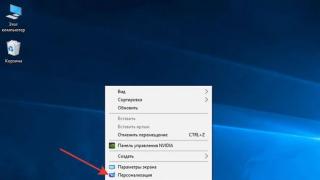
A Microsoft Access database file, like other Office documents, can be protected with a password to open it. Copy the file BDTur_firm.mdb we worked with in the first chapter, name it "BD_withPassword.mdb". To set a password, we need to open the database in the so-called exclusive, single-user mode. The fact is that the ability to set a password when several users work at the same time 1 Microsoft Office Access 2003 supports 255 concurrent users. would lead to errors, so MS Access does not provide it. We start the program, in the main menu we go to "File \ Open", go to the desired directory, select the file, from the drop-down list of values of the "Open" button, select "Exclusively" (Fig. 3.6):
The database window appears. In the main menu, go to "Service \ Security \ Set database password", in the "Set database password" window, enter the password "12345" and confirm it (Fig. 3.7).
Rice. 3.7.
Now, every time you open this file on any computer, you will need to enter the specified password (Fig. 3.8).

Rice. 3.8.
To change the password, we need to delete the existing one and then set a new one. Open the database again in exclusive mode, in the main menu go to "Service \ Protection \ Delete database password". In the window that appears, enter the current password, after clicking the "OK" button, it will be deleted. To enter a new value, again go to the "Set database password" menu item, this time we will enter a more complex password "q1w2e3r4t5y6u7i8o9p0".
Protecting a file with a password is extremely insecure and cannot be used in real applications. The password is stored in plaintext and is very easy to crack. There are many utilities on the Internet designed for this, such as Access Password Recovery Genie (http://www.lenosoft.com). After starting this program, select the MS Access file, the password for which you need to guess, and the password instantly appears in the main window (Fig. 3.9).

Rice. 3.9.
Next, we will need to enter the password again - in order not to waste time, set its value again to "12345". Let's now connect to the database file from applications. Of course, you will now doubt whether to use password setting as a security tool at all, but in any case, we need to learn how to connect even to such an "untrusted" database. Create a new Windows project and name it "VisualBD_withPassword". From the Toolbox window, drag a DataGrid control onto the form, set its Dock property to "Fill". Go to the Data tab and double click on the OleDbDataAdapter object. In the wizard that appears, configure the connection to the BD_withPassword.mdb file. Now, in the "Data Link Properties" window, when checking the connection, an error message appears (Fig. 3.10):

Rice. 3.10.
Based on the text of the error, there is a natural desire to uncheck the "Empty password" box and enter "12345" in the password field. But this time also error 2 Also make sure that your database file is not open in Microsoft Access itself.(Fig. 3.11):

Rice. 3.11.
The fact is that the interface of the "Connection" tab is intended for entering account parameters when protecting at the user level. Next, we will consider it. Here we again check the "Empty password" checkbox and go to the "All" tab. Double-click on the Jet OLEDB:Database Password property (or, having selected it, click on the "Change value" button), in the "Change property value" window that appears, enter the password "12345" (Fig. 3.12).

Rice. 3.12.
Go to the "Connection" tab - finally we managed to get access to the database (Fig. 3.13).

Rice. 3.13.
We press the "OK" button to close the "Data Link Properties" window, in the next steps of the "Data Adapter Configuration Wizard" we configure the extraction of all records from the "Tourists" table. In the last step of the wizard - including the password in the connection string - select the "Include password" button; we will examine the string generated by the wizard (Figure 3.14):

Rice. 3.14.
On the form components panel, select the DataAdapter object, go to its Properties window and click on the Generate dataset link. We leave the name of the DataSet object offered by default. In the form constructor, we fill in the DataSet object, and also define the data source for the DataGrid element:
public Form1() ( InitializeComponent(); oleDbDataAdapter1.Fill(dataSet11); dataGrid1.DataSource = dataSet11.Tables.DefaultView; )
Here we are specifying the index (zero) of the only table in the DataSet object.
We launch the application. The form displays data from the database (
The widespread use of ms Access has given rise to a whole class of programs that allow you to find out "forgotten" passwords to databases. I don't know who was the first, but they look alike like twins.
Testing
All programs considered in this review cope with passwords like "may". But not everyone allows you to find out non-standard passwords. The test results are presented in the table. You can read more about protection methods in the article Protecting and cracking Access databases. Here it can be noted that he became the leader. The Access database file, protected by a password of 20 non-printable characters and a title of a different version, remained unapproachable. Unfortunately, only the password remained inaccessible, but not the database. allows you to restore the contents of tables, but almost completely recreates the file, including tables, queries, forms, macros, reports, and module code. Registered versions of programs took part in testing.
Allows you to open Access database passwords. In addition, it is possible to remove or replace the password for Access 97 databases.
The only program that gives out the password in hexadecimal form, which allows you to see passwords using non-printable characters. I used to think so, but in fact, a string is translated into a hexadecimal form and, as a result, there is no sense from it. Access 97 databases with a password of 20 characters are considered corrupted and do not produce any result.
AOPR allows you to define passwords for many MS applications. With regard to the Access database, it can determine:
- Database password
- Database owner - username (user) and its identifier (ID)
- Information about the owners of database objects
- Usernames and their passwords
- Membership of users to groups
The program determines passwords for databases of format 97 - 2000 - 2003. For Access 97 databases it is possible to change and delete passwords.
It should be noted that the program does not stand on the meta in its development. Password detection algorithms are being improved. If in the previous version (AOXPPR) for Access 97 - only the first 14 characters, and if it encounters non-printable characters - it says that the file is damaged. Access 2k - normally reads all 20 characters, but produces question marks on Unicode. In the described version, all passwords are normally defined, and non-printable characters are normally copied to the clipboard.
This is a set of utilities that allow you to find out passwords for a very large number of applications. The Office Key program works with the Access database. It allows you to determine the passwords of the database, groups, users and their passwords from the workgroup file. Similar functions are provided by another utility from this manufacturer - Access Key. Archive size - 662 KB. It is a standalone product that is not part of the Passware Kit.
The program does not allow you to find out the identifiers (ID) of users, the owner of the database and its objects. Thus, in terms of capabilities, it is inferior. However, it did well on the test. Copies the real password to the clipboard, not question marks. Normally determines passwords when replacing a sequence of 40 bytes, typical for different versions of the database. Single error on Access 97 file with non-printable characters.
The program allows you to determine the database password, the database owner - his name and identifier. Based on the workgroup file, it determines user names and their passwords. Works with database ms Access 2.0 - 2003
The easiest way to protect is to set a password to open the database (.mdb). Once the password is set, each time the database is opened, a dialog box will appear asking you to enter the password. Only those users who enter the correct password will be able to open the database. This method is fairly secure (Microsoft Access encrypts the password, so it can't be accessed by directly reading the database file), but it only works when the database is opened. Once the database is opened, all objects are available to the user (until other security types are defined, described later in this section). For a database that is shared by a small group of users or on a standalone computer, setting a password is usually sufficient.
To set a password
- Open the database file in exclusive mode. For this
- In an Access application, run the command File/Open.
- Select a database file.
- In the Open button, select the Exclusive mode.
- Execute a command on the menu Service/Protection/Set database password.
- Set a password and confirm it.
To remove the database password
- Open a file in exclusive mode
- Execute the command Service/Protection/Remove database password.
Note! Do not use a database password if you intend to replicate the database. Replicated databases cannot be synchronized if a database password is set.
Application Protection
You can protect your application from accidental or intentional damage by end users by hiding database objects in the database window. To control the appearance and behavior of an application, and to secure menus and command bars, use the application's launch options.
Hiding objects
- In the Main Database Window, select the object you want to hide.
- Click the button Properties on the toolbar - the properties window of the selected object will open.
- Check box hidden and press the button OK..
- To display all hidden objects, select the command Options on the menu Service, open the tab View and check the box hidden objects. Hidden object icons will have low contrast.
- To display hidden objects again, repeat steps 1-3, but at step 3, clear the checkbox hidden.
Hiding tables and relationships in a data schema
- Open the data schema ( Service/Data Schema).
- Right-click on the object (table image) and select the command from the context menu Hide table.
Protecting database objects at the user level
The most flexible and common way to secure a database is called user-level security. This method of protection is similar to those used in most network systems. The two main reasons for using user-level security are:
- protection of the application from damage due to inadvertent modification by users of tables, queries, forms, reports and macros on which the application depends;
- protection of confidential information in the database.
When starting Microsoft Access, the user is required to identify themselves and enter a password. Within the workgroup file, users are identified as members of the group. Microsoft Access creates two groups by default: Administrators (the "Admins" group) and Users (the "Users" group). You can also define other groups.
Although setting up user-level security for most databases is a complex task, the Security Wizard makes it quick and easy to secure an Access database. Moreover, by using common security schemes, the wizard reduces or even eliminates the need to use the Security command on the Tools menu.
After running the Security Wizard, access permissions for user and group accounts in a workgroup can be assigned and removed for the database and its existing tables, queries, forms, reports, and macros. Access permissions can also be set to be given to newly created database objects by default.
Groups and users are granted access permissions that determine whether they can access each database object. For example, members of the Users group may have permission to view, enter, or modify data in the Customers table, but they will not be allowed to change the structure of that table. The "Users" group can only be allowed to view data in the table containing information about orders, and not have access to the "Payroll" table. Members of the "Admins" group have permissions to access all database objects. You can set up a more granular control structure by creating your own group accounts, granting those groups appropriate permissions, and adding users to groups.
If the administrator group and the user group are enough for the protection system, then there is no need to create groups. You can use the standard groups "Admins" and "Users". In this case, you must assign appropriate access permissions to the default Users group and add additional administrators to the default Admins group. Each new user is automatically added to the Users group. Typical access permissions for the Users group might include Read Data and Refresh Data for tables and queries, and Open/Run for forms and reports
If you need a more extensive management structure for different user groups, you can create new groups, assign different sets of access permissions to groups, and add new users to the corresponding groups. To simplify the management of access permissions, we recommend that you only assign access permissions to groups (rather than individual users) and then add users to the appropriate groups
Note.
For more information about the Microsoft Access security system, see Microsoft Office 2000/Visual Basic Programmer's Guide.
Protection Wizard Steps
- Create a workgroup file.
- The file name is set (Secured.mdw by default), code (randomly generated by default).
- The database objects that need to be protected are marked (by default, all objects are protected). To unprotect any object, uncheck the corresponding checkbox.
- Types of groups with different access levels and their codes are assigned (randomly generated by default). The types of groups to be included in the file are marked with a flag.
- You can set some (but not all) permissions to the Users group, which is included by default in every workgroup file.
- Users are added to the workgroup file - name, password, code (randomly generated by default).
- Each of the assigned users is included in a certain group with the appropriate access level.
- Specifies the name of the backup (unprotected) copy of the database.
Protection in a multi-user environment
Securing a database in a multi-user environment has three aspects.
First, preventing users from replicating the database. Database replication allows a user to make a copy of a shared database, as well as add fields and make other changes to the current database.
Secondly, the prohibition on setting and changing the database password. If a password is set on a common database, then no one else, not knowing the password, will be able to open the database.
Third, protection against changes to launch options that define properties such as custom menus, custom toolbars, and the start form.
If the shared database does not have user-level security, it is not possible to prevent users from making such changes. The Security Wizard sets up user-level security for the database, which allows you to control access to certain tools and determine how database objects can be used. When setting user-level security, the user or group to replicate the database, set the database password, and change startup options must have the same access permission as an administrator. After running the Protection Wizard, only members of the "Admins" group of the current workgroup have administrator privileges.
If user-level security is already in place and the user or group currently has permission to access the database that matches that of an administrator, removing the permission will prevent the user or group from making changes. You can assign the appropriate access permission to a user or group to allow them to perform these tasks. It is not possible to independently manage the availability of each of the tasks.
Configuring Access DBMS Launch Options
It is possible to assign a form that will be displayed when the database is opened, disable or allow customization of toolbars or the use of context menus, and set some other launch options.
- On the Tools menu, select Launch Options.
- Select the desired options or enter the desired values.
Note.
You should not combine the setting in the launch options of the form that opens when the application starts, and the macro autoexec to open the form on startup.
Selecting Options in the Launch Options Dialog Box
- Launch options apply to the current Microsoft Access database or Microsoft Access project.
- When you select an option in the Launch Options dialog box, it automatically sets the value of the Access database or Access project property associated with that option. To view a list of these properties, click the button.
- Properties that match launch options do not override property settings for a specific toolbar, menu bar, shortcut menu, form, or report. For example, the Menu Bar and Shortcut Menu options in the Launch Options dialog box do not override property values for specific forms or reports that have a custom menu bar or shortcut menu. Therefore, when a form or report is opened, Microsoft Access displays the custom menu bar attached to that form or report, rather than the global menu bar specified in the Launch Options dialog box.
- The Launch Options dialog box can be used instead of or in addition to a macro autoexec . Macro autoexec is launched after the launch options take effect, so in the macro autoexec you should not include macros that can change startup options. For example, if a form is specified in the Form/Page Output field of the Launch Options dialog box, and the macro autoexec If the OpenForm macro is called, then the form specified in the Launch Options dialog box will be opened first, followed immediately by the form specified in the OpenForm macro.
- In an Access environment, if user-level security is defined for a database, you can prevent users from changing settings in the Launch Options dialog box. To do this, make sure that users cannot get administrator rights to access the database.
- The launch options settings can be bypassed by holding down the SHIFT key while opening the database.
Working with different versions of the Access environment
Sometimes a user creates a database in one version of Access DBMS, and then needs to view it in another version of Access DBMS (either created earlier or created later).
In doing so, the following must be taken into account:
To be able to edit the database, you need to convert the file to the required version of the Access DBMS.
Converting a database to a previous version of Access DBMS (downgrading)
- Run command Tools/Utilities/Convert Database/to a previous version of Access.
- During the conversion step, you will be prompted to enter a name for the new database.
Converting a database to a new version (upgrading)
- At the opening stage, a message will appear prompting you to select one of the options
- Convert database
- Open for viewing only.
- Select the Convert database radio button and enter a new database name and folder.
Files created in Access 2000 are opened in Access 2003 for viewing and editing.
A user account password is defined to prevent a user from connecting under another user's account. MS Access default assigns a user account Admin and any new user accounts created in the workgroup, blank passwords.
Attention! If the password is lost or forgotten, it will be impossible to recover it. Therefore, you should store it in a safe place. To gain access to the database, a user who has lost his password must contact administrator(group member Admins the workgroup in which the account and password were created) to remove the password.
For create a password the user needs:
1. Run MS Access using the workgroup in which the user account is stored, and log into it using the account for which you want to create or change the password.
2. Open the database.
3. On a tab in a group Administrator choose a team
4. Tab change Password leave the field Current Password empty if the account did not previously have a password. Otherwise, enter in the field Current Password Old Password.
5. Enter New Password in field New Password.
6. Re-enter New Password in field Confirmation and press the button OK(Fig. 11.18).
Removing a user account password
To perform this procedure, you must log in to the database using a group member account. Admins.
1. Launch MS Access using workgroup file A that stores the user account.
2. Open the database.
3. Tab Working with Tool Ribbon Databases in the group Administrator choose a team Users and Permissions - Users and Groups….
4. Tab Users enter the user account name in the field Name.
5. Press the button Remove password(Fig. 11.19).
6. Repeat steps 4 and 5 to remove other passwords, then press the button OK.
Access Permissions
Permissions- a set of attributes that define the user's rights to data or objects in the database.
There are two types access permissions:
1. Explicit - if they are directly assigned to a user account. These permissions do not affect the permissions of other users.
2. Implicit - access permissions assigned to the group account. A user included in such a group receives all the permissions granted to the group. Removing a user from this group revokes all permissions assigned to that group.
When a user attempts to perform any operation on a protected database object, their current permissions are determined by a combination of explicit and implicit access permissions. At the user level always act minimum restrictions from imposed explicit permissions for the user and for all groups to which the user belongs. Therefore, the easiest way to manage a workgroup is to create new groups and define access permissions for those groups, not individual users. After that, changing permissions for individual users is done by adding users to groups or removing them from groups. In addition, if new permissions need to be granted, they are granted to all members of the group at once in a single operation.
Change permissions of other users on individual database objects the following users can:
group members Admins defined in workgroup file, which was used when creating a particular database;
· owner object;
· any user received on this object administrator permissions.
In some cases, users who do not have permission to perform any action have the opportunity to assign them to themselves. This situation occurs for a user who is a member of the group Admins or owner object.
The user who created the table, query, form, report, or macro is owner this object. In addition, a group of users who can change permissions in the database can also change the owner of objects or re-create those objects, which is an alternative way to change the owner of objects. To create an object again, it is enough to import or export this object to another database or make a copy of the object. This technique is the simplest way to change the owner of objects, including the entire database.
Administrators and owners are essential because they are given permissions that cannot be taken away.
1. Administrators(group members Admins) can always get all permissions on objects created in the workgroup.
2. Accounts that are owners tables, queries, forms, reports, or macros can always get full permissions to access these objects.
3. An account that is owner db, can always open the db.
Because user accounts Admin are exactly the same for all instances of MS Access, then the first step in organizing a protection system is to define accounts administrator and owner(or a single account that is both an administrator and an owner account). After that, you should delete the user account Admin from the group Admins. If this is not done, any Microsoft Access user will be able to connect to the workgroup using the account Admin and to get all permissions to access tables, queries, forms, reports, and workgroup macros.
To the group Admins You are allowed to add an arbitrary number of accounts, however database owner there can be only one account - the one that was active when the database was created, or the one that was active when the owner was transferred by creating a new database and importing all objects from the original database into it. However, group accounts can own tables, queries, forms, reports, and database macros.
Only user accounts can be used to log into MS Access; signing in with a group account is not possible.
Accounts created for database users must be stored in a file of the workgroup to which users will join to work with the database. If a different workgroup file is used to create the database, it must be changed before creating the accounts.
Need to create unique passwords for accounts administrator and users. A user who connects using an administrator account will always be able to get full permissions to all tables, queries, forms, reports, and macros created in the workgroup. A user who connects using the owner account will always be able to get all permissions to access objects owned by that owner.
After creating user and group accounts, you can view and print their schemas. MS Access prints a Workgroup Accounts report showing the groups each user belongs to and all users in each group.
"Database security" here refers to a way to prevent unauthorized access to information stored in tables. Protecting the source code of forms and modules is not considered.
The relevance of this topic is extremely high. This can be judged by the first place in the rating (18 thousand hits) of the article written by Yuri Sherman. I even came across a 500 page book entirely dedicated to Access protection: Garry Robinson "Real World Microsoft Access Database Protection and Security .
Standard protection methods
Database password protection
This protection method allows you to set a password to open the database for all users. To create it, you need to open the database file in the "exclusive" mode and select the menu item Service / Protection / Set database password. To work with such a database in MS Access, you will need to enter a password. Here is an example of working with a db file using DAO or ADO.
Public Sub TestDAO()
Dim mWS As DAO.Workspace
Dim mDB As DAO.Database
Set mWS = DBEngine.Workspaces(0)
("C:\a97.mdb", True, True, ";pwd=123")
end sub
Public Sub TestADO()
CnDB.Open "Provider=Microsoft.Jet.OLEDB.4.0" & _
";Data Source=C:\a97.mdb" & _
";Jet OLEDB:Database Password=123"
end sub
This is the most unreliable way to protect databases. There are a sufficient number of free and paid utilities that display the password. Including source codes for VB code are available that allow you to read such a password. Other than that, it's not all that bad. Once I came across an original modification of this method of protection, which will be discussed below.
User password protection
This method allows you to introduce an additional level of restrictions related to the operation of the Access database. Based on the creation of a workgroup file, which defines user names, their passwords and rights to work with various database objects.
The sequence of actions to create a protected file:
- Create a new workgroup file.
To do this, the WRKGADM.EXE program is launched in 97-2000 Access, and in 2003 Access it is necessary to select the menu item "Tools / Security / Workgroup Administrator". In the administrator, click the "Create" button, specify the name, organization and group code. Specify the name and location of the file to be created. For example:
Name: test_Name
Organization: ~
Work group code: line 20 characters.
Workgroup file: C:\test\gr.mdw - Create a shortcut to launch ms Access using the created mdw file. The shortcut must contain the string: [path to MSACCESS.EXE] /WrkGrp [path to mdw file]. For example: "C:\Program Files\MSOffice2003\OFFICE11\MSACCESS.EXE" /WrkGrp C:\test\gr.mdw
- After launching Access using this shortcut, you need to open the menu item "Tools / Protection / Users and groups". In the dialog box that opens, create a new user and add it to the "Admins" group. For example, "test_User" was created with the code "987654321"
- Now you need to open Access on behalf of the created user. To do this, add the following line to the created shortcut: /user [username]. For example: "C:\Program Files\MSOffice2003\OFFICE11\MSACCESS.EXE" /WrkGrp C:\test\gr.mdw /User test_User
- Launch Access using this shortcut. Now the created user needs to be assigned a password. This is done in the same "Users and Groups" dialog. Let's say the user "test_User" is assigned the password "test_Password". Next, you need to create a new database. In this case, the owner of this database, as well as all created or imported objects (tables, queries, etc.) will be the user whose name was specified in the label.
- After the database is created, it is desirable to remove "Admin" from the "Admins" group and take away the rights to the database objects and to open the database from the "Users" group.
- Add the name of the protected database to the label. For example: "C:\Program Files\MSOffice2003\OFFICE11\MSACCESS.EXE" C:\test\db2k_test.mdb /WrkGrp C:\test\gr.mdw /User test_User /pwd test_Password
Here is an example of opening a user-level secured database using DAO or ADO
Public Sub TestDAO()
Dim mWS As DAO.Workspace
Dim mDB As DAO.Database
DBEngine.SystemDB = "C:\test\gr.mdw"
Set mWS = DBEngine.CreateWorkspace_
("", "test_User", "test_Password", dbUseJet)
Set mDB = mWS.OpenDatabase_
("C:\test\a97.mdb", True)
end sub
Public Sub TestADO()
Dim CnDB As New ADODB.Connection
CnDB.Open "Provider=Microsoft.Jet.OLEDB.4.0;" &_
"Data Source=C:\test\a97.mdb;" &_
"Jet OLEDB:System database=C:\test\gr.mdw;" &_
"User ID=test_User;" &_
"Password=test_Password;"
end sub
Removal of such protection.
Create a new database. In the shortcut, write the path to this database, the MDW file of the protected database, the name and password of the owner. Open a new database with this shortcut. Import tables into it from a protected one, and then change the owner for all database objects to Admin. In order to find out the name and password of the database owner, you can use the specialized programs described in the Access Passwords review. If the workgroup file is missing, you can restore it. To do this, you need to find out the names and identifiers of the owners of database objects. This information is contained in a database file and can be retrieved using programs such as AOPR. Using this data, a new file is created. (sequence described above)
It is not necessary to use programs that allow you to determine the password of the database or user. Often programmers do not care at all about hiding the password in the program text. Having launched a program that works with a protected database, you need to open the virtual memory of this application in the WinHex hexadecimal editor. By searching for the Unicode strings "User ID="; "Password="; "Database Password=" or "pwd=" you can find the username, password and database password.
You can completely ignore the presence of protection. To do this, you need to use AccessRecovery, which creates a new file without protection and transfers tables, queries, forms, macros, reports, and module code to it.
Non-standard methods of protection
Changing the file extension
A fairly simple way to mislead is to change the extension of the database file. Seeing an unfamiliar extension, not everyone will try to find out the nature of this file. In addition, it becomes possible to associate this extension with your program, so that when you click on the file, your application is launched, and not Access. It is advisable to open such a file with exclusive access, since in this case no ldb file will be created.
Security using a database password containing non-printable characters
First of all, this method is aimed at counteracting the definition of passwords using special programs. One base with such protection spoiled my discord well. Now I will spoil the mood of its authors by talking about this defense. The method is based on the fact that the database password of Access 2000 and 2002-2003 format is a text string in Unicode format. However, there are no restrictions on its content. The standard way to set and use a database password is to enter it from the keyboard in a dialog box. If the password string contains non-printable characters, then they will not be correctly displayed by the program that opens the passwords of the database. On the other hand, this password cannot be entered in the dialog box when opening the database in MS Access.
But I didn't forget about Access 97 either. The fact is that the database specification and the DAO 3.60 help indicate that the maximum number of characters in a password is 14. But in fact, there can be 20 of them. At the same time, Access 97 itself does not allow password strings of more than 14 characters. The Access 2003 spec also says 14 characters, but the program allows all 20 to be entered. Non-printable characters are also possible, making most password-cracking programs stupefied.
To set such a password, you will need to use a program that uses the CompactDatabase method of the ADOX or DAO libraries.
Security breach.
- First, you can use AccessRecovery .
- Secondly, you can try to determine the database password using special programs. The Access Passwords overview provides a summary table of their capabilities.
- Thirdly, you can find out the password by analyzing the program code in the debugger. Whatever the password is, it is still passed as a text string in the database open method. With some experience, this is not a very difficult task. When I first encountered such protection, I managed to find the password using the OllyDbg debugger, finding the place where ADODB.Connection was created
- You can find out or change the database password without resorting to special programs. In Access 97, a password is obtained by XORing the password with a 20-byte sequence. The values of these bytes can be obtained from any non-password protected mdb file. Starting with Access 2k, due to the use of Unicode, 40 bytes are allocated to store 20 characters of a password. Encryption also uses XOR addition, but to obtain a sequence of bytes corresponding to an empty password, you must create a file with the date of the database under study. The resulting bytes can be entered into the file under investigation and the password reset, or they can be added to similar bytes of the file under investigation and the password value obtained.
This paper does not consider possible manipulations with workgroup files. Surely there are ways to protect the passwords stored in them from too curious programs, but all this loses its meaning when using AccessRecovery, which does not notice the protection at all.
File modification protection
The protection method is based on the modification of the first bytes of the file. Thus, before opening the database, the correct header stored in the program is written to its file, and after closing the wrong header is returned. When trying to open a database file with ms Access, an error message appears. It is not bad to combine this method with changing the file extension. For example, you can take the header of a dbf file and write it to the beginning of the mdb file. Next, change the file extension to dbf and enjoy the result. The database can now be opened in Excel, Access or another program that allows reading dbf files. Here is an example of such a transformation:
"database file header modification
"Ex: Call BaseProtect("C:\01.mdb", True)
Public Sub BaseProtect(sPath As String, bLock As Boolean)
Dim iFn As Integer
iFn = FreeFile()
Open sPath For Binary Access Write As #iFn
Put #iFn, 5, CStr(IIf(bLock, _
"ProtectDataBase", "Standard Jet DB"))
Close #iFn
end sub
The method is not effective enough, since the program working with the database can be interrupted artificially and an unprotected database will remain on the disk. Therefore, it should only be used in combination with other methods.
Protection by changing the database version
This method is a further development of the idea of modifying the file header in order to counter programs that read passwords. The method is based on the fact that to work with Access 97 and 2k databases, programs use different password reading algorithms and at the same time try to independently determine the version of the mdb file.
To determine the version, you can use a sequence of 40 bytes, starting from 122 from the beginning of the file. If you enter this sequence from Access 2k into the Access 97 database, then we get an interesting result. ms Access, ADO, and DAO work fine with this file, and most password-cracking programs fall for this trick. A similar result can be obtained when transplanting a byte sequence from Access 97 to Access 2k
Access 2k file header
the fragment of the database password is highlighted in green
blue - a fragment specific to the database version
Offset 0 1 2 3 4 5 6 7 8 9 A B C D E F
00000000 00 01 00 00 53 74 61 6E 64 61 72 64 20 4A 65 74
00000010 20 44 42 00 01 00 00 00 B5 6E 03 62 60 09 C2 55
00000020 E9 A9 67 72 40 3F 00 9C 7E 9F 90 FF 85 9A 31 C5
00000030 79 BA ED 30 BC DF CC 9D 63 D9 E4 C3 9F 46 FB 8A
00000040 BC 4E 9B 6D EC 37 40 D2 9C FA DB C8 28 E6 0E 20
00000050 8A 60 49 02 7B 36 E8 E4 DF B1 6A 62 13 43 D2 39
00000060 B1 33 29 F7 79 5B 8F 23 7C 2A 4F E9 7C 99 08 1F
00000070 98 FD DC 75 0C FF D8 FD 82 66 5F 95 F8 D0 89 24
00000080 85 67 C6 1F 27 44 D2 EE CF 65 ED FF 07 C7 46 A1
00000090 78 16 0C ED E9 2D 62 D4 54 06 00 00 34 2E 30 00
Protection using an electronic key
This is another confirmation that standard protection methods, even from third-party manufacturers, are vulnerable. We are talking about HASP keys. Using the HASP Envelope utility, you can encrypt a file (in this case, a database) and allow access to it only from a protected application. The mechanism of "transparent" encryption is used. With the start of the operating system, a certain process is launched that monitors all accesses to the protected database file. If this call comes from a normal application, for example from ms Access - the file is read and a message about "unrecognized database format" is displayed. But if the application specified during encryption works with the file, then the data is transferred to it in decrypted form. As a result, the program itself is unaware of the presence of protection. Yes, the complexity of hacking such a database increases significantly. But at the same time, it must be remembered that an electronic key must be supplied with the application, with a price of N c.u. and that data access speed drops two to three times.
Security breach.
Two ways were found to get the DB its full order.
- First, the program code was vulnerable. The database was accessed using queries. From the beginning, the debugger found a query called in response to a button click in the program. Further, this request was replaced by the text of the request to create a table in another database. After clicking the button, the query fetched the table data from the secure database and saved it in another file.
- Secondly, a program was written that, using a hook, injected its code into the address space of a HASP-protected process and simply copied the database file on its behalf.
Encryption of table values
This method is not bad. In any case, there is a real hope that something can be saved. However, there are a number of limitations. Data must be decrypted before it can be displayed. There is no way to search by part of a string in an encrypted field. The encryption algorithm and the key are contained in the program, which means that there is a potential vulnerability. In this case, the reliability depends on the resistance to hacking of the program that works with the database. You can combine business with pleasure: do not encrypt, but compress the contents of memo fields. Dealing with the compression algorithm in the program code is a boring task.
Conclusion
Before raising the question of how to protect the database, you should think about its necessity. You shouldn't rely on standard methods, but that's no reason not to use Access. A specialist will hack anything, but you can make it not so easy.
The following article describes transparent encryption of Access databases, which has a number of advantages over existing methods.