The biggest drawback, in my opinion, is support for password-only authentication. Smart cards, biometrics, tokens are not supported today.
How does FDE work?
Each hard drive on the end device uses two keys. The first key is used to encrypt/decrypt data on the hard drive, Disk Encryption Key(DEK). The second key is for encrypting DEK and other sensitive data - Disk Master Key (DMK). The boot disk DMK has a special purpose - it is DMK encryption/decryption for all other hard disks and user policies. Such a key is called an End-Point Key (EPK), and for the boot disk,
"EPK"="Boot Disk DMK".
The end device stores all sensitive data (metadata) in a special metadata store, which can also be accessed on behalf of the user before bootstrap, and from kernel mode. To check metadata integrity and authenticity, a special Authentication Tag is calculated using the DMK as a key (according to the NIST-SP-800-38B CMAC specification).
Boot disk encryption
Depending on the type of media - boot drive, data drive, or removable drive - metadata has its own physical deployment format. The boot disk with FDE installed has its own Custom MBR boot entry. This Custom MBR entry is not encrypted and contains a table with the following important parameters: The GUID of the drive and the address (number of sectors) of the location of the Pre-Boot Components. Other disk data is encrypted at the sector level with the AES-XTS algorithm with a key of 256 bits, except for two areas (Figure 2):
- the Pre-Boot Components area contains the executable components (PBE, INT13 handler, initial MBR) and the address of the Endpoint Metadata Storage metadata block;
- the Endpoint Metadata Storage area contains all the metadata (vulnerable information) of the end device used for authentication and authorization.
.jpg) |
| Figure 2. Boot hard drive encryption mechanism |
Both storages, Pre-Boot Components and Endpoint Metadata Storage, can be located in the middle of the disk, among the sectors with encrypted data.
The Endpoint Metadata Storage area contains two main sections (Figure 3):
- the Endpoint Metadata section contains information related to the entire end device (password policies and end device settings) and the corresponding boot drive information (encrypted DEK and Metadata Authentication Tag);
- the Users Metadata section contains information related to users - user authentication data, encrypted by DMK, custom policies etc.
.jpg) |
| Figure 3. Structure of Endpoint Metadata Storage |
The Endpoint Metadata partition consists of one continuous block containing auxiliary information (metadata version, signature, size of this block, user partition size, number of users, encryption and authentication parameters), encrypted using DMK DEK (CBC AES algorithm, 256 bit key), Authentication Tag of the entire Endpoint Metadata Storage, encrypted with a DMK key (AES-CMAC, 256-bit key) and endpoint settings such as password policies and the Security Center public key.
The user metadata section contains one or more user metadata blocks. Each user metadata block is a contiguous block containing the following sections.
- Ancillary information (signature, size of the entire user block, record status, size of the authentication sub-block and number of authentication records, size of the data sub-block).
- User ID (User ID) - hashed user name for registration in the system (SHA1 algorithm).
- The User Authentication Data block contains one or more authentication entries: Password Based Authentication stores the information required to authenticate a user with a password. The Token Based Authentication entry stores the information required to authenticate a user with a security token. This entry contains the ID of the token and the DMK encrypted with the public key of the token. The Certificate Based Authentication entry stores the information needed to authenticate a user with a certificate. This entry contains the certificate ID, key parameters, the private key of the user certificate encrypted with a password, the DMK encrypted with the public key of the user certificate.
- The User Data block, encrypted with DMK (CBC AES, 256 bit key), contains user policies with user account information and username.
Thus, each user can have one or more various types authenticators at the same time.
Other drives and removable drives with FDE installed also have a Custom MBR entry (in plaintext), but of a slightly different type. This Custom MBR contains the GUID of the disk, and a Device Metadata Storage block containing authentication data and encrypted keys (DMK and DEK). Other data on these types of media is fully encrypted (AES-XTS, 256 bit key), see Figure 4.
The Device Metadata Storage area includes two main sections.
- The Device Metadata section contains information related to the current device, such as identification data, encrypted DEK, and Metadata Authentication Tag.
- The Device Unlocking Metadata section contains information related to two unlock methods: basic password (for offline device) and password auto unlock(for a secondary drive installed in end system), and user authentication data and an encrypted DMK.
The Device Metadata section consists of one contiguous block containing auxiliary information (metadata version, signatures, size of this block, encryption and authentication parameters) encrypted with DMK DEK (AES CBC, 256 bit key) and the authentication Tag of the entire Device Metadata Storage, encrypted DMK key (AES-CMAC, 256 bit key).
When encryption is started, metadata is created on the end device for all encrypted hard drives and user accounts.
Booting on a computer with an encrypted boot disk
If the boot disk is encrypted on the host, then the user must authenticate with the Preboot agent before booting the operating system. Based on the name and password entered by the user, all FDE-encrypted devices that were encrypted on this host are connected. If an FDE-encrypted device was connected to the host, the encryption of which was performed on another host, then access to such a device will be provided only after the operating system is loaded and the product starts.
Granting access to the contents of an encrypted drive
The product provides access to the contents of an encrypted object to any user who has successfully logged in to operating system. To do this, the first time a user accesses an encrypted disk on this computer the product obtains access keys from the encrypted disk itself. The product extracts a cryptocontainer from the encrypted object and, using the SC encryption service, obtains all the necessary keys from it. After successfully obtaining the key, the product saves it locally for this user(except for some system users). When a user accesses an encrypted object again, the product uses the key stored locally for that user. In the case of several simultaneous user sessions, all users get access to encrypted objects if access has been granted to at least one of them. In the absence of a product, access to encrypted files on a removable device can be granted by the Portable Mode special agent. This agent is installed by the product on the device during the application of the corresponding policy and allows access to encrypted files after the user successfully enters the password.
File level encryption
File Level Encryption (FLE) enables data encryption in certain files and folders on this device(Figure 5). This makes the selected information inaccessible to unauthorized funds view, no matter where they are stored. FLE allows system administrators automatically encrypt files based on attributes such as location and file type.
.jpg) |
| Figure 5. FLE operation scheme |
Unlike FDE full disk encryption, where the entire partition or disk is encrypted, FLE does not encrypt all information about the hard disk or portable device data storage, as is done with FDE. Administrators can choose what data should be encrypted (or unencrypted) using rules that can be implemented through a convenient user interface software. Encryption rules can be created so that you can decide what should be encrypted, for example, you can create lists of files to encrypt by their name, extension, or directory. You can specify files for removable media or automatically encrypt files created or modified by any given application.
The host on which the user first accesses the encrypted object must be managed by the same Server Security Center as the host on which this object was encrypted. Otherwise, the Security Center Encryption Service will not be able to unpack the cryptocontainer, and the product, accordingly, will not receive keys to access the encrypted object.
If, for any reason, access to local storage keys on the host is lost (the local storage is damaged, the user's password is reset by the administrator), then when the user accesses the encrypted object again, the product will try to get the keys from the encrypted object.