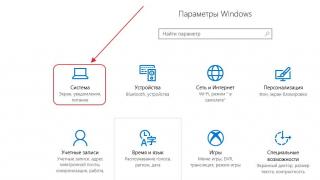
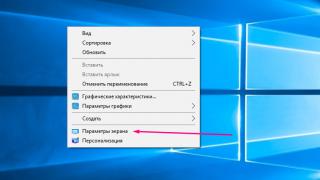
Signal coding
Signal coding serves for the exchange of information between the individual components of the control system of the TOU (ACS or ACS) (circuits, nodes, devices, blocks), its processing and storage with the required accuracy and reliability (the highest noise immunity). Coding is to use code- a universal way of displaying information during its transmission, processing and storage. The code is a system of correspondences between elements of messages and signals, with the help of which these elements can be fixed. In the code, different types of signals of the same physical nature are called symbols... The finite set of symbols chosen to convey a specific messages is called word... Code signal (code) - a special type of signals (digital signal). Coding can be performed either from analog or discrete signals (Figure 1.2).
example: 0 or 1 - symbols in one bit of the binary code (1 bit of information);
a byte contains 8 bits of information (8 bits), i.e. for example 10001001 byte words.
In the ACS, as in any information-measuring systems (IMS), two transmission methods are used messages(word assemblies): parallel code- all symbols of one word are transmitted simultaneously over channels, the number of which corresponds to the number of symbols, i.e. word length (8 channels are needed to transmit a byte word); sequential code- characters of one word are transmitted one after another over one channel.
The choice of codes is determined by the specifics of the perception and transformation of information, characteristic of a given level of the APCS and its components.
The main requirements that are put forward when choosing a coding method are: the economy of displaying information, the simplicity of the technical implementation of coding devices, the convenience of performing computational operations and the reliability of message transmission.
To fulfill these requirements, especially related with the convenience of performing computational operations, the most suitable is a digital code (alphabet), the number of characters in which depends on the base of the number system and usually does not exceed 10 or 16. This approach allows coding not only numbers, but also concepts.
Using code with a radix n any number can be represented as:
where N- the number of digits; a j- the number of characters in one digit.
If we omit n j, then we get a more compact notation N- bit (from N-1 to 0) of the number M:
![]() . (1.2)
. (1.2)
Example: M = 123 = 1 × 10 3 - 1 + 2 × 10 2 - 1 + 3 × 10 ° (n = 10).
It follows from formulas (1.1) and (1.2) that the same number M depending on the basis n when encoding, it is formed from a different number of characters in one bit ( a j) and the number of digits ( N). For example, a digital 3-digit decimal voltmeter, representing information in a base 10 code, has 10 different digits (symbols) in each digit, it can give 1000 (0, 1, ..., 999) different values of the measured parameter with an accuracy of 1 least significant digit (voltage). to perform the same operation in binary code (base 2 code), 10 bits with two significant digits in each of them are required (2 10 = 1024).
Let n Is the maximum number of characters in a bit (code base), and N - number of digits.
Then the possible number of different messages is
For example, 1024 = 2 10; in binary code, using 10 bits, you can write the maximum number of 1024, i.e. to transmit the number 1024 you need 10 channels (bits) of the binary code.
Economical coding will be the higher, the fewer characters should be spent on the transmission of the same message. When transmitting messages over a communication channel, the number of characters also determines the time required for this.
For reasons simplicity of technical implementation clear advantage on the code side with n= 2, at which discrete elements with two stable states are required for storing, transmitting and processing information.
Example: logical functions: "yes" - "no", the state of the TOU unit: "enabled" - "disabled", the action (operation): "completed" - "not performed", the technical state of the TOC unit: "serviceable" - "faulty", encoded by digits "1" - "0".
Therefore, the binary code has become widespread in digital devices for measuring control, control and automation.
When entering binary-coded information into a computer for compact recording, codes are often used whose base is an integer power of 2: 2 3 = 8 (octal) and 2 4 = 16 (hexadecimal).
For example, consider the formation of numbers in various number systems (Table 1.1).
Table 1.1
| Notation | |||
| Decimal n = 10 | Binary n = 2 | Octal n = 8 | Hexadecimal n = 16 |
| A | |||
| B ... F | |||
Consider binary positional codes. Among them, special codes are widely used: direct, reverse, additional... All of these codes contain special sign rank.
In straight code the sign is encoded 0 for positive and 1 for negative numbers. Example 1100 (+12) in direct code 0.1100. Direct code is convenient for performing multiplication operations because the product sign is obtained automatically. However, subtraction is difficult. This disadvantage is eliminated by using reverse and additional codes, which differ from the direct way of representing negative numbers. Reverse code a negative number is formed by inverting all significant digits (-1100 (- 12) in the reverse code: 1.0011). In complementary code after inverting the digits, 1 is added to the least significant size. Example: - 1100 in the additional code: 1.0100.
Information display (digital indication) has found application in systems and devices binary decimal codes... In these codes, each decimal digit is represented by four binary (tetrad).
Coding systems in 2-10 codes are shown in Table 1.2.
Table 1.2
Selecting a sampling frequency for an analog-to-digital converter (ADC)... When quantizing and subsequent coding of signals, for example, in the case of time quantization in the form of pulses modulated in amplitude (Fig. 1.3, b), further conversion of signals in the ADC consists in representing the amplitude of the pulses with a binary code. In this case, the establishment of the quantization frequency is complicated in cases where the original analog signal y(f) is an arbitrary function of time and does not lend itself to analytical expression. Then the sampling frequency is determined based on V. A. Kotelnikov's theorems... This theorem considers a continuous function with a bounded frequency spectrum, i.e. contains frequencies from 0 to f m a x... Such a function can be represented with sufficient accuracy using numbers following each other at intervals of time
Therefore, based on formula (1.4), which determines the quantization step, at the quantization frequency
2. In narrowband transmission a bipolar discrete signal is used. In this case, the encoding in the network adapter of the transmitting PC of digital data into a digital signal is performed directly.
The simplest and most commonly used is coding method without return to zero (NRZ - Non Return to Zero), in which bit "1" is represented by positive voltage (H - high level), and bit "0" - negative voltage (L - low level). That is, the signal is always above or below zero voltage, hence the name of the method. An illustration of the described signal coding methods is shown in Figure 5.22.
For both analog and digital signals, if the consecutive bits are equal (both "0" or both "1"), then it is difficult to tell when one ends and the other begins. To solve this problem, the receiver and the transmitter must be synchronized, that is, the time intervals must be counted equally.
This can be done either by introducing an additional line for transmitting sync pulses (which is not always possible, and expensive), or by using special data transmission methods: asynchronous or auto-tuning.
Figure 5.22 - Options for signal coding.
Methods of data transmission over networks
At low signal rates, the asynchronous transmission method is used, at high rates, it is more efficient to use the auto-tuning method. Both the transmitter and the receiver are equipped with clock generators operating at the same frequency. However, it is impossible for them to work absolutely synchronously, so they need to be adjusted periodically. Similar to an ordinary watch, which needs to be adjusted periodically.
At asynchronous transfer the generators are synchronized at the beginning of the transmission of each packet (or byte) of data and it is assumed that during this time there will be no generators mismatch that would cause transmission errors. In this case, it is assumed that all packages of the same length(for example a byte). Synchronization of the receiver clock is achieved by:
· Before each packet (byte) an additional "start-bit" is sent, which is always "0";
· At the end of the packet, another additional "stop bit" is sent, which is always "1".
If no data is being transmitted, the link is in state "1" (idle state). The beginning of the transmission causes a transition from "1" to "0", which means the beginning of the "start bit". This transition is used to synchronize the receiver's oscillator. Let's explain this process with a timing diagram (Figure 5.23):

Figure 5.23 - Asynchronous transmission
At auto-tuning transmission- the Manchester coding method is used, in which:
· The clock generator of the receiver is synchronized with the transmission of each bit;
Therefore, you can send packages of any length.
Synchronization of the data signal is achieved by ensuring the transition from the "H" -layer to the "L" -layer, or vice versa, in the middle of each data bit (Figure 5.24). These transitions are used to synchronize the receiver clock. Data bits are encoded: "0" - with the transition "L" → "H" and "1" - with the transition "H" → "L"

Figure 5.24 - Transfer with auto-tuning
If no information is transmitted, there are no transitions in the data line and the clock generators of the transmitter and receiver are mismatched.
With this type of coding, transitions occur not only in the middle of each data bit, but also between bits when two consecutive bits have the same value.
After the line is idle, preliminary synchronization of the generator is required, which is achieved by sending fixed bit sequence(preamble and readiness bits).
For example, you can use a preamble of eight bits: 11111110, where the first 7 bits are used for initial synchronization, and the last one is used to inform the receiver that the preamble has ended, i.e. data bits will follow.
Lecture 17
Topic 5.3 Principles of functioning of local area networks
Lecture plan
- Basic LAN components
- LAN types
- Peer-to-peer networks
- Server based networks
- Combined networks
- Hardware
- Concept of network topology and basic topologies:
bus topology
star topology
ring topology
combined topologies
- Comparative characteristics of topologies
- Methods of access to the physical transmission medium
The main part of the lecture
Basic LAN components
PC-based LANs are now widely used due to their low complexity and low cost. They are used in the automation of industry, banking, as well as for the creation of distributed, control and information-reference systems. LANs are modular.
servers are hardware and software systems that perform the functions of managing the distribution of shared network resources;
– workstations- these are computers accessing network resources provided by the server;
- f physical data transmission medium (network cable) - these are coaxial and fiber-optic cables, twisted pairs of wires, as well as wireless communication channels (infrared radiation, lasers, radio transmission).

LAN types
There are two main types of LANs: peer-to-peer LANs and server based LANs. The differences between them are of fundamental importance, since they determine the different capabilities of these networks.
The choice of the LAN type depends on:
· The size of the enterprise;
· The required level of security;
· The volume of network traffic;
· Financial costs;
· The level of availability of network administrative support.
At the same time, the tasks of network administration usually include:
· Management of user work and data protection;
· Providing access to resources;
· Application and data support;
· Installation and modernization of application software.
Peer-to-peer networks
In these networks, all computers are equal: there is no hierarchy among them; no dedicated server. As a rule, each PC functions both as a workstation (PC) and as a server, i.e. there is no PC responsible for
Figure 5.25 - LAN components
administration of the entire network (Figure 5.26). All users decide for themselves which data and resources (catalogs, printers, fax modems) on their computer to make publicly available over the network
Working group Is a small team united by a common goal and interests. Therefore, in peer-to-peer networks, most often there are no more than 10 computers. These networks are relatively simple. Since each PC is both a PC and a server. There is no need for a powerful central server or other components required for more complex networks.
Peer-to-peer networks are usually cheaper than server-based networks, but require more powerful, and therefore more expensive, PCs. The performance requirements and the level of protection for network software in them are also significantly lower.

Figure 5.26 - Peer-to-peer network
In such operating systems as: MS Widows NT for Workstation; MS Widows 95/98, Widows 2000 built-in support for peer-to-peer networks. Therefore, to establish a peer-to-peer network, additional software is not required, and a simple cabling system is used to connect the computers. Peer-to-peer networking is fine where:
· The number of users does not exceed 10-15 people;
· Users are located compactly;
· Data protection issues are not critical;
· In the foreseeable future, the expansion of the company is not expected, and, consequently, the increase in the network.
Although peer-to-peer networks are well suited to the needs of small firms, there are situations where their use is inappropriate. In these networks, protection involves setting a password on a shared resource (for example, a directory). It is difficult to centrally manage peer-to-peer protection because:
- the user installs it himself;
- "Shared" resources can be located on all PCs, not just on the central server.
This situation is a threat to the entire network; in addition, users may not install protection at all.
Server-based networks
If more than 10 users are connected, the peer-to-peer network may not perform well. Therefore, most networks use dedicated servers (Figure 5.27). Highlighted such servers are called which function only as a server (excluding the functions of a PC or a client). They are specially optimized for fast processing of requests from network clients and for managing the protection of files and directories.

Figure 5.27 - Server-based network structure
As the size of the network and the volume of network traffic increase, the number of servers must increase. Spreading tasks across multiple servers ensures that each task is performed in the most efficient way possible.
The range of tasks that servers perform is varied and complex. To accommodate the increasing needs of users, LAN servers have become specialized. So, for example, in the Windows NT Server operating system, there are different types of servers (Figure 5.15):
– File servers and print servers... They control user access to files and printers. In other words, a file server is for storing files and data;
- With Application servers(including database server, WEB server ) ... Application parts of client-server applications (programs) are executed on them. These servers are fundamentally different from file servers in that when working with a file server, the required file or data is copied entirely to the requesting PC, and when working with the application server, only the results of the request are sent to the PC;
– mail servers- manage the transmission of electronic messages between network users;
- f ax servers- control the flow of incoming and outgoing fax messages through one or more fax modems;
- To communication servers- control the flow of data and mail messages between this LAN and other networks or remote users through a modem and a telephone line. They also provide access to the Internet;
- With directory services server- designed to search, store and protect information on the network.
Windows NT Server unites PCs into logical domain groups, the security system of which gives users different access rights to any network resource.

Figure 5.28. - Types of servers in the LAN
Moreover, each of the servers can be implemented both on a separate computer and in a small-sized LAN, be combined on one computer with some other server. North and OS work as a single unit. Without an OS, even the most powerful server is a heap of hardware. The OS allows you to realize the potential of the server's hardware resources.
Coding on the two lower channels characterizes the method of representing information by signals that propagate through the transport medium. Coding can be thought of as a two-step encoding. And it is clear that symmetric decoding is implemented on the receiving side.
Logical coding data modifies the bitstream of the generated MAC layer frame into a sequence of symbols that must be physically encoded for transport over the communication channel. Different schemes are used for logical coding:
- 4B / 5B - every 4 bits of the input stream are encoded with a 5-bit character (Table 1.1). A double redundancy is obtained, since 2 4 = 16 input combinations are shown by symbols of 2 5 = 32. The costs for the number of bit intervals are: (5-4) / 4 = 1/4 (25%). This redundancy allows you to define a number of service symbols that are used for synchronization. Applied in 100BaseFX / TX, FDDI
- 8B / 10B - a similar scheme (8 bits are encoded with a 10-bit symbol) but the redundancy is already 4 times (256 inputs to 1024 outputs).
- 5B / 6B - 5 bits of the input stream are encoded with 6-bit characters. Applied in 100VG-AnyLAN
- 8B / 6T - 8 bits of the input stream are encoded with six ternary (T = ternary) digits (-, 0, +). For example: 00h: + -00 + -; 01h: 0 + - + = 0; The code has redundancy of 3 6/2 8 = 729/256 = 2.85. The transport rate of symbols in the line is lower than the bit rate and their arrival at the encoding. Used in 100BaseT4.
- Bit stuffing - This scheme works to eliminate invalid bit sequences. We will explain its work on the implementation in the HDLC protocol. Here the input stream looks like a contiguous sequence of bits, for which a chain of more than five contiguous 1 parsed as an overhead signal (example: 01111110 is a frame separator flag). If the broadcast stream contains a continuous sequence of 1 , then after every fifth into the output stream the transmitter inserts 0 ... The receiver analyzes the incoming chain, and if after the chain 011111 He sees 0 , then he discards it and the sequence 011111 appends to the rest of the output data stream. If bit is received 1 , then the sequence 011111 looks like a service symbol. This technique solves two problems - to exclude long monotonic sequences, which are inconvenient for self-synchronization of physical coding, and allows the recognition of frame boundaries and special states in a continuous bit stream.
Table 1 - 4V / 5V coding
| Input Symbol | Output symbol |
|---|---|
| 0000 (0) | 11110 |
| 0001 (1) | 01001 |
| 0010 (2) | 10100 |
| 0011 (3) | 10101 |
| 0100 (4) | 01010 |
| 0101 (5) | 01011 |
| 0110 (6) | 01110 |
| 0111 (7) | 01111 |
| 1000 (8) | 10010 |
| 1001 (9) | 10011 |
| 1010 (A) | 10110 |
| 1011 (B) | 10111 |
| 1100 (C) | 11010 |
| 1101 (D) | 11011 |
| 1110 (E) | 11100 |
| 1111 (F) | 11101 |
Redundancy logical coding makes it possible to facilitate the tasks of physical coding - to eliminate inconvenient bit sequences, improve the spectral characteristics of a physical signal, etc. Physical / Signal Coding writes the rules for the representation of discrete symbols, the result of logical encoding into the result of physical line signals. Physical signals can have a continuous (analog) form - an infinite number of values from which a valid recognizable set is selected. At the level of physical signals, instead of the bit rate (bit / s), the concept is used the rate of change of the signal in the line which is measured in baud (baud). Under this definition, the number of changes in various states of the line per unit of time is determined. On the physical level, it passes synchronization receiver and transmitter. External synchronization is not used due to the high cost of implementing one more channel. Many physical coding schemes are self-timed — they permit the extraction of a clock signal from a received sequence of channel states.
Scrambling at the physical level, it allows suppressing very strong spectral characteristics of the signal, smearing them over a certain band of the spectrum. Very strong interference distorts adjacent transmission channels. When talking about physical encoding, the following terms can be used:
- Transit coding - informative is the transition from one state to another
- Potential coding - informative is the signal level at specific points in time
- Polar - a signal of one polarity is implemented to represent one value, a signal of another polarity is used to represent another. For fiber optic transport, pulse amplitudes are used instead of polarity
- Unipolar - a signal of one polarity is realized to represent one value, a zero signal - for another
- Bipolar - uses negative, positive and zero values to represent three states
- Two-phase - in each bit interval there is a transition from one state to another, which is used to isolate the sync signal.
Popular encoding schemes used in local networks
AMI / ABP
AMI - Alternate Mark Inversion or ABP - Alternate bipolare, a bipolar circuit that uses the values + V, 0V and -V. All zero bits have values of 0V, single bits - with alternating values of + V, -V (Fig. 1). Used in DSx (DS1 - DS4), ISDN. Such a scheme is not completely self-synchronizing - a long string of zeros will lead to loss of synchronization.
Picture 1
MAMI - Modified Alternate Mark Inversion, or ASI - modified AMI scheme, pulses of alternating polarity are coded 0, and 1 - zero potential. Used in ISDN (S / T - interfaces).
B8ZS - Bipolar with 8 Zero Substitution, a scheme similar to AMI, but excludes strings of 8 or more zeros for synchronization (due to bit insertion).
HDB3 - High Density Bipolar 3, the scheme is similar to AMI, but does not allow the transmission of a chain of more than three zeros. Instead of a sequence of four zeros, one of the four bipolar codes is inserted. (Fig. 2)
 Drawing - 2
Drawing - 2
Manchester coding
Manchester encoding is a bi-phase polar / unipolar self-timed encoding. The current bit is recognized by the direction of the state change in the middle of the bit interval: from -V to + V: 1. From + V to -V: 0. There may not be a jump at the beginning of the interval. Used in Ethernet. (In the initial versions - unipolar). (fig. 3)
 Figure - 3
Figure - 3
Differential manchester encoding - two-phase polar / unipolar self-synchronizing code. The current bit is recognized by the presence of a transition at the beginning of a bit interval (Fig. 4.1), for example 0 - there is a transition (vertical fragment), 1 - no transition (horizontal fragment). It is possible, and vice versa, to define 0 and 1. In the middle of a bit interval, there is always a transition. It is needed for synchronization. Token Ring uses a modified version of this scheme, where, in addition to bits 0 and 1, two bits j and k are also defined (Figure 4.2). There are no transitions in the middle of the interval. Bit K has a transition at the beginning of the interval, but j does not.
 Figure - 4.1 and 4.2
Figure - 4.1 and 4.2
Three-level scrambling coding that does not self-sync. Levels (+ V, 0, -V) are used constant in the line of each bit interval. When transmitting 0, the values do not change, when transmitting 1, they change to those adjacent along the chain + V, 0, -V, 0, + V, etc. (fig. 5). This scheme is a sophisticated version of the NRZI. Used in FDDI and 100BaseTX.
 Figure - 5
Figure - 5
NRZ and NRZI
NRZ - Non-return to zero (non-return to zero), bipolar non-transitive circuit (states change at the border), which has 2 options. The first option is the non-differential NRZ (used in RS-232) state directly reflects the bit value (Fig. 6.a). In another variant - differential, the NRZ state changes at the beginning of the bit interval for 1 and does not change for 0. (Figure 6B). There is no binding 1 and 0 to a specific state.
NRZI - Non-return to zero Inverted, modified NRZ scheme (Fig.6c). Here the states change to opposite ones at the beginning of bit interval 0, and do not change during transmission 1. The reverse representation scheme is also possible. Used in FDDI, 100BaseFX.
 Figure - 6-a, b, c
Figure - 6-a, b, c
RZ - Return to zero, bipolar transitive self-synchronizing circuit. The state at a certain point in the bit interval always returns to zero. Has differential / non-differential options. In differential, there is no binding of 1 and 0 to the state. (Fig. 7.a).
 Figure - 7-a, b
Figure - 7-a, b
FM 0 - Frequency Modulation 0, self-synchronizing polar code. Reverse at the edge of each bit interval. When transmitting 1 for a bit interval, the state is unchanged. When transmitting 0, in the middle of a bit interval, the state is reversed. (fig. 8). Used in LocalTalk.
 Figure - 8
Figure - 8
PAM 5 - Pulse Amplitude Modulation, five-level bipolar coding, where a pair of bits, depending on the history, turns out to be one of 5 potential levels. You need a narrow bandwidth (half the bit rate). Used in 1000BaseT.
Here a pair of bits turns out to be one Quater-nary symbol, where each corresponds to one of 4 signal levels. The table shows the ISDN character representation.
4B3T - a block of 4 bits (16 states) is encoded with three ternary symbols (27 symbols). Of the many possible change methods, consider MMS43, which is used in the BRI interface of ISDN networks (table). Here, special methods are used to eliminate the constant component of the voltage in the line, as a result of which the coding of a number of combinations depends on the background - the state where the encoder is located. Example: bit sequence 1100 1101 would be represented as: + + + - 0 -.
| Binary code | S1 | Transition | S2 | Transition | S3 | Transition | S4 | Transition |
|---|---|---|---|---|---|---|---|---|
| 0001 | 0 — + | S1 | 0 — + | S2 | 0 — + | S3 | 0 — + | S4 |
| 0111 | — 0 + | S1 | — 0 + | S2 | — 0 + | S3 | — 0 + | S4 |
| 0100 | — + 0 | S1 | — + 0 | S2 | — + 0 | S3 | — + 0 | S4 |
| 0010 | + — 0 | S1 | + — 0 | S2 | + — 0 | S3 | + — 0 | S4 |
| 1011 | + 0 — | S1 | + 0 — | S2 | + 0 — | S3 | + 0 — | S4 |
| 1110 | 0 + — | S1 | 0 + — | S2 | 0 + — | S3 | 0 + — | S4 |
| 1001 | + — + | S2 | + — + | S3 | + — + | S4 | — — — | S1 |
| 0011 | 0 0 + | S2 | 0 0 + | S3 | 0 0 + | S4 | — — 0 | S2 |
| 1101 | 0 + 0 | S2 | 0 + 0 | S3 | 0 + 0 | S4 | — 0 — | S2 |
| 1000 | + 0 0 | S2 | + 0 0 | S3 | + 0 0 | S4 | 0 — — | S2 |
| 0110 | — + + | S2 | — + + | S3 | — — + | S2 | — — + | S3 |
| 1010 | + + — | S2 | + + — | S3 | + — — | S2 | + — — | S3 |
| 1111 | + + 0 | S3 | 0 0 — | S1 | 0 0 — | S1 | 0 0 — | S3 |
| 0000 | + 0 + | S3 | 0 — 0 | S1 | 0 — 0 | S2 | 0 — 0 | S3 |
| 0101 | 0 + + | S3 | — 0 0 | S1 | — 0 0 | S2 | — 0 0 | S3 |
| 1100 | + + + | S4 | — + — | S1 | — + — | S2 | — + — | S3 |
Outcome
Circuits that are not self-synchronizing, together with logical coding and the definition of fixed bit-slot lengths, allow synchronization to be achieved. The start bit and stop bit are used for synchronization, and the check bit introduces redundancy to improve reception reliability.
Methods for coding digital signals
| This article is missing links to sources of information.
Information must be verifiable, otherwise it can be questioned and removed. |
Code formats
Each bit of a codeword is transmitted or written using discrete signals such as pulses. The way the source code is represented by certain signals is determined by the code format. A large number of formats are known, each of which has its own advantages and disadvantages and is intended for use in specific equipment.
- BVN format (no return to zero) naturally corresponds to the mode of operation of logic circuits. A single bit is transmitted within a cycle, the level does not change. A positive edge means a transition from 0 to 1 in the source code, a negative edge - from 1 to 0. The absence of edges indicates that the values of the previous and subsequent bits are equal. To decode codes in the BVN format, clock pulses are required, since its spectrum does not contain a clock frequency. The signal corresponding to the BVN format code contains low-frequency components (no drops occur when transmitting long series of zeros or ones).
- BVN-1 format (no return to zero with drop in transmission 1) is a kind of BVN format. Unlike the latter, the BVN-1 level does not transmit data, since both positive and negative drops correspond to single bits. Signal drops are formed during transmission 1. With transmission 0, the level does not change. Clock is required for decoding.
- BVN format −0 (no return to zero with dropoff when transmitting 0) is complementary to BVN-1 (slopes correspond to zero bits of the source code). In multitrack systems for recording digital signals, clock pulses must be recorded along with the code in the BVN format. A possible option is to record two additional signals corresponding to the codes in the BVN-1 and BVN-0 formats. In one of the two signals, the drops occur in each clock cycle, which makes it possible to obtain clock pulses.
- VN format (return to zero) requires the transmission of a pulse that occupies only a part of the clock interval (for example, half), with a single bit. With a zero bit, no pulse is generated.
- VN-P format (with active pause) means the transmission of a pulse of positive polarity with a single bit and negative - with a zero bit. A signal of this format has clock frequency components in its spectrum. It is used in a number of cases for data transmission over communication lines.
- DF-0 format (two-phase with a phase jump when transmitting 0) Corresponds to the presentation method in which the jumps are formed at the beginning of each measure. With single bits, the signal in this format changes with the clock frequency, that is, in the middle of each cycle, there is a level drop. When a zero bit is transmitted, a difference in the middle of the cycle is not formed, that is, there is a phase jump. The code in this format has the ability to self-synchronize and does not require the transmission of clock signals.
The direction of the differential when transmitting a 1 signal is irrelevant. Therefore, changing the polarity of the encoded signal does not affect the decoding result. It can be transmitted over balanced lines without a DC component. It also makes it easier to magnetically record. This format is also known as Manchester 1. It is used in the SMPTE time-address code, which is widely used for synchronizing audio and video media.
By Northwest (Serov, CMT)
Binary encoding
No return to zero
Potential encoding is also called non-return-to-zero (NRZ) encoding. When transferring zero, it transfers the potential that was set in the previous cycle (that is, does not change it), and when transferring one, the potential is inverted to the opposite. This code is called the potential one inversion code (NRZI).
NRZ
Potential NRZ code (inverted)
Two stably distinguishable potentials are used to convey ones and zeros:
NRZ (direct):
- bits 0 are represented by a zero voltage 0 (V);
- bits 1 are represented by the value U (B).
NRZ (inverted):
- bits 0 are represented by the value U (B);
- bits 1 are represented by 0 (V) zero voltage.
NRZI

Potential NRZI code
When transmitting a sequence of ones, the signal, unlike other coding methods, does not return to zero during a clock cycle. That is, the signal change occurs when the unit is transmitted, and the transfer of zero does not lead to a change in voltage.
Advantages of the NRZ method:
Ease of implementation.
The method has good error recognition (due to the presence of two sharply differing potentials).
The fundamental f0 has a sufficiently low frequency (equal to N / 2 Hz, where N is the bit rate of the discrete data transmission [bps]), which leads to a narrow spectrum.
Disadvantages of the NRZ method:
The method does not have the property of self-synchronization. Even in the presence of a high-precision clock generator, the receiver can make a mistake with the choice of the moment of data acquisition, since the frequencies of the two oscillators are never completely identical. Therefore, at high data exchange rates and long sequences of ones or zeros, a small clock frequency mismatch can lead to an error in a whole cycle and, accordingly, reading an incorrect bit value.
The second serious drawback of the method is the presence of a low-frequency component, which approaches a constant signal when transmitting long sequences of ones and zeros. Because of this, many communication lines that do not provide a direct galvanic connection between the receiver and the source do not support this type of coding. Therefore, in networks, the NRZ code is mainly used in the form of various modifications of it, in which both poor self-synchronization of the code and the problems of the constant component are eliminated.
Manchester coding

Manchester coding
In Manchester encoding, each bar is divided into two parts. Information is encoded by potential drops in the middle of each cycle. One is encoded by a drop from a low signal level to a high one, and zero is encoded by a reverse edge (according to the IEEE 802.3 standard, although according to DE Thomas, the coding is the opposite). At the beginning of each cycle, an overhead signal drop can occur if several ones or zeros are to be represented in a row. Since the signal changes at least once per transmission cycle of one data bit, the Manchester code has good self-synchronizing properties. The Manchester code does not have a constant component (it changes every cycle), and the fundamental harmonic in the worst case (when transmitting a sequence of ones or zeros) has a frequency of N Hz, and in the best case (when transmitting alternating ones and zeros) - N / 2 Hz, as and at NRZ. On average, the spectrum width for Manchester coding is twice as wide as for NRZ coding.
Differential Manchester Coding

Differential Manchester Coding
With differential Manchester coding, the signal level can change twice during a bit interval (transmission time of one bit). The level change is obligatory in the middle of the interval; this difference is used for synchronization. It turns out that when transmitting zero at the beginning of a bit interval, a level drop occurs, and when transmitting one, there is no such drop.
Trinary coding
(with return to zero)
That is, each bit is transmitted in 3 voltage levels. Therefore, it requires 2 times more speed than normal speed. This is a quasi-ternary code, that is, the signal changes between 3 levels.
Bipolar AMI Code

Bipolar AMI Code
AMI code uses the following bit representations:
- bits 0 are represented by zero voltage (0 V);
- bits 1 are represented alternately by the values -U or + U (B).
AMI code has good synchronization properties when transmitting series of units and is relatively simple to implement. The disadvantage of the code is the limitation on the density of zeros in the data stream, since long sequences of zeros lead to loss of synchronization. Used in data layer telephony when multiplexing streams are used.
HDB3
HDB3 corrects any 4 consecutive leading zeros to their original sequences. The rule for generating the code is as follows: every 4 zeros are replaced by 4 characters in which there is at least one V signal. To suppress the DC component, the polarity of the V signal is alternated during successive replacements. For replacement, two methods are used: 1) if before the replacement the source code contained an odd number of ones, then the sequence 000V is used, if even then 100V
V-signal of the unit prohibited for this polarity signal
The same as AMI, only the encoding of sequences of four zeros is replaced with the code -V, 0, 0, -V or + V, 0, 0, + V - depending on the previous phase of the signal.
MLT-3
MLT-3 Multi Level Transmission - 3 (multilevel transmission) - coding method using three signal levels. The method is based on cyclical level switching -U, 0, + U. The unit corresponds to the transition from one signal level to the next. Just like in the method NRZI when transmitting "zero", the signal does not change. In the case of the most frequent level switching (long sequence of ones), four transitions are required to complete the cycle. This allows the carrier frequency to be reduced by a factor of four relative to the clock frequency, which makes MLT-3 a convenient method when using copper wires as a transmission medium. The method was developed by Cisco Systems for use in copper-based FDDI networks known as CDDI. Also used in Fast Ethernet 100BASE-TX.
Tetra coding
Potential code 2B1Q

Potential code 2B1Q
The 2B1Q code transmits a couple of bits per bit interval. Each possible pair is assigned its own level of four possible levels of potential. Couple
00 corresponds to a potential of −2.5 V,
01 corresponds to -0.833 V,
11 - +0.833 V,
10 - +2.5 V.
1. Symmetric binary code.
2. The structure of the code.
3. Principles of converting parallel code to serial
In the process of encoding, the amplitude of each sample, quantized by the APM level, is represented as a binary sequence containing T characters (m-bit code combination). To determine the structure of the combination in the simplest case, you need to write down the amplitude of the AIM in binary code. reference I aim, expressed in steps of quantization.
In fig. 5.1 shows timing diagrams explaining the encoding process when using a five-bit binary code. The amplitude of the samples arriving at the input of the encoder, in this case, can take values in the range # aim = = 0-31 conditional quantization steps, and a digital signal with PCM is formed at the output of the encoder, which is a sequence of five-bit code combinations.
As shown above, for high-quality transmission of telephone signals with non-uniform quantization, it is necessary to use an eight-bit code (t = 8, and with uniform-12-bit (m = 12). In practice, binary codes of the following types are used: natural binary code, symmetric binary code, reflex binary code (Gray code).
Symmetric binary code is mainly used when coding bipolar signals (for example, telephone). Code structure and code table corresponding to the given code. For all positive samples, the sign symbol has a value of 1, and for negative samples, 0. For positive and negative samples of equal amplitude, the structures of the code combinations completely coincide (except for the sign bit), that is, the code is symmetric. For example, the maximum positive signal corresponds to the code 11111111, and the maximum negative one corresponds to 01111111. The absolute value of the quantization step is 6 = Ј / O rp / 2 m ~ 1.
Natural binary code is mainly used for coding unipolar signals. The structure of the code and the code table corresponding to this code are shown (when m-b). Obviously, the number of combinations of different structures is 256, with the minimum signal corresponding to the combination 00000000, and the maximum -11111111. The absolute value of the quantization step is 6 = £ / limit / 2 tons.
With the help of a natural binary code, it is possible to encode i-bipolar signals, providing their preliminary offset. In this case, obviously, the amplitude of the encoded samples changes, and the transition from the amplitude from * count H c> expressed in quantization steps, when using a symmetric code, to the amplitude of the same sample R "when using a natural code and vice versa, it can be done as follows:
| I „-128 at H a> \ 2 $, c (# n _127 at I n<128; Ян 1Я с +127 при Я с <0.
Natural and symmetric binary codes are the simplest. For both natural and symmetric codes, an error in one of the symbols can lead to significant signal distortion. If, for example, in a code combination of the form 11010011, an error occurred in the fifth bit, that is, a combination of 11000011 is accepted, then the sample amplitude will be less than the true value by 2 4 = 16 conditional quantization steps. The most dangerous, obviously, will be errors in the most significant digits (Fe »P; b
Consider the principles of constructing encoding and decoding devices, which can be linear and non-linear.
Linear coding refers to the encoding of a uniformly quantized signal, and nonlinear encoding of a non-uniformly quantized signal.
Rice. 5.1. Principles of converting parallel * code to serial (a) and
According to the principle of operation, encoders are divided into count-type encoders, matrix "weighting type, etc. In DSP, weighting encoders are most often used, among which the simplest is the bitwise weighting encoder (Fig. 5.20), at the outputs of which a natural binary code is formed. The principle of operation of such encoders is to balance the encoded samples with the sum of the reference currents (voltages) with certain weights. Scheme a bitwise weighting linear encoder contains eight cells (for t = * 8), providing the formation of the value of the corresponding bit (1 or 0). Each cell (except for the last one, corresponding to the least significant bit by weight) includes a CC comparison circuit (comparator) and a subtraction circuit (SV).
If, for example, a sample with an amplitude AND aim = 1746, then CCe forms P «-1 and a signal with an amplitude H "Aim= 1746-1286 = 466. At the output of CC7, we will receive Pt-O, and a signal with the same amplitude # d IM = 466 will arrive at the input of the third cell of the encoder. At the output of CCe, we will receive Pe- 1, and a signal with # ^ im * = will arrive at the input of the next cell
466-326 = 146, etc. As a result, a code combination of the form 10101110 will be formed (the first bit is the most significant by weight).
When coding bipolar signals in the encoder, it is necessary to have two reference shaping circuits (PE) to encode positive and negative samples.
In the process of decoding the signal, the m-bit code combinations are converted into AIM samples with the corresponding amplitudes. The signal at the output of the decoder can be obtained as a result of summing the reference signals (C / et) of those bits of the code combination, the value of which is 1. So, if the code combination 10101110 arrives at the input of the decoder, then the amplitude of the AIM sample at the output of the decoder # aim = 1286 + 325 + 86 + 45 + 23 = -1746.
The block diagram of the weighting type linear decoder is shown in Fig. 5.2K Under the influence of control signals coming from the generating equipment, the next eight-bit code combination is written into the shift register. After that, only those keys (Yun ... Kl ^) are closed that correspond to the digits having the value 1. As a result, the corresponding reference signals are sent to the input of the adder from the shaper of the reference signals (FE), as a result of which the AIM is formed at the output of the adder readout with a certain amplitude.
Obviously, if an error occurs in the process of transmitting a digital signal through a linear path in one (or more) code combination bit, then the amplitude of the sample at the output of the decoder will differ from the true value. If, for example, in the combination 10101110 an error occurs in P &, r * e *, the combination 10001110 arrives at the input of the decoder, then the amplitude of the sample at the output of the decoder is Yaim = 12864-86 + 46 + 26 ^ 1426, that is, 32 & is less than the true amplitude counting equal to 1746.
When constructing encoders and decoders, it is necessary to use FEs that form a set of reference signals, and the ratio between the values of two adjacent standards is 2 (16,26,46, ..., 1286). The general idea of constructing such devices is to use one highly stable reference signal source and a chain of circuits having a transmission coefficient / (= 1/2). Such circuits usually take the form of a matrix implemented on precision resistors of two denominations (R and 2R).
Non-linear encoders and decoders (non-linear codecs) are used in modern 1DSPs "providing coding and decoding of signals with an uneven quantization scale with an eight-bit code (t-8). For non-uniform quantization scale encoding, the following methods can be used:
analog companding, characterized by compression (compression) of the dynamic range of the signal before linear coding, and expansion (expansion) of the dynamic range of the signal after linear decoding;
non-linear coding, characterized by the coding of a signal in non-linear encoders "combining the functions of analog-to-digital conversion and compressor;
digital companding, characterized by coding a signal in a linear encoder with a large number of bits, followed by non-linear digital processing of the coding result.
With analog command (Fig. 5.24) at the input of the linear encoder (LK) and the output of the linear decoder (LD), the analog compressor (AK) and the expander (AE) are switched on, respectively, providing the corresponding nonlinear conversion of the analog signal (see Fig. 5.15).