Operating system security analysis tools
Tools of this class are designed to check the operating system settings that affect its security. These settings include: About user accounts (account), for example, password length and expiration date; About the rights of users to access critical system files; Vulnerable ...(Protection of computer information)
Basic approaches to building secure operating systems
There are two main approaches to building secure operating systems - fragmented and complex. With a fragmented approach, protection is first organized against one threat, then against another, etc. An example of a fragmented approach is a situation where an unprotected operating room is taken as a basis ...(Protection in operating systems)
APPROACHES TO BUILDING PRODUCTION FUNCTIONS
SET OF ACHIEVEMENT METHOD In work for analysis mathematical model with exogenous variables, which in in this case we will consider controls, some aggregated variables are considered, which are indicators of the functioning of the system under study. Since the relationship of indicators ...(Mathematical Methods economic dynamics)
Protected operating system concept
Basic definitions We will call an operating system protected if it provides means of protection against the main threats to the confidentiality, integrity and availability of information, updated taking into account the peculiarities of the operation of this a specific instance operating system ....(Protection in operating systems)
Operating system security standards
Threat analysis, which begins the formation of a security policy, is a very laborious and difficult to formalize procedure. As a rule, the threats against which it is supposed to protect a computer system or network are very heterogeneous, compare them with each other and single out the most dangerous among them ...(Protection in operating systems)
Linux distributions can be divided into different categories, depending on the purpose and intended target group... Servers, training, games and multimedia are some of the popular categories of Linux distributions.
For users who are concerned about security, there are several distributions that are designed to enhanced protection privacy. These assemblies ensure that your surfing activity is not tracked.
However, our selection includes not only distributions with an emphasis on privacy, but also distributions for intrusion testing. These assemblies are specifically designed to analyze and evaluate system and network security and contain wide range specialized tools for testing systems for potential vulnerabilities.

An Ubuntu-based distribution designed for intrusion testing. By using XFCE as the default window manager, it is very fast.
Repositories software solutions are constantly updated to ensure that the user is always dealing with the latest versions of built-in tools that allow you to perform web application analysis, stress tests, assessing potential vulnerabilities, privileges and much more.
Unlike other distributions that include a large set of various applications The backbox does not contain this redundancy. Here you will find only best tools for each individual task or goal. All tools are sorted into categories, making them easy to find.
Wikipedia presents short overviews many built-in tools. Although Backbox was originally created purely for testing purposes, the distribution also supports the Tor network to help hide your digital presence.
Kali
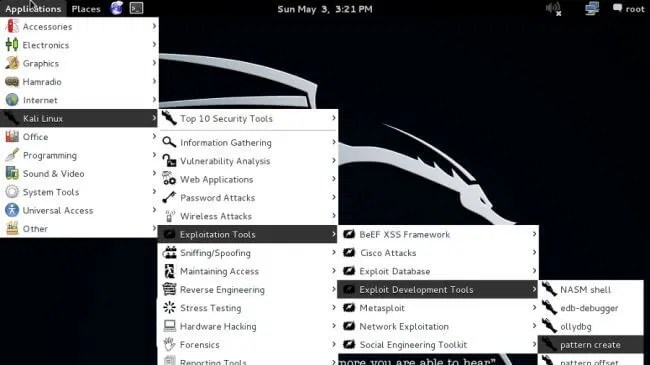
Probably the most popular distribution for penetration testing, based on Debian Wheezy. developed by Offensive Security Ltd and is a continuation of the earlier BackTrack Linux project.
Kali is available as 32-bit and 64-bit ISO images that can be burned to a USB stick or CD, or even installed on a hard drive or solid state drive... The project also supports ARM architecture and can even run on a single board Raspberry computer Pi, and also includes a huge number of analysis and testing tools. The main desktop is Gnome, but Kali allows you to create a personalized ISO with a different desktop environment. This highly customizable distribution allows users to even modify and rebuild the Linux kernel to meet specific requirements.
The popularity of Kali can be judged by the fact that the system is a compatible and supported platform for the MetaSpoilt Framework - powerful tool that allows you to develop and execute exploit code on a remote computer.

Available for 32-bit and 64-bit machines, this is an intrusion testing distribution based on Gentoo Linux. Gentoo users can optionally install Pentoo, which will install over the main system. The distribution is based on XFCE and supports saving changes, so if you unplug the USB drive, all applied changes will be saved for future sessions.
The built-in tools are divided into 15 different categories such as Exploit, Fingerprint, Cracker, Database, Scanner, etc. Based on Gentoo, the distribution inherits a set of Gentoo security features that allow additional security settings and more granular control over the distribution. You can use the Application Finder utility to quickly locate applications in different categories.
Since the distribution is based on Gentoo, some manipulation will be required to get the network card and other hardware components to work. At boot, select the check option and configure all your devices.

Based on Ubuntu, this distribution is designed for intrusion detection and network security monitoring. Unlike other penetration testing distributions, which are more offensive in nature, it is a more defensive system.
However, the project includes a large number of offensive tools found in other distributions for penetration testing; and network monitoring tools such as the Wireshark packet sniffer and the Suricata intrusion detection utility.
Security Onion is built around XFCE and includes all the most required applications available in Xubuntu. Security Onion is not intended for hobbyists, but rather for experienced professionals who have a certain level of knowledge in network monitoring and intrusion prevention. Fortunately, the project is constantly accompanied by detailed tutorials and video tutorials to help you work with complex firmware.
Caine

The default account is root: blackarch. BlackArch is over 4 gigabytes in size and comes with several different window managers including Fluxbox, Openbox, Awesome.
Unlike other penetration testing distributions, BlackArch can also be used as a tool increased confidentiality... In addition to various analysis, monitoring and testing tools, the distribution also includes anti-tracking tools, in particular sswap and ropeadope for securely erasing the contents of the paging file and system logs, respectively, and many other programs to ensure privacy.

Developed by the Italian IT security and programming network Frozenbox, based on Debian, can be used for intrusion testing and privacy maintenance. Like BlackArch, Parrot Security OS is a rolling release distribution. The default login for a Live session is root: toor.
The Live image that you install offers several boot options, such as persistent mode or persistent mode with encrypted data. In addition to analytical tools, the distribution includes several programs for anonymity and even cryptographic software.
Mate's personalized desktop environment offers an attractive interface, and Parrot Security OS itself runs very fast, even on machines with 2GB of RAM. Several niche utilities are built into the system, for example, apktool - a tool for modifying APK files.
For users who care about privacy, the distribution provides a special category of applications where users can enable anonymous surfing mode on the Internet (used Tor networks) in one click.
JonDo
Found a typo? Press Ctrl + Enter
Staying anonymous online is not always the same as surfing the web safely. It is important to keep the maximum technical information your device is safe from prying eyes, so that attackers cannot take advantage of the vulnerabilities of your system and steal your confidential data and use it for their own purposes, which can have serious consequences.
If you want to stay anonymous online and protect your data, in this article we will take a look at the most secure linux distributions to help you with this.
Most of the tools listed in this article are completely free to use. In addition to them, there are paid options, for example, VPN, but these free tools do their job much better. The need for security on the Internet is constantly growing, there is always a risk of cyberattack and eavesdropping by intelligence agencies. Not surprisingly, several distributions were immediately created, combining tools that provide maximum anonymity on the web.
These distributions were originally aimed at narrow specialists, but recently they have gained a lot of popularity. Due to the demand for such systems from users, they are constantly evolving and new ones are added, perhaps now there are more than twenty of them, but we will consider only the best safe linux distributions.
Most of them use Tor software for anonymity, which really provides high level anonymity, unlike VPN providers who still know your real IP address.
But a VPN still has many advantages, making it the best option in some cases. If connection speed is important to you or you are going to transfer files over P2P, then VPN will win.
Before looking at the most secure linux distributions, let's talk about how Tor anonymity is maintained. Tor or The Onion Router is a standard encryption protocol developed by the US Navy.
Tor software works with multiple nodes to ensure high reliability and anonymity. When passing through a random node, data is re-encrypted each time and becomes fully decrypted only at the last node. The Tor developers are also responsible for creating the Tails distribution that Edward Snowden recommends.
Now let's get back to VPN. Usually, these are paid services, it is very difficult to find a good, free VPN. VPN quality of service varies by provider, but VPN servers generally run much faster than Tor.
1. Tails - anonymous LiveCD
If you want to stay anonymous online, Tails is a great choice. Its main purpose is to make sure that you don't leave any digital footprints while surfing the web. It is one of the most commonly used distributions for anonymity, and the only one where all Internet connections are routed through Tor.
Usually Tails is installed on a USB flash drive, all data is stored in RAM, and is erased after completion of work. The operating system is based on Debian and comes with a large set of open source tools source code specially designed for confidentiality. It supports MAC address spoofing and Windows camouflage when the system looks very similar to Windows 8.
Tails uses outdated version Gnome, which looks ugly and minimalistic without the possibility of additional customization and improvement, since files are not saved between sessions. This may not matter to many, because Tails gets the job done. The distribution has excellent documentation and you can read it on the official website.
2. JonDo Live-DVD
JonDo Live-DVD is a commercial solution for online anonymity. It works in a similar way to Tor, your data is also transferred through a series of JonDonym mixed servers. At each node, the data is re-encrypted. it great alternative for Tails, especially if you are looking for something with a less limited user interface.

Like Tails, the distribution is based on Debian and also includes a suite of anonymity tools and commonly used applications.
JonDo Live-DVD is paid service, for commercial use. It is geared towards corporate use and is faster than Tails and also does not support saving files.
If you want something completely different, you will be interested in Whonix. This is a completely different approach. This is not a LiveCD. Whonix runs in a VirtualBox virtual machine, the system is isolated from your main system, thereby reducing the risk of catching viruses or exposing your data on the network.
Whonix has two parts. Whonix Gatway acts as the Tor gateway, the second - Whonix Workstation is completely isolated from the network and directs all its network connections through the Tor gateway.

Thus, it is necessary to use two virtual machines here, which can create certain problems if you have weak hardware. But it works nonetheless. True, this is not the safest Linux distribution like the Live CD, since it does not store data on the hard drive.
Whonix is based on Debian, but uses KDE as the desktop environment. The operating system is not suitable for everyday use and you can only use it in a virtual machine.
4. Qubes OS
This is another anonymity distribution recommended by Snowden. Qubes tries to fix the shortcomings of all previous distributions with insufficiently beautiful and customizable user interface. It is a distribution for everyday use that combines the power of Tor and Whonix.

This is a completely different approach to anonymity. The idea behind Qubes is safety by separation. This means that your digital life will be divided between isolated virtual machines... Any application runs in a separate virtual environment.
It should be noted that Qubes ships by default with Purism's flagship laptop. This laptop is considered the safest device for users. And that's true given the distribution's powerful software.
If you are looking for a convenient distro for everyday use with all the standard functionality and familiar applications, Qubes OS can be a great choice. Unlike the above, it can be installed on a hard drive.
5. UPR (Ubuntu Privacy Remix)
UPR is another installable distribution focused on security. It is user-friendly and provides an isolated environment in which sensitive data can be kept safe.

As the name suggests, it is based on Ubuntu. The distribution kit offers safe surfing the Internet and the use of encrypted flash drives to effectively protect your data from unauthorized access. The distribution comes with preinstalled encryption tools like GnuPG and TrueCrypt. UPR is only for safe internet surfing, not for anonymity. It is great if you want to install the system on your computer, rather than using a LiveCD. If you also need anonymity, you can install Tor or connect a VPN.
conclusions
Considering that Tails is the most common of all those mentioned in this article, you can decide that it is the safest. But other distributions serve their purpose very well too. So it all comes down to personal preference.
INTRODUCTION
Operating room Linux system inherited the Unix security system, developed back in the 70s, advanced at the time of creation, but today it is clearly insufficient. Each user has complete freedom of action within the limits of his authority on an all-or-nothing basis. This leads to the fact that to perform some tasks, the user is often granted much more rights than is really necessary. Therefore, the user who has gained access with the rights of the system account, can achieve almost complete control over the system.
In the course of the operation of any application, various deviations can occur, leading, as a result, to its abnormal execution. These can be both system failures, programming errors, and artificially caused situations. A hacker, having discovered that under certain conditions, it is possible to influence the execution of the program, naturally, he will try to take advantage of this. It is almost impossible to predict the behavior of a program in freelance mode. An example of this are antiviruses, which all the time work in a “catching up” rhythm, not providing protection against so-called zero-day attacks. However, the normal behavior of a program can be described with relatively simple rules... As a result, several projects have emerged that implement the concept of proactive protection.
The purpose of this course work is to study software products aimed at strengthening the security of the operating system, comparative analysis their main characteristics, as well as summing up the results of the work done and justifying their practical application.
DEFINITION OF A PROTECTED OPERATING SYSTEM. SELINUX
Protected operating system concept
Operating system- a software package that provides control of computer hardware, organizes work with files and execution of application programs, and provides input and output of data.
Calculating the "safest operating system" is not as easy as it seems at first glance. The main criterion that users who do not understand security standards are guided by is the number of identified vulnerabilities. However, the minimum of loopholes found in the system is not yet a reason to consider it reliably protected. There are a number of factors to consider when talking about safety, including:
- whether the quality of the OS source code is checked;
- what are given standard settings security;
- how quickly and efficiently the fixes are released;
- how the system of distribution of powers works and much more.
When choosing a secure OS, should definitely be considered operating system Linux.
First, the Windows OS was never designed directly to ensure the security of the system, it was always closed from outside eyes - the whole windows code encrypted. In theory, Windows can be prepared for safe use, but no one has done this yet, since it would take a huge amount of time. Linux, by virtue of its openness, allows you to work with the source code of the OS. Special versions of Linux have already been released, which are completely safe.
Secondly, the Live CD technology - Linux is able to start up and deploy very quickly without installing it on a hard drive. Such a secure OS can be written on optical disc or a USB stick and always have it with you. “In the blink of an eye,” it is possible to get an operating system with a ready-made desktop and related applications for working on the Internet, regardless of the installed main operating system in the computer that is to be used.
The kernel is the central component of the operating system. It is responsible for the management of system resources, communication between hardware and software, and security. The kernel plays a critical role in maintaining security at higher levels.
As indicated earlier, there are a number of important Linux kernel patches to help keep your system secure. Their significant differences are mainly in how they are administered and how they integrate into an existing system. Also, patches provide access control between processes and objects, processes and other processes, objects and other objects.
15.04.2001 Ruslan Bogatyrev
Never before in history has the real world been so dependent on the artificial world, invented and built by man himself - the Internet not only built bridges between countries and continents, but also brought the criminal closer to the victim. As a result, there has been a growing interest in trusted and secure operating systems.
The security of computer systems has been and remains a headache for those who are not indifferent to the fate of important information that affects decision-making, financial management, resource allocation, etc. Years go by, and the number of those wishing to take advantage of the fruits of someone else's labor or cause deliberate damage does not decrease, but increases continuously. Moreover, thanks to the ability to quickly and widely disseminate "best practices" to overcome protective barriers, due to the obvious carelessness of many information owners and the rare observance of the principle of inevitability of punishment, the whole world is faced with a serious and cruel disease. Her name is unknown, but her danger is obvious. She in a latent form struck a huge territory and now threatens to develop into a real epidemic.
Never before in history has the real world been so dependent on the artificial world, invented and built by man himself. Without taking proper care of the organization of effective protection of our creations, for the benefit of the development of civilization, we strive to connect these two universe deeper and deeper with information channels, to ensure maximum penetration of a more imperfect world into a less imperfect one. Computer evolution has already passed three important stages:
- concentration of computing and information resources(in the era of mainframes);
- ensuring the technical availability of computer facilities for a mass audience (in the era of the PC);
- breaking the natural boundaries of space and time on the scale of the world economy and politics (in the era of the Internet).
A single digital form of representation has greatly facilitated the solution of many practical problems, but at the same time inevitably created the basis for causing maximum damage at minimum cost. Moreover, due to the unification information exchange and the simplicity of working with software tools, harm can be done even by an inexperienced person. Only when faced with the AIDS problem, we were able to realize that our body has its own multi-level protection, where immunity plays an almost key role. The absence of such an all-pervading protective barrier in the computer world in the not-too-distant future promises to bring problems of such magnitude, in comparison with which the troubles caused by modern epidemics seem small and insignificant. The time has come to seriously think about the fact that without the erection of artificial barriers, without the creation of analogs of local immune protection for software, it becomes more and more dangerous to move forward.
When it comes to information security problems, they usually resort to a simple and proven scenario: first, to thoroughly intimidate the audience with figures and facts characterizing the scale and nature of the impending danger, and then proceed to the main part - to present recipes for miraculous "drugs" that eliminate a number of the mentioned symptoms ... Paying tribute to tradition, let's not stray too far from the beaten path. However, it hardly makes sense to dissemble: there are far more problems here than solutions. So the main focus will be on the pain points of computer configurations - their operating systems.
Based on the Institute's 2001 Computer Crime and Security Survey annual report computer security in San Francisco and the FBI, financial losses from computer crimes in the United States over the past year increased by 43% from $ 265.6 million to $ 377.8 million.At the same time, 85% of 538 respondents, mainly from industrial and government structures , announced the facts of computer security breaches, and not only due to attacks by cybercriminals. Almost 64% were concerned about the incurred losses, but only 35% were able to assess them in monetary terms. About 70% of respondents said that Internet channels were most often attacked, and 31% indicated that corporate systems were attacked. Cases of intrusion from the outside were confirmed by 40% of respondents (in 2000 - 25%), and 38% recorded a denial of service (27% in 2000). 91% of respondents complained about violation of privileges due to employee abuse of work on the Internet, and 94% found viruses in their systems (in 2000, 85% noted this).
Even these scant figures show a clearly negative trend - the Internet not only builds bridges between countries and continents, but also brings the perpetrator closer to the victim. To paraphrase a well-known saying, we can say that if you are not interested in cybercrime, very soon cybercriminals will be interested in you. Leaving aside the age-old issues of intelligence and industrial espionage and focusing only on the “everyday” side of the matter, attacks on payment systems, discrediting companies (denial of service), industrial sabotage, autopsy corporate secrets, violation of rights intellectual property... The Science and Technology Department under the President of the United States estimates that the annual damage inflicted on American businesses by cybercriminals in last years, reached $ 100 billion. Losses from unauthorized access to information related to the activities of US financial institutions amounted to at least $ 1 billion per year. Thus, American business has come close to the point where timely and adequate security solutions become economically feasible for them.
Unix in a security context
The history of the OS is inseparable from the history and evolution of the computers themselves. It just so happened that it is the Unix clones that dominate the corporate systems market today and have become the link between the world of personal and high-performance computers. Unfortunately, Unix suffers from serious shortcomings, and the Linux phenomenon forced us to look differently at many problems, including the problems of information security.
Unix does not have a clear mechanism for enforcing integrity custom programs and files does not provide access control for an individual user; differentiation of rights is carried out within the groups. In normal Unix, it is not so difficult for an outside person to seize superuser privileges. Accounting and control over user actions, especially when working with security-critical resources, is also not a strong point of regular UNIX. Of course, with some configuration effort on the part of the system administrator, some of the flaws can be eliminated. But in general, the picture does not look encouraging.
The work of the US National Security Agency provides a detailed analysis of the problems facing the current generation of operating systems in terms of computer security. The main conclusion: we need new specially designed secure operating systems. In particular, the authors say that the Kerberos system, SSL protocols and IPSEC are highly vulnerable in that protection becomes illusory if no reliable software is available at the ends of a connection.
Elias Levy (Aleph1), moderator of the well-known computer security mailing list BugTraq, said in a recent interview: “I think the security model in Unix is overly simplistic. The all-or-nothing approach turns out to be worthless compared to the least privilege ... A Trusted Computing Base will never provide all that a user would require. On the other hand, I find that most implementations of mandatory access control, privilege, etc. too complex ... Ultimately, it is difficult to predict the interactions that will lead to the emergence of weaknesses. Consider the sendmail problem as a result of the permissions implemented in the Linux kernel. "
Levy calls for abandoning the practice of "patching holes" and starting to build a new OS that initially meets the security requirements.
This echoes the current interest in trusted and secure operating systems. Security requirements should be determinative in the design of the OS, and not introduced as ancillary services.
Safety criteria and benchmarks
Work on system safety criteria began as early as 1967 and in 1970 the first report appeared titled “ Security Controls for Computer Systems". In 1983, the US Department of Defense issued “ Orange book"- an orange cover book called Trusted Computer Systems Evaluation Criteria. Region computer networks in relation to security has been defined in the so-called X.800 - Security Architecture for Open Systems Interconnection for CCITT Applications. The Orange Book defines a trustworthy system as “a system using sufficient hardware and software to ensure the simultaneous processing of information of varying degrees of secrecy by a group of users without violating access rights ”.
There are two main criteria for evaluating reliable systems:
- security policy (a set of rules and regulations that determine the discipline of processing, protection and dissemination of information, as well as the choice of specific security mechanisms; it is active ingredient protection);
- assurance (the degree of confidence that can be provided to a specific OS implementation; reflects the level of correctness of security mechanisms; is a passive component of protection).
According to the Orange Book, there are three roles: System Administrator, System Operator, and Security Administrator. According to TCSEC requirements, the manufacturer's documentation must include four important element: security policy; reliable computing base interfaces; TCB mechanisms; guidance on the effective use of TCB mechanisms.
Generally speaking, operating systems are not the only domain of protected components. So, in particular, in addition to the TCSEC Orange Book, which regulates security issues in the OS, there are similar documents of the US National Center for Computer Security for DBMS (TDI, “ Purple book") And networks (TNI," Red Book"). So the Orange Book is not the only, albeit important, document. A whole series of documents in multi-colored covers, called "Rainbow" ( Rainbow series; www.radium.ncsc.mil/tpep/library/ rainbow). At the same time, as can be seen from the inset, sometimes different material appeared under the cover of the same color.
Outside the United States, analogues of the Orange Book have also appeared: these are the guidance documents of the State Technical Commission (1992), as well as the Safety Assessment Criterion information technologies”(ITSEC - Information Technology Security Evaluation Criteria, 1991), valid in the UK, Germany, France and the Netherlands.
Of course, due to the need to unify approaches to information security, in the end the need arose to remove the duality of regulation, which was separately conducted in the United States (TCSEC) and Europe (ITSEC). In fig. 1 shows the "family tree" of the adoption of a new international standard called "Unified criteria for assessing security in the field of information technology." More often than not, it is simply referred to as the "Common Criteria" international standard ISO / IEC 15408, co-authored by the National Security Agency and the National Institute of Standards and Technology (USA), the Electronics and Data Communications Security Group (UK), the Federal Agency for Information Technology (Germany), the Central Information Security Service systems (France), Netherlands National Security Agency for data communications, Security Service for data communications (Canada).
Common Criteria V2.1 is described in three books:
- Introduction and General Model (CCIMB-99-031).
- Functional requirements to security (CCIMB-99-032).
- Security Assurance Requirements (CCIMB-99-033).
There are 11 functional classes in the "Unified Criteria":
- audit;
- cryptographic support;
- data transfer;
- protection of user data;
- identification and authentication;
- security management;
- confidentiality;
- protection of the security functions of the target system;
- utilization of resources;
- access to the target system;
- reliable paths / channels.
Each of these classes contains several families, and each family contains from one to several components.
The criteria formulated in TCSEC, ITSEC and CCITSE determine the division of computer systems into 4 security levels (A, B, C, D), depending on the degree of confidence. Level A is the highest. Next comes level B (in order of decreasing safety, here are classes B3, B2, B1). Then the most common level is C (grades C2 and C1). The lowest level is D (systems that could not obtain certification for the above classes).
Following a trade-off between security requirements, system efficiency and its cost, the vast majority of companies today are striving to achieve C2 certification.
Literature
1. P. Khristov. Data Security in UNIX OS // "Open Systems", 1993, No. 3
2. V. Galatenko. Information Security // "Open Systems", 1995, No. 4, 1996, No. 1
3.R. Bogatyrev. Linux: the origins of a new philosophy of programming // World of PCs, 2001, No.1.
4.11 Computer Crime and Security Survey // Computer Security Institute, San Francisco, March 12, 2001; www.gocsi.com/prelea_000321.htm
5. Common Criteria for Information Technology Security Evaluation (CCITSE) V2.1 // 1998; www.radium.ncsc.mil/tpep/library/ccitse/ccitse.html
6 P. Loscocco et al. The Inevitability of Failure: The Flawed Assumptiom of Security in Modern Computing Environments // National Security Agency, 1998.
Ruslan Bogatyrev
The subject of a set of books on computer security TCSEC in the "Rainbow" series
- TCSEC (1983, 1985, Orange Book, 5200.28-STD).
- TNI, Interpretation of Reliable Computer Networks (1987, 1990, Red Book, NCSC-TG-005, NCSC-TG-011).
- TDI, Reliable Database Interpretation (1991, The Purple Book, NCSC-TG-021).
- Formal Verification Systems (1989, The Purple Book, NCSC-TG-014).
- Verified Systems Manufacturing (1992-1994, Purple Books, NCSC-TG-024).
- Access Protection (1992, Purple Book, NCSC-TG-028).
- Confidence Distribution (1988, Dark Green Book, NCSC-TG-008).
- Creation of documentation (1988, Ruby Book, NCSC-TG-007).
- RAMP (1995, Pink Book, NCSC-TG-013).
- Analysis of Secret Channels (1993, "Light Pink Book", NCSC-TG-030).
- Safety Testing (1991, Bright Orange Book, NCSC-TG-023).
- Discretionary Access Control (1987, The Neon Book, NCSC-TG-003).
- Guidelines for Creating User Guides (1991, The Peach Book, NCSC-TG-026).
- Configuration Management (1988, Amber Book, NCSC-TG-006).
- Computer Security Requirements (1985, Bright Yellow Book, CSC-STD-003-85).
- Technical clarifications for computer security requirements (1985, Yellow Book, CSC-STD-004-85).
- Reliable disaster recovery (1991, Yellow Book, NCSC-TG-022).
- Writing guidelines for managing credible funds (1992, Green-Yellow Book, NCSC-TG-016).
- Data acquisition in automated information systems(1991, The Pale Green Book, NCSC-TG-025).
- Password Management (1985, Green Book, CSC-STD-002-85).
- Computer Security Terminology Dictionary (1988, The Dark Green Book, NCSC-TG-004).
- Security Modeling (1992, Blue-Green Book, NCSC-TG-010).
- Security Administrator Competence (1992, Turquoise Book, NCSC-TG-027).
- Identification and Authentication (1991, Light Blue Book, NCSC-TG-017).
- Reusable Objects (1992, Light Blue Book, NCSC-TG-018).
- Questionnaires for the assessment of reliable systems (1992, "Blue Book", NCSC-TG-019).
- Concepts for Certification and Accreditation (1994, Blue Book, NCSC-TG-029).
- Evaluating Credible Products (1990, Bright Blue Book, NCSC-TG-002).
- Interpreting Computer Security Subsystems (1988, Sky Blue Book, NCSC-TG-009).
- Management of Trustworthy Funds (1989, The Brown Book, NCSC-TG-015).
- Auditing in Trusted Systems (1988, Light Brown Book, NCSC-TG-001).
- TRUSIX (1989, The Silver Book, NCSC-TG-020).
Computer Systems Security Classes (TCSEC, Common Criteria)
Class D. Minimum level of security. This class includes systems that have been applied for certification, but have not passed it. While in this class no OS is registered.
Class C1. Selective access protection. Provides for the availability of a reliable computing base (TCB), meeting the requirements for selective security. Separation of users from data is provided (measures to prevent reading or destruction of data, the ability to protect private data). Currently, there is no certification for this class.
Class C2. Managed access protection. Systems of this class are able to implement more clearly dedicated control in terms of selective access protection. User actions are associated with identification / authentication procedures. Granting and depriving users of access privileges. In addition, security-critical events are audited and resources are isolated. Certified in this class: AIX 4.3.1, OS / 400 V4R4M0 with Feature Code 1920, AOS / VS II, Release 3.10, OpenVMS VAX and Alpha Version 6.1, CA-ACF2 MVS Release 6.1, NT Workstation and NT Server, Ver. 4.0, Guardian-90 w / Safeguard S00.01.
Class B1. Labeled security. In addition to class C2 requirements, an informal description of the security policy model, data labeling, and enforcement of access control to named subjects and objects is required. Certified in this class: CA-ACF2 MVS Release 6.1 bundled with CA-ACF2 MAC, UTS / MLS, Version 2.1.5+ (Amdahl), SEVMS VAX and Alpha Version 6.1, ULTRIX MLS + Version 2.1 on VAX Station 3100, CX platform / SX 6.2.1 (Harris Computer Systems), HP-UX BLS release 9.0.9+, Trusted IRIX / B release 4.0.5EPL, OS 1100/2200 Release SB4R7 (Unisys).
Class B2. Structured protection. In this class of systems, the TCB should rely on a well-defined and documented formal security policy model. Selective and compulsory access control applies to all subjects and objects in the system. Covert channels are revealed. TCB should be clearly decomposed into critical and non-safety critical elements. Authentication mechanisms are being strengthened. The control of validity mechanisms is provided in the form of support for the functions of the system administrator and operator. Strong configuration management mechanisms are assumed. The system is relatively resistant to intrusion. Trusted Xenix 4.0 (Trusted Information Systems) is certified in this class.
Class B3. Security domains. TCB must meet the requirements of a reference monitoring mechanism that controls absolutely all access of subjects to objects and at the same time be compact enough to be analyzed and tested. Security administrator required. Auditing mechanisms are expanded to include the ability to report security-critical events. System recovery procedures are required. The system is extremely resistant to intrusion. XTS-300 STOP 5.2.E (Wang Government Services) is certified for this class.
Class A1. Verified design. This class of systems is functionally equivalent to class B3 in the sense that no additional architectural features or other security policy requirements are required. A significant difference is that a formal design specification and appropriate verification methods are required to ensure that the TCB is implemented correctly. No OS is registered in this class.



