You no longer need cables and flash drives to exchange files between computers and mobile gadgets. If the devices have access to the Internet, files can “fly” between them “on the cloud”. More precisely, they can "settle" in the cloud storage, which is a collection of servers scattered around the world (combined into one virtual - cloud server), where users place their data for free or for free. In the cloud, files are stored in the same way as on a computer's hard drive, but they are accessible not from one, but from different devices that are able to connect to it.
Every second or third Internet user has already adopted the cloud storage technology and uses it with pleasure, but someone is still saving themselves with flash drives. After all, not everyone knows about such an opportunity, and some simply cannot decide which service to choose and how to use it. Well, let's figure it out together.
What are cloud storage from the user's point of view and how they work
If you look at the eyes of an inexperienced user, cloud storage is a common application. All it does is create a folder on the computer under its own name. But not simple. Everything that you put into it is simultaneously copied to the same cloud-based Internet server and becomes available from other devices. The size of this folder is limited and can grow within the limits of the disk space allocated to you (on average from 2 GB).
If the cloud storage application is launched and the computer (mobile gadget) is connected to the global network, the data on the hard disk and in the cloud is synchronized in real time. When working offline, as well as when the application is not running, all changes are saved only in the local folder. When the machine is connected to the Internet, access to the storage becomes possible, including through a browser.
Files and folders uploaded to the cloud are full-fledged web objects, just like any content on Internet sites and ftp storages. You can link to them and share links with other people, even those who do not use this service. But only those to whom you yourself have allowed it can download or see an object from your repository. In the cloud, your data is hidden from prying eyes and is securely password protected.
The bulk of cloud services have additional functionality - a file viewer, built-in document editors, screenshot tools, etc. This, plus the amount of space provided, creates the main differences between them.

Is a cloud storage service that needs no introduction to Windows users. Still, after all, in the latest releases of this OS (in the "top ten"), it just climbs on top of everything on the screen, as it is set to autostart by default.
For Windows users, the advantage of the Microsoft OneDrive service over its counterparts is perhaps only one thing - it does not need to be installed. You also do not need to create a separate account for it - to enter the cloud, you just need to enter your Microsoft account information.
The owner of one account Microsoft OneDrive provides 5 GB of free disk space to store any information. To get additional volume, you will have to pay extra. The maximum is 5 TB and costs RUB 3 399 per year, but this package includes not only disk space, but also the Office 365 application (home edition). More affordable tariff plans are 1 TB (2,699 rubles per year - storage and Office 365 personal) and 50 GB (140 rubles per month - only storage).
Additional features of all tariffs:
- Supports other operating systems - Mac OS X, iOS and Android.
- View and edit documents using the built-in Office suite applications.
- Remote access to all content on the computer (not just the OneDrive folders) where the service is installed and your Microsoft account is used.
- Creation of photo albums.
- Built-in messenger (Skype).
- Create and store text notes.
- Search.
Paid versions only:
- Creation of links with a limited duration.
- Offline folders.
- Multi-page scanning with saving documents in a PDF file.
In general, the service is good, but sometimes there are problems with logging into your account. If you are going to work with the web version of the storage (through a browser) and log into it with a different IP address than before, Microsoft sometimes triggers a verification of your account ownership, which is quite time-consuming.
There have also been complaints about the removal of user-generated content from OneDrive - when Microsoft suspected it was counterfeit.

Is one of the oldest cross-platform cloud storage. Unlike the previous one, it supports all major operating systems, as well as some rarely used ones, such as Symbian and MeeGo. The service is very easy to use, fast and stable.
For free, a DropBox user is provided with only 2 GB of disk space for storing personal files, but this amount can be doubled by creating and attaching another one to your account - a work one (which can actually be personal). Together this will make 4 GB.
Switching between personal and working disk space on the DropBox website and in the application is carried out without logging out of your account (you do not need to enter your username and password each time). A separate folder is created on the computer for both accounts - 2 GB each.
DropBox, as expected, also has several tariff plans. About free it was said above, Paid is "Plus" (1 TB, $ 8.25 per month, intended for personal use), "Standard" (2 TB, $ 12.50 per month, for business), "Advanced" (unlimited volume, $ 20 per month for 1 user) and "Enterprise" (unlimited volume, individually set price). The difference between the latter two lies in the set of additional options.
In addition to storage, free users have access to:
- Document collaboration service DropBox Paper.
- Share links and create shared folders.
- File change log with the ability to restore them to a previous version (up to 30 days).
- Commenting on files - both your own and other users, if the file is available for viewing.
- Search function.
- Receive event notifications (individually configurable).
- Automatic download of photos from the camera (by the way, for enabling this option some time ago, DropBox provided users with additional space).
- Choice of full or selective synchronization.
- Data encryption during storage and transmission.
The possibilities of paid tariffs can be listed for a very long time, therefore, we will note only the main ones:
- Remotely wipe data from DropBox on a lost or stolen device.
- Link expiration date.
- Two-factor account authentication.
- Setting access levels to different data.
- Enhanced protection of information class HIPAA / HITECH (safe storage of medical records).
- 24/7 technical support.
DropBox is, if not the best, then a very decent service. Despite the small volume of free space by today's standards, it is used by millions of people around the world.
Mega (Megasynk)

As it is clear from the description, Amazon Web Services is focused only on the corporate sector and is not intended to store albums with photos of cats, although it is possible that someone uses it for this as well. After all, cloud storage of files - Amazon Glacier, like Yandex disk, provides users with 10 free GB. Additional storage costs $ 0.004 per GB per month.
Comparing Amazon Glacier with the web resources described above is perhaps incorrect, since they have slightly different purposes. The functionality and capabilities of this service are determined by business objectives, including:
- Uninterrupted operation, increased reliability.
- Compliance with enhanced data protection standards.
- Multilingual interface.
- Unlimited volume (additional charge extension).
- Ease of use and flexibility of settings.
- Integration with other Amazon Web Services.
Those interested in Amazon's capabilities can check out the full AWS product documentation on the official website.
Mail.ru

It takes the second or third place in the popularity rating of web file storage among the Russian-speaking audience. In terms of the set of features, it is comparable to Google Drive and Yandex Disk: it, like them, contains web applications for creating and editing documents (texts, tables, presentations) and a screenshoter (a utility for taking screenshots). It is also integrated with other Mail.ru projects - mail, social networks "My World" and "Odnoklassniki", the service "Mail. Dating ”, etc., has a convenient file viewer with a flash player and is also quite affordable (for those who do not have enough allocated space).
The free disk space of the Mail cloud is 8 GB (previously, this figure has changed several times). The premium rate for 64 GB costs 690 rubles per year. For 128 GB you will have to pay 1,490 rubles per year, for 256 GB - 2,290 rubles per year. The maximum volume is 512 GB, it will cost 3,790 rubles per year.
Other functions of the service are not much different from similar ones. This:
- Shared folders.
- Synchronization.
- Built-in search.
- The ability to share links.
The Mail.ru client application runs on Windows, OS X, iOS and Android.

Cloud storage is a proprietary web service for owners of smartphones and tablets from the same manufacturer. Designed to store backup copies of data from mobile devices - multimedia content, OS files and other things at the user's discretion.
The Samsung Cloud client app is pre-installed on phones and tablets released after the second half of 2016 (more precisely, after the release of the Samsung Galaxy Note 7). Registration of an account on the service is possible only through it, apparently, to filter out strangers.
Free storage is 15 GB. An additional 50 GB costs $ 0.99 per month, and 200 GB costs $ 2.99.
iCloud (Apple)

- the favorite among cloud data storage users of Apple products. Still, because it is free (though not very roomy) and is integrated with other apple services. The service is designed to store backup copies of data from iPhone, iPad and iPod, as well as user media files, mail and documents (the latter are automatically synchronized with the contents of iCloud Drive).
Free iCloud storage capacity is 5GB. Additional storage is priced at $ 0.99 for 50GB, $ 2.99 for 200GB, and $ 9.99 for 2TB.
The iCloud client application supports Mac OS X, iOS, and Windows operating systems. An official application for Android has not been developed, but owners of devices based on this OS can view mail from the Apple cloud on their device.

Chinese service completes the top parade of cloud storage. As you can see from the screenshot, it is clearly not adapted for us. Why is it needed then, if there are Russian, European and American analogues that are more familiar to a Russian-speaking person? The point is, Baidu gives users a terabyte of free disk space. For this, it is worth overcoming translation difficulties and other obstacles.
Signing up for Baidu Cloud is significantly more time consuming than the competition. It requires confirmation with a code sent via SMS, and no SMS from a Chinese server arrives at Russian, Belarusian and Ukrainian numbers. Our fellow citizens have to get out by renting a virtual phone number, but that's not all. The second difficulty is that the account cannot be registered to some email addresses. In particular, on services gmail (Google is blocked in China), fastmail and Yandex. And the third difficulty is the need to install the Baidu Cloud mobile application on a phone or tablet, since this is exactly what 1 TB is given (when registering on a computer, you will receive only 5 GB). And it, as you know, is completely in Chinese.
Aren't you scared? Go for it - and you will be rewarded. Information on how to create an account on Baidu with your own hands is on the Internet.
In this regard, we decided to turn to experts in the field of information security and cloud technologies to understand whether cloud storage can replace physical media, how secure such services are, and how users can protect their information placed in the "cloud".
"Is cloud storage the future?" Will cloud storage completely replace physical storage media?
Alexey Fedorov, director of the recommendation system for cloud services Startpack :
“In applications like working with documents, cloud storage will really replace physical media. This is the model used by Google and Microsoft in Google Drive and OneDrive, respectively. Cloud storages Dropbox, Yandex Disk, Cloud Mail.Ru initially did not have the ability to work with documents, but they introduced such an opportunity. Combining working with documents and storing them is so natural that back in 2005, Box repository positioned itself "like SharePoint, only better." Six years of the existence of the Chromebook - a laptop with nothing but a browser - also shows that the model has a right to exist. At the same time, there are applied tasks for which storing files in the "cloud" is impractical: video processing, working with sound, engineering design. Most games assume that the user has a computer with a large hard drive. Even to run a remote desktop, a thin client must have some basic functionality in place.

Alexey Shipov, Head of ICL Cloud Platform Development at ICL Services
Alexey Shipov, Head of Cloud Platform Development ICL Cloud in company ICL Services :
“We are now seeing an explosive growth in the use of cloud storage for data generated on social media. After all, many photos and videos taken on a smartphone automatically go to the "cloud". The use of the cloud for business data is growing at a slightly slower rate, but steadily at 30-50% each year. See how Microsoft is building Windows Server with fast data migration capabilities to the Azure public cloud. The same trends can be seen among other vendors. Probably, in 5-10 years more than half of the data will be stored in the "cloud". However, for especially valuable and important information, local storage using the most modern means of protection, for example, quantum encryption, will not lose its relevance. "

Denis Polyansky, Head of Virtualization and Cloud Platform Protection, Security Code
Denis Polyansky, head of the protection of virtualization and cloud platforms of the company "Security code" :
“Cloud storage has many benefits: high availability, scalability, and so on. And they will continue to gain popularity in the short term. But there are a number of aspects that make the cloud model difficult to apply in some cases. For example, the impossibility of obtaining the consent of the subjects for the transfer of personal data to the side of the provider or the unwillingness of the customer to transfer a certain type of data to the side (client bases, financial systems). The problem can also arise if there are problems with the network connection on the client side, but you need to continue working (locally). Therefore, in the near future, cloud services will not completely replace local data processing. The most popular and promising model today is the so-called "hybrid clouds", which combine the advantages of cloud services and local storage and processing of data. "Clouds" have proved to be good for backup storage of information in case of problems in the local infrastructure. "

Rustem Khairetdinov "Attack Killer"
Rustem Khairetdinov, CEO of the company "Attack Killer" :
“Of course, there will not be a complete replacement, at least in the foreseeable future. For a hundred years, mankind has not learned how to provide people with electricity with a 100% guarantee, every now and then there are cliffs and "blackouts" due to natural phenomena and man-made disasters, what can we say about cloud services. There is information that today is more convenient to store in the "clouds" - these are "heavy", not often needed and at the same time rarely changing files, for example - films, music, photographs. But for them it would be good for them to have a physical backup copy, especially if such information is made by you and exists in a single copy. For data that is needed constantly and at the same time it is constantly changing, while it is better to use an on-site or at least a hybrid architecture - to store data both in the "cloud" and at home. "

How secure are cloud services?
Alexey Fedorov:
“The dangers of using cloud storage can be divided into two types: information loss and information leakage. Loss of information is now impossible in almost any cloud storage, since information is repeatedly copied and stored on different servers and in different data centers. For example, for Google to lose a user's files, two continents must disappear overnight. However, domestic cloud storage at the dawn of its appearance had precedents with the loss of user data. Some storages, according to the terms of the user agreement, delete data if the user has not used it for several months. Usually, to enter the cloud storage, you need a username and password, if an attacker finds out this data, he can get access to the stored files. This is how personal iCloud photos of celebrities were leaked. "

Andrey Rybin, head of the information security sector of the Department of Information Technologies (DIT) of the city of Moscow
Andrey Rybin, Head of the Information Security Sector Department of Information Technology (DIT) cities Moscow:
“Using cloud services is not secure. The main threats to information security when using cloud technologies are: theft and loss of data, hacking of accounts, vulnerabilities in interfaces and APIs, DDoS attacks, actions of insiders, the possibility of hackers penetrating, as well as simple negligence of the provider. In addition, there are additional threats associated with the use of virtual infrastructure - the dynamism of virtual machines, attacks on the hypervisor as a key element of the virtualization system, attacks on control systems. "

Csaba Krasnai, IT Evangelist, Balabit
Chaba Krasnai, IT evangelist of the company Balabit :
“For many companies, mainly SMEs, the cloud is more secure than their own infrastructure. Cloud providers have the necessary expertise and workforce to ensure security. In large companies, it depends on the information that needs to be managed. Organizations are moving towards hybrid "clouds", some business processes use public "clouds", while others remain within the internal infrastructure. To determine the security level of cloud services, a risk assessment is needed. Many solutions help secure hybrid infrastructure, such as PAM tools that monitor and track the activity of administrators in a networked environment. "

Vladimir Fomenko, head of the hosting company King Servers
Vladimir Fomenko, head of a hosting company King Servers :
“Cloud services are clearly better protected from technical failures due to several factors:
- For storage, specialized "hardware" is used, the probability of failure of which is much lower than that of conventional home appliances.
- The equipment of such services is located in specialized data centers, where it is protected from voltage surges and overheating.
- Naturally, backup technologies are used to store data, which will save data in the event of equipment failure.
From the point of view of information security, such services are reliable enough that only an authorized account owner could access the data.
The only vulnerability will be insufficient concern for security on the part of the user himself, such as setting a simple password or connecting to the storage from untrusted devices. From the point of view of the reliability of the services themselves, if the user is interested in the safety of data, then I highly recommend using large services and not relying on startups that provide more space on free accounts. Quite possiblethat for small companies the provision of such services will be unprofitable, and they will close after a while, as was the case with the vSeife and Copy services. In such a case, you may not have time to download your data back, and they will be lost. "

Artem Marusov, expert of the Information Security Center of Jet Infosystems
Artem Marusov, expert of the Information Security Center of the company Jet Infosystems:
“How secure are cloud services? Unfortunately, there is no definite answer to this question. And even the professional community cannot come to a common opinion on this matter. It is enough to look through the profile sites and forums to understand that a lot of ambivalent opinions have already been expressed (and continue to be expressed) on the topic, and quite well reasoned ones. Supporters of cloud services believe that since such services are provided, as a rule, by large corporations with serious IT and information security competencies, then security is provided by them, if not the highest, then at a sufficiently adequate level. Opponents of the "clouds" do not stop listing the facts of large data leaks from cloud services, recalling that using them, we, in fact, give our data to a kind of "black box", the implementation aspects of which are unknown to us and, accordingly, cannot be estimated adequately. Personally, I believe that it is necessary to accept the fact that no one can provide a 100% guarantee of protection against leaks. In this regard, you just need to take it as a rule:
1) Never upload information in the open form to cloud services, the leakage of which is undesirable for you (work and financial documents, personal files).
2) If such a need cannot be avoided, then be sure to encrypt files before sending them to the "cloud". To do this, you can use both simple tools (for example, creating password-protected archives), and more advanced (software for creating encrypted partitions). "

How can users ensure the security of their information in the cloud?

Ashot Hovhannisyan, CTO and Founder of DeviceLock
Ashot Hovhannisyan, CTO & Founder DeviceLock :
“First of all, you need to use two-factor authentication (2FA) to access cloud services. It is highly recommended to store files on such services in protected containers (at least in password-protected archives). Organizations actively using cloud storage for storing and exchanging information need to regularly scan their data stored in the cloud using Data Discovery products to identify those data that got into cloud storage by accident or in violation of company policies. "
Alexey Fedorov:
“If the data is extremely valuable, it’s better not to rely on one store and send it to another store. It should be remembered that if a cloud storage client application is installed on the device, when files on the disk are damaged by a virus, the corrupted files will also be loaded into the storage, replacing the uncorrupted ones. And even if the storage allows you to roll back to previous versions, it will be quite problematic to fix the corruption: you will have to restore each file separately, the depth of the stored versions may not be enough. Therefore, it is better to upload files to at least one repository through a browser without installing the client application. Of course, you should come up with a complex password for your account: 10 or more characters, letters in different case, numbers and special characters. Store the password in the password container or remember. "

Denis Sukhovey, Head of Technology Development Department, Aladdin R.D.
Denis Sukhovey, head of the technology development department of the company "Aladdin R.D." :
“Today users have the opportunity to use an impressive arsenal of organizational and technical measures to ensure the protection of information in the cloud. However, this approach negates all the benefits of the cloud itself, as it increases the total cost of using the service. In this light, cryptographic protection of confidential information in the "cloud" is the only option. Data encryption solves a whole bunch of cloud-based security problems at once, including countering leaks of important and business-critical information, differentiating access rights, meeting a whole set of requirements of regulatory organizations, and, of course, cost-effectiveness and ease of solution. "

Maxim Zakharenko, General Director of the company "Oblakoteka"
Maxim Zakharenko, CEO of the company "Cloud" :
“It is possible to ensure almost absolute confidentiality if data is transferred to the“ cloud ”and stored there in encrypted form, and decryption occurs only on its own hardware. Another thing is that it is very inconvenient and in fact it is rarely practiced, especially when it comes to private users. As soon as the decrypted data is placed in the "cloud", of course, security is significantly reduced, but the question is how relevant this security is, for example, for vacation photos or for a small individual entrepreneur who has nothing to "hide" even from the tax authorities. "
Thus, against the background of the growing role of cloud services, users need to be more responsible in placing their information in the "cloud". Of course, it cannot be ruled out that you may encounter the provider's negligence, but we must not forget that the user himself must protect his data. Therefore, we join the experts and strongly recommend using the two-factor authentication mechanism, setting strong passwords and differentiating information storage (use several different storages and pay attention to hybrid "clouds").
Cloud storage technologies are now considered a must-have tool for the modern Internet user. Each of them has an account on one of the cloud drives: Google Drive, Yandex.Disk or Mail.ru. Most have at least two of these services. In this article, we will look at the main network file storage services, ways to increase disk space on them, and provide tips for their effective and safe use.
What is cloud storage
Local drives and memory cards are physically connected to our computer or tablet with wires. Network drives are physically located in special server centers, where a stable power supply and a comfortable temperature regime for operation are ensured. The local computer maintains connection with them via the Internet. When you enter your cloud drive through a browser or mobile client application, the system displays a list of files on the server. When a user transfers a file from the local My Documents folder to the Cloud Storage, the document is physically copied over the Internet and sent to the server.
Therefore, even after the physical destruction of the phone or computer, the files will remain intact. They can be viewed through a web browser on any computer or tablet.
To assess the popularity of disk storages, it is enough to cite one fact of statistics. As of 2014, the most popular cloud was Google Drive. The storage works by default on all Android devices, except for Chinese ones, where access to Google is limited. Its users were 240 million people.
What you can use Cloud Disk for
The main tasks solved by users using network storages:
Developers are constantly improving the security system of their services. The standard today is the storage of user files in encrypted form. Without a special key, this is a useless set of bytes.
Service security should not be overestimated. In 2011, the reputable company IDC published its report, where it assesses the level of their secrecy and resistance to hacking as unsatisfactory. Experts recommended strengthening the level of authorization and encrypting files at the storage location and in transit. Most of the developers followed the recommendations and made changes to their applications.
Logging into the Cloud Storage can be protected by two-factor authorization: specifying a password and confirming the login using your phone. But for most users, one password is enough.
When compiling this rating, the company's experts took into account technological solutions to ensure the security of user data and the presence of service failures in the past. Considering that all storages presented in the diagram have been operating for more than 5 years, the history of statistics of failure situations is comparable.
- The safest was recognized OneDrive... Experts added to the advantages of the service innovative security system when the keys to encrypted files and the data themselves are stored on separate servers. By gaining access to only one of these arrays, an attacker will not be able to gain benefits. As a reminder, OneDrive is targeted at the enterprise market and is the default drive when you subscribe to Office365. Subscribers are allocated up to 100 GB immediately, while free users get only 6 GB.
- Named second in terms of safety iCloud Drive... This cloud serves users of the apple ecosystem: iPhone, MacBook and other corporate solutions of the corporation. Data encryption is performed here both during storage and in transit. Overall, the storage is reliable and comparable to OneDrive in terms of security, but earned a negative point for failure in 2014. Many users were attracted to this scandal. Private photos of the stars, stored on their iPhone, have gone online. if you use Apple technology, then you cannot do without a branded cloud. It backs up data and system settings of the phone and laptop. With its help, deleted photos and documents are recovered.
- Third place is given Google drive... Reason - insufficiently high degree of security when storing files ... When transferring data to the server and to the client device, the traffic is encrypted. In the pluses of the cloud, experts have included two-factor authorization with password confirmation via SMS to the phone number specified during registration. Experts note that in business accounts designed for corporations, Google Drive provides an increased level of security, comparable to OneDrive. It is recommended for ordinary users to encrypt confidential data on their own. For example, archive them with a password.
- The fourth place belongs to the Russian Yandex.Disk... Experts attributed a wide range of authorization methods to the security advantages of this cloud, including TouchID, pin-code and QR-code. An important advantage for ordinary users is scanning files for viruses ... The transfer channel at the Yandex storage is encrypted, like those of competitors. The only serious failure is considered to be an error in the client program of the service for Windows, made by the company's programmers in 2013. Users did not remain in the loser. They were allocated 200 GB of disk space for unlimited free use as compensation.
- The fifth place belongs to the old-timer of the market - Dropbox... The lack of his security is no client side encryption ... In theory, this allows an attacker to intercept data as it travels from a local device to a server. In 2011, the DropBox service crashed. It lasted only 4 hours. During this period of time, it was possible to access the entire storage, and not just the data area of a particular user. But note that in 2011 there were simply no other competitors from the ranking. DropBox was a pioneer in network storage and was error-prone.
How to get more free cloud storage space
All cloud storage is commercial. Their main task is to earn the money required to cover the costs of supporting the development team and developing the server infrastructure. Therefore, a limited amount of space is provided for free to users. To get additional free space for storing photos and documents, you will need to fulfill certain conditions of the service or participate in promotions.
For instance. Yandex.Disk offers 32 gigabytes of free space. autoloading photos on a mobile device.
Other cloud services also offer space expansion options for free:
- For inviting friends.
- For installing a cloud disk mobile application or program on a computer.
- Students and teachers for providing a photograph of a student card or a pass to the university. Yandex.Disk allocates an additional 32 free gigabytes for this promotion.
Also, cloud file storage services provide free space through an affiliate scheme. For example, when buying laptops or tablets of a particular brand.
A universal way to multiply your cloud storage space for free is to create multiple accounts.
How to install a cloud drive on a computer
Three network storages are most suitable for a computer:
- Google Drive. It is chosen by active users of GMail services and a powerful Internet document and spreadsheet editor - Google Docs.
- Yandex.Disk. A good choice when you don't need to use Google services. This is a reliable Russian cloud drive, for which you can easily get up to 42 GB or more free space by turning on auto-upload of photos on your mobile device.
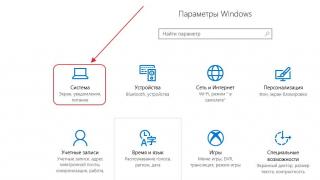
- OneDrive. Users of computers and laptops with Windows 10 operating system receive support for this network drive "on load". If you have a Windows account, 5 GB of space is allocated on OneDrive. In the shortcut This computer creates a folder of the same name, synchronized with the cloud.
Installation of the program on a computer is required only for the first two services. OneDrive support is implemented at the system level. Here is a step-by-step guide to installing the application using Yandex.Disk as an example.
Every modern smartphone out of the box includes support for at least one cloud storage.
- Apple phones come with iCloud support for backing up settings, system files, and syncing photos. Additionally, you can connect the Yandex storage using the program downloaded and installed from the official Apple application store.
- Samsung phones include support for two clouds at once: the branded Samsung Cloud and Google Drive. The owners of smartphones of this brand have a Google account as Android users and a Samsung account for the manufacturer's branded services.
- Xiaomi phones out of the box communicate with Xiaomi's own MiCloud. Everything works by analogy with the iPhone: backups are made to the storage on the network and photos from the camera are sent.
- Windows Phone smartphones come with OneDrive access enabled. With an Office365 subscription, the available storage increases by 100 GB.
- Android smartphones from other manufacturers support one cloud storage - Google Drive.
You can purchase additional space by fulfilling the requirements of the services' promotions or by purchasing it for money.
Please note that Android smartphones support Google Drive, but you will need to install separate mobile apps to work with Google Docs and Sheets. There is also a client program from Google Drive for easy navigation through the network storage. The latter is most often preinstalled on the phone.
If the capabilities of the pre-installed NAS are not enough for you, install a third-party one. The most popular are Yandex.Disk, DropBox, Mail.ru.
We will show the installation of the application for them using Yandex Drive as an example.

Come up with a strong password. Your private photos and videos are more likely to leak online if you come up with a simple password. A complex one can be generated using a special program or you can invent it yourself according to the following algorithm:! -! 123HELLO-WoRlD123! - !. This combination is easy to remember, but very difficult to crack with a password.
Encrypt sensitive data before uploading it to the network. It is dangerous to store passwords and account keys in clear text. If there is no dedicated encryption software, please zip confidential files with a password before sending them to the network.
Use double authorization. A number of network attached storages support double authorization. You need to enter the password and confirm the entry by sending the code from the SMS sent by the service. This procedure seems less convenient, but provides more data protection.
History of cloud storage technologies
The phrase "cloud technologies" was first used in 1997. The new global global network required a new computing paradigm. Professor Ramnath Chellup of the University of Texas proposed a move to cloud computing as an alternative to increasing the power of local computing.
Real developments in terms of sharing resources on the network date back to 2000. We owe the commercial launch of the service on the new cloud-based operating system to Amazon. This happened in 2002.
Google has pioneered the implementation and development of browser-based cloud applications. The new technology has been launched on the market since 2009.
The idea of creating a cloud storage on the Internet is described by its inventor Drew Houston as follows. The guy was sitting on the bus from Boston to New York, with a laptop, but no flash drive left at home. To overcome the misfortune, he began to think about accessing files wirelessly and came up with an application that implements this idea. The first DropBox code was written, according to this version of events, right on the bus.
According to the founder of DropBox, Steve Jobs wanted to acquire the project at the startup stage, but was refused. Today the company is worth approximately US $ 4 billion.
All subsequent network storages: iCloud, Google and Yandex, appeared much later. Their main promotion paradigm is the conditional free service. The user receives part of the gigabytes immediately, free of charge and unconditionally. The rest must be purchased by subscription.
Modern cloud storage has become not only a place for storing information, but also offers a number of technological solutions for collaborating on files for people living in different parts of the world. On the most popular tasks solved with their help, below.
Complain about content
Copyright infringement Spam Inappropriate content Broken links
Many cloud storage services offer very lucrative subscription plans, but are they secure? In this article, I decided to answer this question.
At the very beginning of this article, I would like to provide you with a summary of the research I have done. The table below summarizes the current security offerings of the 5 cloud storage providers I have selected.
Below is my experience with these cloud storages, as well as information collected by me from expert sources. This article looks at the security features offered by these online storage companies in order to determine which ISP is the safest. First, we will look at the security features of each individual provider, and at the end we will summarize the results.
Google drive
The web giant Google provides many great features in its cloud storage. Google provides 15GB of free cloud storage for Gmail, Docs, Google+ Photos, and Drive users. So you should use Google Drive more efficiently, as this size is spread across several services. Google says it's safe to store data with them. Even if your computer, tablet or phone fails, the data on Google Drive is safe. The company also claims that the files stored in their data center cannot disappear.
But what security does Google offer at the consumer level? What can a consumer do to protect their online data? To answer this question, we need to get inside the Google Drive security tools.
To use Drive, you need a Google account. Signing up for a Google account is as easy as shelling pears. Google will prompt you for a strong password. The password must be at least 8 characters long. However, there are no requirements for case-sensitive or miscellaneous letters and numbers when registering with Google. It could improve security though.
Protecting your Google account is a key step in keeping your Drive safe. Google suggests two-step verification(two-factor authentication) in order to increase the reliability of the account. Once you activate this feature, each time you log into any of the Google services, you will need to enter an additional code. After entering the correct username and password on your Google account page, you will receive an SMS with a verification code to your mobile phone. You will only be able to log into Google after entering this code. Thus, two-step authentication can make Google Drive more secure from hackers. You can also receive such codes using smartphone apps.
The Google account has a security question and the ability to enter an email address or phone number to recover the account, as well as allow you to regain control of your account in the event of a breach. You also control the apps that you log into with your account. The browsing history, IP address and device data are also available so you can track the activity on your Google account.
Encryption is vital for any cloud service. Although Google Drive uses HTTPS in operation, it does not provide its own file encryption service. So if you want to encrypt your files, do so before sending them to Google Drive. You can use Boxcryptor for free to secure your cloud files.
Google Drive offers a range of personalized sharing options. Using these settings, you can define who can access your files, who can upload them, edit them, and more. You can view versions of files on Google Drive. So if you need a previous version, you can get it by right-clicking on the required file and selecting the ‘Version control’ option.
In conclusion, the security of Google's online storage service depends on the security of your Google account. If you can protect your Gmail ID account, then you can safely count on the reliable protection of your files on Google Drive.
Microsoft OneDrive
Dropbox
Dropbox is one of the most popular online storage providers. It is used for both personal and commercial purposes. Dropbox is purely cloud storage. So all their forces are concentrated on the cloud. Dropbox offers new users 2GB of free cloud storage. You can increase this volume with a new customer acquisition program.
Dropbox says data security is their top priority. When I signed up for Dropbox, I noticed that the process is pretty simple and quick. I was required to enter a name, email address and password. The account creation page prompted me to use a strong password. However, there was no obligation to maintain a certain level of security. Next to the password entry field, only its strength was indicated: 'weak ... reliable'.
However, a Dropbox subscription may not require immediate email verification, but you must verify your email in order to seamlessly share files. All these options will be available to you as you use the service.
Dropbox offers a file revision feature so you can quickly revert to an older version of the files you need. If you edited a file and later wanted to get its previous version, just right-click on the new version of the file and select the "Previous Versions" option in the context menu.
Your Dropbox account comes with a range of additional security features. You can use two-step verification, which requires you to enter a unique code each time you log into Dropbox. You will receive this code on your mobile phone. You can also get the code via the smartphone app. In any case, two-factor authentication can significantly increase the security level of your account.
On the Dropbox Security Settings page, you can also monitor and manage connected devices, browsing history, linked apps, and more to prevent unauthorized access.
Dropbox uses an HTTPS connection on its site and when transferring your data between you and the cloud storage. You can control access to your files using data exchange options.
Dropbox itself does not provide an option to encrypt files prior to uploading them to their server. Dropbox assures that they encrypt files during transfer and during the rest of the time. However, you can encrypt your files before sending them to Dropbox. There are a variety of tools for this. Boxcryptor is one of them. It uses industry-standard "AES-256 bit" encryption technology to further enhance the security of your files.
Copy
Copy is one of the most popular cloud storage services competing with Dropbox, Google Drive, OneDrive, and more. Copy gives every new user 15GB of free cloud storage. The service also offers a new customer acquisition bonus with which existing users can increase their free space. The registration process for Copy takes only a few seconds. You will be asked for your name, email address and password. During the registration process for Copy, I was not prompted to choose a strong password. All that has been indicated regarding the password is that it must be at least 6 characters long.
Mega
Now let's move on to the Mega service, which is known for its privacy. Mega was founded by Kim Dotcom. The service provides each new user with 50 GB of free space. To register with Mega, you need to provide basic information such as name, email address, password, etc. Mega requires you to use a strong password. If your password is not strong enough, you will receive the following message: 'Your password is not strong enough to continue'.
Mega uses HTTPS connection and client side encryption technology. This means that your locally encrypted information will be sent to Mega. When downloading information from the service, it is decrypted. As stated on the Mega security help page, your files cannot be read on the server. The company strongly recommends not to lose your password. The Mega password is not only a password, but a code that unlocks your master decryption key. Mega claims that it is impossible to recover the password on the service. If you do not have a backup copy of your main decryption key and you lose your password, then you will also lose all data stored on the service server. So grab your Mega Master Key from this Mega link and keep it in a safe place. It is very important.
However, there are reports that there are certain weaknesses in Mega's browser-based encryption system.
Mega offers excellent security features, but unfortunately, the service does not have a file version history. You can simply recover deleted files using the ‘SyncDebris’ application from the Sync Client, or from the ‘Rubbish Bin’ folder on Mega. To monitor your activity, Mega provides a visit log option and an application management option.
Interestingly, Mega does not have a two-step verification option that would greatly improve the service's privacy and security efforts.
Conclusion
In this article, I tried to take a closer look at the security tools available from 5 popular cloud storage providers such as Google Drive, OneDrive, Dropbox, Copy, and Mega. When it comes to security, they all have their own special offers. Now let's take a look at the basic security features these services offer. Below is an easy-to-read checklist.
- Password strength requirement: Google, Microsoft and Mega all require a strong password. Dropbox and Copy are more flexible in this regard.
- Email verification requirement: All services sooner or later require you to verify your email address.
- Two-step verification: Google Drive, OneDrive, and Dropbox provide two-step verification. Copy and Mega do not provide this option at the moment.
- Client side encryption: Only Mega offers client-side encryption. This is done from the device from which the files are downloaded.
- Server side encryption: Dropbox, Mega and Copy keep your files encrypted on servers. You can use local encryption to avoid risks.
- Using a secure connection (HTTPS): All five providers use a secure HTTPS connection. However, Mega gives users the option to turn it off (optional).
- Using security questions to verify users: Google Drive has this option available. OneDrive, Dropbox, Copy and Mega do not use the secret question at this time.
From the above, it is clear that Google Drive provides almost all security features other than encryption. Microsoft OneDrive and Dropbox are close behind. Mega provides sophisticated security such as encryption, but the service lacks two-step verification. Copy needs to work to transform great cloud storage into a more secure environment through two-step verification, password strength requirements, and other innovative security systems.
Hope you found this article helpful when looking for a secure cloud storage provider. For even more tips and tricks, stay tuned. Thank you for attention. May safety be with you!