Technologieswireless networks
After reading this chapter and completing the practice exercises, you will be able to:
· Talk about modern technologies of wireless networks;
· Present the history of the development of wireless networks and their benefits;
· Describe the technology of radio networks;
· To tell about radio networks of the 802.11 standard;
· Describe alternative radio network technologies (such as Bluetooth, HiperLAN and HomeRF Shared Wireless Access Protocol);
· Discuss wireless technologies using infrared radiation;
· Talk about microwave networks;
· Describe wireless networks using low earth orbit (LEO) satellites.
Wireless networks are an emerging technology of great interest for many reasons. The most obvious reason is that such networks provide the mobility of portable and handheld computing devices, allowing the user to forget about cables. Another reason is that wireless technologies are now more reliable and, in some situations, are cheaper to deploy than cable networks. There are several wireless media alternatives to cable for transmitting network packets: radio waves, infrared (IR) radiation, and microwaves (microwave waves). With all of these technologies, signals are transmitted over the air or in the atmosphere, making them a good alternative in cases where it is difficult or impossible to use a cable.
In this chapter, you will become familiar with many types of wireless network communications. First, you will learn which wireless networks are currently in use, and then read a brief history of such networks. T ix benefits. After a general description of networks using radio waves, it will be described in more detail about the widespread standard for wireless networks IEEE 802.11. You will also learn about alternative technologies of radio networks: Bluetooth, HiperLAN and HomeRF Shared Wireless Access Protocol, then technologies based on scattered infrared radiation will be described, which provide relatively secure wireless communications, and finally, it will be described how microwave technologies are used in networks based on terrestrial and satellite channels (including networks of wide-orbiting earth satellites).
Modern technologieswireless networks
Currently, the following technologies are used to create wireless networks:
· Technologies using radio waves;
· Technologies based on infrared radiation;
· Microwave (microwave) technologies;
· Networks based on low-orbit earth satellites (special space project using microwave waves).
Radio wave technologies are very widespread and represent a rapidly growing sector of wireless network communications. This also includes the 802.11 wireless networking standard, as well as alternatives to industry standards such as Bluetooth, HiperLAN, and NoteShared Wireless Access Protocol (SWAP).
Technologies based on infrared radiation are not as widespread as radio networks, however they have some advantages, since they allow creating relatively more secure wireless networks (since the signal is more difficult to intercept unnoticed). Both technologies (radio waves and infrared radiation) are used to organize communications over short distances within an office, building or between buildings.
Microwave (microwave) technologies are used for communication over long distances and can provide network communications between continents via satellites).
Networks based on low-orbit satellites are another type of wireless networks, on the basis of which at some point a "worldwide network" can be created, available in all parts of the planet.
All of these technologies will be discussed in this chapter. First, however, we will look at the history of wireless networks and learn about their benefits.
A brief history of wireless networksand their dignity
The history of wireless networks can be viewed formally and informally. The informal progenitor of wireless networks is amateur radio, whose operators obtain licenses from the FCC to transmit speech, Morse code, data, satellite and video signals using radio and microwave waves. The FCC views it as an important source of ideas and expertise for developing communications.
Note
Radio waves and microwaves are one of the ranges of the electromagnetic spectrum, which includes visible light, radio waves, infrared radiation, x-rays, microwaves (microwaves), and gamma rays. All of these are types of electromagnetic radiation that spreads in the Earth's atmosphere and in space. It has both the properties of a wave and the properties of a particle. Additional information on the spectrum of electromagnetic waves can be found at
http:// imagine. gsfc. nasa. gov/ docs/ science/ knowJ1/ emspectrum. html andhttp:// imagine. gsfc. nasa. gov/ docs/ science/ knowJ2/ emspectrum. html.
In the 1980s, licensed radio amateurs received approval from the FCC to transmit data on multiple radio frequencies in the 50.1-54.0 MHz (low band) to 1240-1300 MHz (high band) bands. Most people are familiar with these frequencies because they are used for the transmission of music by AM and FM radio stations. These frequencies represent only a small fraction of the possible radio frequencies on which signals can be transmitted. The basic unit of measurement for radio frequency is hertz (Hz)(Hertz (Hz)). In technology, one hertz corresponds to one period of an alternating voltage or radiated signal per second.
Note
Radio frequencies represent the range of waves above 20 kHz through which an electromagnetic signal can be radiated into space.
It has been long since IBM built the personal computer in the early 1980s before radio amateurs networked personal computers using radio waves (typically in the higher bands 902-928 MHz and 1240-1300 MHz). To do this, they created a device called a terminal node controller (TNC). This device was placed between the computer and the transceiver and was used to convert the computer digital signal into an analog signal, amplified by the transceiver and emitted through the antenna. The resulting technology was called packet radio. The discovery by radio amateurs that packet radio works well at 902 MHz and above was soon analyzed by commercial wireless service providers. In 1985, the FCC authorized commercial use in wireless computer networks with a frequency for industrial, scientific, and medical applications (Industrial, ScietfJtitle and Medical, ISM), which can be used for low-power unlicensed public communications on fixed frequencies "in the range of 902 MHz to 5.825 GHz. In 1996, the Telecommunications Congress prepared the next phase in wireless development! communications, securing the concept of "wireless node (location)" and setting standards for it, as well as creating incentives for the further development of telecommunication technologies, including wireless communications (additional information can be found at www.fcc. gov / telecom . html). Shortly thereafter, the IEEE created the 802.11 Wireless Standards Group, which was responsible for the first 802.11 standard, established in 1997. Currently, wireless networks are being developed and implemented to meet many needs, including the following:
· Implementation of communications in those areas where it is difficult to deploy a cable network;
· Reduced deployment costs;
· Providing "random" access to those users who cannot be tied to a specific cable connection;
· Simplification of the procedure for creating networks in small and home offices;
Providing access to data required in a specific configuration
Why is it not always possible to use cable networks?
In some situations, it is difficult and even impossible to deploy a cable network. Consider this scenario. The two buildings need to be connected by one network, however, an federal highway passes between them. In this case, there are several ways to organize the network. First, it is possible to dig a trench under the highway, which will require high costs and disruptions in traffic caused by digging trenches, laying cables, digging trenches and completely rehabilitating the road. Second, you can create a regional network linking the two buildings. Buildings can be connected to T-1 lines or to a regional Optical Ethernet network using the services of the public network owner or the local telephone company. At the same time, the costs will be less than when laying a new cable, however, the lease of telecommunication lines will require constant deductions. Third, a wireless network could be deployed, which would require a one-time hardware expense and would also incur recurrent network management costs. However, all these costs are likely to be most justified when considered over long periods of time.
Let's consider another scenario. A large office tenant needs to deploy a network for 77 employees. The owner of the premises prohibits the laying of a permanent cable system. This premise suits the tenant in every sense, in addition, the payment for it is lower than in other alternative options. The solution to the problem is to create a wireless network.
And finally, the third scenario. The public library is located in a historic location. Although the library is owned by the city, strict public and private contracts prevent library management from obtaining the necessary permission to lay network cables. The library has lagged behind in the creation of an electronic catalog of books for many years, since it cannot network the computers of its employees and the help desk for its customers. Therefore, the management of the library can solve their problems by deploying a wireless network that allows you to preserve the integrity of the building and not violate any contracts.
Saving money and timewhen using wireless networks
The cost and time of setting up a wireless network can be less than deploying a cable network. For example, older buildings often contain hazardous materials, such as old production mines that contain negligible amounts of chlorine from air ducts and asbestos. Since the mines are not used, they can simply be bricked up. Or, an expensive hazardous materials disposal program could be launched so that these mines can be used to run network cables. In such a situation, it is much cheaper to brick the mines and deploy a wireless network instead of a cable.
Consider a case where one university needed a working network because large funds were invested in its development. The university invited an expensive consulting company, which provided
the project has five people and organized 18 new jobs. A few days before work began, the university realized that there were no network connections for new employees and consultants. Laying new cables is expensive and impossible in the next few months as the university's IT department is already overburdened with work. A way out was found in the form of a wireless network that can be deployed in record time.
Unlimited network access
Some computer users need access to the network from almost anywhere. Consider, for example, a large automotive parts warehouse that needs to be regularly audited using networked barcode measures. The wireless network gives users of these scanners unlimited access as they are not tied to cable connections. Another example A doctor in a hospital may carry a small laptop computer with a wireless adapter that can be used to update medical records, order test orders, or organize patient care.
Simplifying networking for newbies
In the field of computerization of small or home offices with a wireless network, a cut above cabling. Networks of these offices can be very unsatisfactory as they are usually set up by non-professionals. As a result, the wrong cable type may be selected. The cable can pass by sources of radio interference and electromagnetic radiation, or it can be damaged (for example, by passing under a chair, table, or in a doorway). Therefore, the user of such an office may waste his time unproductively looking for network inoperability. In such a situation, the wireless network may be easier to install and operate. Typically, in many online computer stores, small and home office users are asked if they would like to purchase wireless devices for networking between purchased computers.
The advantage of wireless networks for this class of users is that the cost of wireless devices is currently quite moderate. Wireless networking combined with automatic IP address assignment in Windows 2000 and Windows XP allows you to create a complete home network with little or no experience.
Improving data access
Wireless networks can significantly improve access to some types of data and applications. Consider, for example, a large university with ten full-time auditors who visit several departments (and sites) every day and need access to financial data, reports, and other information available in those departments. With a laptop computer equipped with a wireless network adapter, the auditor can easily move between sites and have constant access to any financial documents. As another example, consider a chemical engineer working at various points in a chemical plant. At one point, he can observe the data during some reaction of the production cycle. At another point, he may need a chemical nomenclature to ensure that the necessary ingredients are available to start another production process. At a third point, this engineer can refer to the company's online research library. Wireless access will allow him to easily cope with all these tasks.
Technology Supporting Organizationswireless networks
There are several organizations promoting wireless networking. One such organization, which is a valuable source of information on wireless networks, is Wireless LAN Association (WLANA). This association is formed by manufacturers of wireless devices, as well as interested companies and organizations, including Alvarion, Cisco Systems, ELAN, Intermec, Intersil, Raylink and Wireless Central. Complete Practice 9-1 and familiarize yourself with situations in which you can use wireless LANs and WLANA resources.
WINLAB (Wireless Information Network Laboratory) is a wireless research center based at Rutgers University, supported by several universities. WINLAB is sponsored by the National Science Foundation and has been in operation since 1989. In Practice 9-2, you will learn about the latest research carried out by WINLAB.
Radio network technology
Network data is transmitted using radio waves just like a local radio station, however, waves are used for network applications
much higher frequencies. For example, a local AM (medium and long wave) radio station may broadcast at 1290 kHz, since the frequency range for AM broadcast is 535-1605 kHz. The frequency range for FM broadcasting (VHF) has the boundaries of 88-108 MHz. In the United States, network signals are transmitted at higher frequencies in the 902-928 MHz, 2.4-2.4835 GHz, or 5-5.825 GHz bands.
Note
Each of the mentioned frequency intervals is also referred to as a band: 902 MHz band, 2.4 GHz band and 5 GHz band. The 902 MHz band is primarily used in older non-standard wireless devices and is not covered further in this book.
In radio networks, the signal is transmitted in one or more directions, depending on the type of antenna used. In the example shown in fig. 9.1, the signal is directional because it is transmitted from an antenna located in one building to an antenna located in another building. The wave has a very short length and low power (unless the carrier has a special license from the FCC for multi-watt communications), that is, it is best suited for line-of-sight transmissions(line-of-sight transmission) with a short range.
In line-of-sight transmission, the signal is transmitted from one point to another, following the curvature of the Earth, rather than being reflected from the atmosphere, crossing countries and continents. The disadvantage of this type of transmission is the presence of obstacles in the form of high elevations on the surface of the Earth (for example, hills and mountains). A low-power (1 - 10 W) radio signal can transmit data at speeds from 1 to 54 Mbps and even higher.
To transmit packets in the equipment of wireless radio networks, spread spectrum technology is most often used, when one or more adjacent frequencies are used to transmit a signal with a higher bandwidth. The spread spectrum frequency range is very high: 902-928 MHz and much higher. Spread spectrum communications typically provide data transfer rates of 1-54 Mbps.
Communications using radio waves can save money in cases where it is difficult or very expensive to lay a cable. Radio networks are especially useful when using laptop computers that move frequently. Compared to other wireless technologies, radio networks are relatively inexpensive and easy to install.
The use of radio waves in communications has several disadvantages. Many networks transmit data at speeds of 100 Mbps or higher to organize high-speed communications when sending large amounts of traffic (including large files). Radio networks cannot yet provide communications at such a speed. Another disadvantage is that some wireless frequencies are shared between radio amateurs, the military, and cellular network operators, resulting in various sources of interference at these frequencies. Natural obstacles (eg hills) can also reduce or distort the transmitted signal.
One of the main technologies of radio networks is described by the IEEE 802.11 standard. Other technologies are also used, including Bluetooth, HiperLAN, and HomeRF Shared Wireless Access Protocol (SWAP). All of these technologies will be discussed in the following sections of this chapter.
IEEE 802.11 radio networks
Various types of radio networks are used to implement wireless communications, however, in terms of compatibility and reliability, the IEEE 802.11 standard has significant advantages. Many wireless users use devices that conform to this standard because they do not involve unstandardized communications (especially in the low and slow 902-928 MHz range typical of older wireless devices) and 802.11 devices from different manufacturers are interchangeable. These devices meet an open standard, so different models can communicate with each other, and it is easier to implement new wireless functions in them. Therefore, it is important for a wireless designer to understand the IEEE 802.11 standard and how devices that conform to that standard work.
The IEEE 802.11 standard is also called the IEEE Standard for Wireless LANledium Access (MAC) and Physical Layer (PHY) Specifications. This standard applies to fixed and mobile stations for wireless communications. A stationary station is called a station that does not move, a mobile station is called a station that can move quickly, or slowly, like a walking person.
The 802.11 standard provides for two types of communications. The first type is synchronous communication, when data transfer occurs in separate blocks, the beginning of which is marked with a start bit, and the end is marked with a stop bit. The second type includes communications, it carries out within a certain time frame, when the signal is given a certain one to reach the destination point, and if the signal does not fit in> that time, then it is considered lost or distorted. Timing constraints make 802.11 similar to 803.11, in which the signal must also reach a specified target node within a specified time. The 802.11 standard provides support for network management services (example, SNMP). Network authentication is also provided, the 802.11 standard is focused on the use of the Link and Physical layers of the OSI model. The MAC and LLC sublayers of the Link Layer define standards for the access method (which will be discussed later in this chapter), addressing, and data verification methods using checksums (CRCs). At the Physical Layer, the 802.11 standard defined the data transmission rates at given frequencies. Methods (such as spread spectrum technologies) are also provided for transmitting digital signals using radio waves and infrared radiation.
In terms of the working environment, the 802.11 standard distinguishes between indoor (indoor) and outdoor (bark) wireless communications. Room communications can, for example, be carried out in an office building, an industrial area, a store or a private house (that is, wherever they do not extend beyond a single building). Outdoor communications can be performed within a university campus, sports field, or parking lot (i.e., where information is transmitted between buildings). Next, you will learn about the following aspects related to the functioning of 802.11 wireless networks:
· Wireless components used in IEEE 802.11 networks;
· Methods of access in wireless networks;
· Ways of detecting errors in data transmission;
· Communication rates used in IEEE 802.11 networks;
· Security methods;
· Use of authentication when the connection is broken;
· Topology of IEEE 802.11 networks;
· Use of multi-cell wireless local area networks.
Wireless components
Three main components are usually involved in the implementation of wireless communications: a board that performs the functions of a receiver and transmitter (transceiver), an access point and antennas.
The transceiver board is called wireless adapter(wireless NIC, WNIC), which operates on the Physical and Data Link layers of the OSI model. Most of these adapters are compatible with the Network Interface Specification, NDIS (Microsoft) and Open Datalink Interface, ODI (Novell). As you already know from chapters 5, both of these specifications allow multiple protocols to be transmitted over the network and are used to communicate a computer and its operating system with a WNIC adapter.
Access subtle(access point) is some device connected to a cable network and providing wireless data transfer between WNIC adapters and this network. As stated in chapter 4, the access point is usually a bridge. It can have one or more network interfaces of the following types, allowing it to be connected to a wired network:
100BaseTX, 100BaseT, 100BaseT2 and 100BaseT4;
Advice
Currently, some wireless network providers offer access points with router capabilities.
Antenna Is a device that sends (radiates) and receives radio waves. Both WNICs and access points are equipped with antennas. Most wireless antennas are either directional or omnidirectional.
Advice
When purchasing 802.11 devices, see if they are certified by the Wireless Ethernet Compatibility Alliance (WECA), which includes over 150 wireless device companies. More information on this union can be found on the website www. wi- fi. com.
Directional antenna
A directional antenna sends radio beams in one main direction usually can amplify the radiated signal more than an omnidirectional antenna. The magnitude of the amplification of the emitted signal is called gain(gain). In wireless networks, directional antennas are usually used to transmit radio waves between antennas located on two buildings and connected to access points (Fig.9.2). strong signal (with high gain) in one direction. Considering fig. 9.2, please note that in fact the antenna radiates a signal not only in one direction, since part of the signal is scattered along the sides.

Note
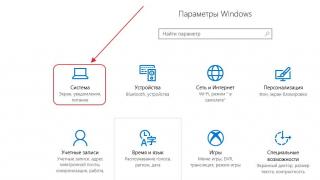
Complete Practice 9-3 to familiarize yourself with the components of wireless networks. In addition, Practice 9-4 and 9-5 show you how to install the WNIC adapter on Windows 2000 and Windows XP Professional. In Practice 9-6, you will learn how to install an adapter there on a Red Hat Linux system. 7. x.
Omnidirectional antenna
An omnidirectional antenna emits radio waves in all directions. Since the signal is scattered more than when using a directional antenna, it is likely to have a lower gain as well. In wireless networks, omnidirectional antennas are often used in indoor networks, in which users are constantly mixed and signals must be transmitted and received in all directions. In addition, in such networks, as a rule, the signal gain is not required to be as high as in an outdoor network, since the distance between wireless devices in a room is much shorter. In fig. 9.3 shows a wireless network using omnidirectional antennas
Rice. 9.3. Omnidirectional antennas
The WNIC adapter for handheld devices (such as laptops, PDAs, and tablets) can be equipped with a small omnidirectional circuit antenna. The LAN access point can have a detachable omnidirectional antenna or an antenna that connects to the access point using a cable. An access point for an outdoor network connecting two buildings usually has a high gain antenna that connects to the access point via a cable.
Wireless Access Methods
The 802.11 standard provides for two access methods: priority access and carrier sense multiple access with collision avoidance. Both of these methods work at the Link Layer.
Using access in order of priority(the priority-based access point also acts as a point coordinator, which sets the period without conflicts during which stations) (other than the coordinator itself) cannot transmit without first contacting the coordinator. During this period, the coordinator interrogates the stations in turn. If a station sends a short packet indicating that it needs to be interrogated because it has a message to transmit, the point coordinator places its questionnaire on this station. If a station is not interrogated, the coordinator sends it a signaling frame indicating how long to wait until the next period without collisions. In this case, the stations included in the questionnaire, in turn, receive the right to carry out communications. When all these stations have received the opportunity to transmit data, the next period without the occurrence of conflicts is immediately set, during which the coordinator again polls and indicates the station, determining the need to include the stations waiting for the transmission opportunity in the questionnaire.
Priority access is intended for communications that require low latency in the transfer of information. These types of communications typically include voice and video transmissions and video conferencing — the applications that work best on a continuous basis. According to the 802.11 standard, access in the priority row is also called point coordination function
More often used in wireless networks multiple access controlLem Carrier and Conflict Prevention(Carrier Sense Multiple Access with Collision Avoidance, CSMA / CA), also called distributed coordination functions(distributed coordination function). In this case, the station awaiting a transmission opportunity listens on the communications frequency and determines whether it is busy by checking the level of the Receiver Signal Strength Indicator (RSSI). At the 14th moment, when the transmitting frequency is free, conflicts are most likely between two stations, which will simultaneously want to start transmitting. As soon as you release the transmitting frequency! each station waits for a few seconds (the number of which is determined by the DIPS parameter) to ensure that the frequency remains unoccupied. DIFS is an abbreviation for Distributed coordination function "s In-tra-Frame Space, which defines a predefined mandatory latency (latency).
If the stations wait for the time specified by the DIFS interval, the likelihood of a conflict between the stations decreases, since for each station requiring transmission, a different delay (backoff) value is calculated, after which the station will again check that the transmitting frequency is busy. If the frequency remains unoccupied, the station with the minimum backoff time starts transmitting. If the frequency is occupied, then the station requiring transmission waits until the frequency becomes free, after which it remains idle for the already calculated backoff time.
When determining the grace period, the duration of the predetermined time interval is multiplied by a random number. A time slot is a value stored in a Management Information Base (MIB) held at each station. The value of the random number ranges from zero to the maximum collision window size, which is also stored in the station's control information base. Thus, a unique backoff time is defined for each station waiting to be transmitted, which allows stations to avoid collisions.
Handling data transmission errors
Wireless communications are affected by weather conditions, sun glare, other wireless communications, natural obstacles, and other sources of interference. All of this interference can interfere with the successful reception of data. 802.11 standard provides automatic request forrepetition(automatic repeat-request, ARQ), which takes into account the possibility of transmission errors.
If, when using ARQ requests, the station that sent the packet does not receive an acknowledgment (ACK) from the target station, then it automatically repeats the transmission of the packet. The number of retries made by the transmitting station before it determines that the packet cannot be delivered depends on the size of the packet. Each station stores two values: the maximum short burst size and the long burst size. In addition, there are two additional parameters: the number of retries for sending a Short packet and the number of retries for a long packet. Analysis of all these values allows the station to decide to stop retransmissions of a certain packet.
As an example of error handling using ARQ requests, consider a station for which a short packet has a maximum length of 776 bytes, and the number of retries for a short packet is 10. Suppose the station transmits a 608 byte packet but does not receive an acknowledgment from the receiving station. In this case, the transmitting station will retransmit this packet 10 times in the absence of confirmation. After 10 unsuccessful attempts (i.e. without receiving an acknowledgment), the station will stop transmitting this packet.
Transfer rates
The transmission rates and corresponding frequencies of 802.11 networks are defined by two standards: 802.11a and 802.1111b. The communication speeds specified in these standards refer to the Physical Layer of the OSI model.
For wireless networks operating in the 5 GHz band, the 802.11 standard provides the following data rates:
6 Mbps;
24 Mbps;
9 Mbps;
· 36 Mbps; "
12 Mbps;
48 Mbps;
· 18Mbps;
· 54 Mbps.
Note
All 802.11a-compliant devices must support 6, 12, and 24 Mbps. The 802. Pa standard is implemented at the Physical layer of the OSI model and for the transmission of information signals using radio waves provides for the use of orthogonal multiplexing of channels separated byfrequency(Orthogonal Frequency Division Multiplexing, OFDM). This multiplexing technique divides the 5GHz frequency range into 52 subcarriers (52 subchannels). Data is split between these subcarriers and transmitted simultaneously across all 52 subcarriers. These transmissions are called parallel transmissions. Four subcarriers are used to control communications and 48 are used to carry data. The 802.11b standard is used in the 2.4 GHz frequency range and provides the following communication rates: "
1 Mbps;
10Mbps;
2 Mbps;
11Mbps.
Note
At the time of this writing, the approval of the extension of the 802.11b standard, called 802.11d, was expected. The 802.11d standard allows data transmission in the 2.4 GHz range at speeds up to 54 Mbps.
The 802.11b standard uses direct sequence modulationand spread spectrum(Direct sequence spread spectrum modulation, DSSS), which is a method of transmitting information signals using radio waves and belongs to the Physical layer. With DSSS modulation, data is spread across multiple channels (up to 14 in total), each of which occupies a 22 MHz bandwidth. The exact number of channels and their frequencies depends on the country in which communications are carried out. Canada and the United States use 11 channels in the 2.4 GHz band. In Europe, the number of channels is 13, with the exception of France, where only 4 channels are used. The information signal is transmitted alternately to the channels and amplified to values sufficient to exceed the level of interference.
At the time of this writing, 802.11a offers faster speeds than 802.11b. However, the increase in speed is achieved at the expense of shorter working distances. Currently, 802.11a devices can transmit data over distances of up to 18 m, while 802.11b devices can operate at distances up to 90 m. This means that if you are using 802.11a devices, then to increase the total working area devices, you will need to purchase more hotspots.
In addition to speed, the advantage of the 802. Pa standard is that the full range of frequencies in the 0.825 GHz range is almost twice the range of frequencies in the 0.4835 GHz range for the 802.11b standard. This means that much more data can be transmitted during the broadcast, since the wider the frequency interval, the more traffic channels through which the binary data is transmitted.
For applications that require more bandwidth (such as voice and video), plan to use 802. Pa devices. Also, consider using these devices in situations where there are many users within a small area (such as a computer lab). Higher bandwidth will enable all clients on the network to perform better and faster.
The scope of 802.11b devices covers those configurations where the availability of high bandwidth is not so important (for example, for communications primarily intended for data transmission). In addition, 802.11b is well suited for low-budget projects as it requires fewer access points than 802.11a. This is because 802.11a provides a wider operating area (up to 90 m versus 18 m allowed by 802.11a). Currently, 802.11b is used more often than 802.11a because networks based on it are cheaper to implement, and there is a wider range of devices designed for it on the market (which, moreover, were launched earlier). The characteristics of the 802.11a and 802.11b standards are presented in table. 9.1.
Table 9.1. Features of 802.11a and 802.11 standardsb
|
802.11 a |
802.11b |
|
|
Working frequency | ||
|
Working speeds (band passcania) |
6, 9, 12, 18, 24, 36, 48, 54 Mbps |
1, 2, 10, 11 Mbps |
|
The communi methodkation |
Orthogonal Frequency Division spread spectrum multiplexing (OFDM) |
Direct sequence modulation DSSS |
|
Maximum working distance at present | ||
|
Real costzations |
Relatively high due to the need for additional access points |
Relatively low due to the use of a small number of access points |
Security methods,
Security is just as important on wireless as it is on cable. The 802.11 standard provides two security mechanisms: open systems authentication and shared key authentication. With open system authentication, any two stations can authenticate each other. The transmitting station simply sends a request to the target station or access point: for authentication. If the target station confirms the request, it means that the authentication is complete. This authentication method is not very secure, and you should be aware that many manufacturers use it by default.
Much better protection is provided by shared key authentication(shared key authentication) because it implements Wired Equivalent Privacy (WEP). With this security mechanism, two stations (for example, a WNIC adapter and an access point) share the same encryption key generated by the WEP services. The WEP encryption key is a 40- or 104-bit key with the addition of a checksum and initiating information, which as a result determines the total key length equal to 64 or 104 bits.
With Shared Key Authentication and WEP, one station asks another for authentication. The second station sends back some special text request. The first station encrypts it using the WEP encryption key and sends the encrypted text to the second station, which decrypts it using the same WEP key and compares the received text with the original text request sent. If both texts match, the second station authenticates the first and communication continues.
Using disconnect authentication
Another function of authentication is to terminate the connection after the communication session ends. The disconnect authentication process is important because two communicating stations cannot be accidentally disconnected by another unauthenticated station. The connection between two stations is dropped if one of them sends an authentication denied notification. In this case, communications are instantly terminated.
Network topologiesIEEE 802.11
There are two main topologies provided by the 802.11 standard. The simplest is topology with a set of independent core services(Independent Basic Service Set (IBSS) topology), formed by two or more wireless stations that can communicate with each other. This type of network is somewhat unpredictable, as new stations often appear unexpectedly. The IBSS topology is formed by arbitrary peer-to-peer (peer-to-peer) communications between the WNICs of individual computers (Figure 9.4).

Compared to IBSS topology, extended topology(Extended service set (ESS) topology) has a large service area because it has one or more access points. Based on the ESS topology, you can create a small, medium or large network and it is significant! expand the area of wireless communications. The ESS topology is shown in Fig. 9.5.
If you are using 802.11 compliant devices, the network and IBSS topology are easy to convert to an ESS topology. However, networks with different topologies should not be located nearby, since peer-to-peer IBSS communications are unstable in the presence of access points used in the ESS network. Communication in the ESS network can also be disrupted. "
Advice
For more information on the IEEE 802.11 standard, visit the IEEE website at www. ieee. org. A complete copy of this standard can be ordered from this site.

Multi-cell wireless LANs
When two or more access points are used in an ESS-based network, the network becomes multi-cell wireless localenew network(multiple-cell wireless LAN). The broadcast area around some point in such a topology is called cell(cell). If, for example, a room network inside a building has five access points, then this network has five cells. In addition, if all five cells are configured in the same way (have the same operating frequency, the same baud rate and general security parameters), then a personal computer or hand-held device equipped with a WNIC adapter can be moved from one cell to another. This process is called roaming(roaming).
As an example of roaming in a wireless ESS topology, consider a university department that has deployed a wireless network that has five access points associated with cells I through V.1 Cell I may belong to a library. Cells II and III can cover the area of the teaching offices. Slot IV can be located in the administration office, and slot V can be located in the training laboratory. If all cells are configured the same, any student, faculty, or office worker can move a laptop equipped with a WNIC adapter from one cell to another while still maintaining access to the faculty's network. Although the 802.11 standard does not provide a specification for a roaming protocol, wireless manufacturers have developed one such protocol called Inter- Access Point Protocol (IAPP), which basically meets this standard. IAPP allows a mobile station to move between cells without losing network connectivity. To ensure communications with IAPP roaming, we encapsulate the UDP and IP protocols.
Note
As you already know from chapters 6, User Datagram Protocol (UDP) is a connectionless protocol that can be used in conjunction with IP instead of TCP, which is a connection-oriented protocol.
The IAPP protocol allows existing access points to be notified of a new device connecting to the network, and also allows adjacent access points to exchange configuration information with each other. In addition, the protocol allows some access point communicating with the mobile station to automatically transmit information about the original connection (including any data pending to be sent to another access point in cases where the mobile station moves from the cell served by the first access point to the cell, connected to the second access point.
Alternative radio network technologies
The most common radio wave communication technologies include the following alternative technologies to the IEEE 802.11 standard:
HomeRF Shared Wireless Access Protocol (SWAP).
Each technology listed is a wireless specification and is supported by specific vendors. All of these technologies are discussed in the following sections.
Bluetooth
Bluetooth – is a wireless communication technology described by the Bluetooth Special Interest Group. This technology has attracted the attention of manufacturers such as 3Com, Agere, IBM, Intel, Lucent, Microsoft, Motorola, Nokia and Toshiba. It uses frequency hopping in the 2.4 GHz (2.4–2.4835 GHz) band allocated by the FCC for unlicensed ISM communications2. The frequency hopping method involves changing the carrier frequency (one of 79 frequencies is selected) for each transmitted packet. The advantage of this method is to reduce the likelihood of mutual interference in cases of simultaneous operation of several devices.
When using multi-watt communications, Bluetooth technology allows data transmission over distances of up to 100 m, but in practice most Bluetooth devices operate at a distance of up to 9 m. Usually, asynchronous communications at a speed of 57.6 or 721 kbps are used. Bluetooth devices that provide synchronous communications operate at 432.6 Kbps, but such devices are less common.
Bluetooth technology uses timeslot duplexchanneling(time division duplexing, TDD), in which packets are sent in opposite directions using time slots. One transmission cycle can employ up to five different time slots, so that packets can be transmitted and received simultaneously. This process is similar to duplex communications. Up to seven Bluetooth devices can communicate at the same time (some manufacturers claim that their technology can connect to eight devices, but this does not meet specifications). When devices exchange information, one of them is automatically selected as the master. This device defines control functions (such as time slot synchronization and forwarding control). In all other aspects, Bluetooth communications resemble a peer-to-peer network.
Advice
Learn more about Bluetooth technology on the official website at www. bluetooth. com. Complete Practice 9-7, which introduces the Bluetooth website, which describes Blue-tooth applications for wireless communication with accessibility.
HiperLAN
Technology HiperLAN was developed in Europe and is currently in a second version called HiperLAN2. This technology uses the 5 GHz band and delivers data rates up to 54 Mbps. In addition to speed, HiperLAN2 also benefits from Ethernet and ATM communication compatibility.
HiperLAN2 technology supports Data Encryption Standard (DES) – a data encryption standard developed by the National Institute on Standards and Technology (NIST) and ANSI. It uses a public encryption key that can be viewed by all network stations, as well as a private one. (private) key assigned only to transmitting and receiving stations. Both keys are required to decrypt the data.
HiperLAN2 technology provides quality of service (QoS) by providing a guaranteed level of communication for different classes of service (for example, voice or video). This is possible due to the fact that the access points are centrally controlled by the wireless! communications, and schedule all sessions of information transmission.
HiperLAN2 operates in two modes. Direct mode (directlmode) is a peer-to-peer topology (similar to 1B58 topology in 802.11 networks) that is generated only by communicating stations. Another mode is called centralized mode because it is implemented in large networks where there are access points that concentrate and control network traffic. The communication method for both modes is Time Division Duplex (TDD), the same technology used in Bluetooth.
Advice
For a closer look at HiperLAN2, visit the website www. hiperian2. com.
HomeRF Shared Wireless Access Protocol (SWAP)(HomeRF Wireless Sharing Protocol) is a technology supported by companies such as Motorola, National Semiconductor, Proxim, and Siemens. This
the technology operates in the 2.4 GHz band and provides network speeds up to 10 Mbps. It uses CSMA / CA as an access method (like the 802.11 standard) and is intended for home networks, where data, voice, video images, multimedia streams and other information are transmitted.
An example of a typical use of HomeRF SWAP technology is a wireless network that connects multiple personal computers and provides them with Internet access. Another area of application is the implementation of wireless connections for entertainment centers (for example, to communicate with each other several televisions and stereos). The HomeRF SWAP network can link multiple phones together. It can also be used to provide communication between home control devices (lighting, air conditioners, kitchen units, etc.). For security, HomeRF SWAP networks use 128-bit data encryption and 24-bit network IDs.
At the time of this writing, HomeRF SWAPS technology was under development, providing communications at a speed of 25 Mbps. The creators of this technology are striving to integrate it into televisions and media servers in order to expand the capabilities of complex video systems.
(Advice)
You can learn more about HomeRF SWAP on the website www. homerf. org.
Network technologies usinginfrared radiation
Infrared (IR) radiation (infrared) can be used as a transmission medium for network communications. You are familiar with this technology with TV and stereo remote controls. IR radiation is an electromagnetic signal, similar to radio waves, but its frequency is closer to the range of visible electromagnetic waves, called visible light.
Infrared radiation can travel either in one direction or in all directions, with a light-emitting diode (LED) for transmitting and a photodiode for receiving. IR radiation belongs to the Physical layer, its frequency is 100 GHz - 1000 THz (terahertz), and the electromagnetic wavelength is in the range from 700 to 1000 nanometers (nm, 10 ~ 9).
Like radio waves, infrared radiation can be an inexpensive solution when cabling is impossible or when there are mobile users. Its advantage is that it is difficult to intercept the PC signal unnoticed. Another advantage is the resistance of the ICC signal to radio and electromagnetic interference. However, this communication environment also has a number of significant disadvantages. First, with directional communications, the data transfer rate does not exceed 16 Mbit / s, and with omnidirectional communications, this value is less than 1 Mbit / s. Secondly, IR radiation does not pass through the walls, which is easy to verify by trying to control the TV with a remote control from another room. On the other hand, this disadvantage turns into an advantage, since due to the limited area of distribution, communications using infrared signals are made more secure. Thirdly, infrared communication can be interfered with by strong ones.
Advice
Infrared technologies can use access points to expand the work area and create large networks.
When transmitting information using diffused infrared radiation, the sent infrared signal is reflected off the ceiling, as shown in Fig. 9.6. For such communications, there is the IEEE 802 standard, which provides for operation at a distance of 9 to 18 m, depending on the ceiling height (the higher the ceiling, the smaller the network coverage area). For scattered infrared radiation, this standard specifies data rates of 1 and 2 Mbps. The wavelengths of the scattered IR signal used in the 802.11R standard are in the 850-950 nm range (out of all the 700-1000 nm IR range). By comparison, visible light has a wavelength range of approximately 400-700 Megahertz. The maximum optical radiated signal power according to the 802.11R standard is 2 W.
Advice
Although scattered infrared signals are not susceptible to radio and electromagnetic interference, windows in buildings can cause interference because these signals are sensitive to strong light sources. Consider the presence of windows when designing a wireless network using stray infrared radiation.
The signaling method used by the IEEE 802.11R standard is called pulse-phase modulation(Pulse position modulation, PPM). According to this method, the binary value of a signal is associated with the location of the pulse at a set of possible positions in the electromagnetic spectrum. For communications at 1 Mbps, the 802.11R standard provides sixteen possible pulse positions (16-PPM), with each position representing four bits. With communications at 2 Mbit / s, each pulse represents two digits, and there are only four possible pulse positions (4-PPM). A pulse at a certain position indicates that some value is present, and the absence of a pulse means that there is no value. PPM is a character coding technique that resembles binary coding in that it uses only ones and zeros.

Microwave networking technologies
Microwave systems operate in two modes. Terrestrial microwave channels transmit signals between two directional dish-shaped parabolic antennas (Figure 9.7). Such communications operate in the 4-6 GHz and 21-23 GHz frequency bands and require the carrier to obtain a license from the Federal Communications Commission (FCC).
Satellite microwave systems transmit a signal between three antennas, one of which is located on an Earth satellite (Figure 9.8). The satellites in such systems are in geosynchronous orbits 35,000 km above the Earth. For an organization to use such communication technology, it must either launch a satellite or lease a channel from a company that provides such services. Due to long distances, transmission delays are 0.5 to 5 seconds. Communications are carried out in the 11-14 GHz frequency range, which require licensing.
|
|
|
|
Like other wireless media, microwave technology is used when cabling is too expensive or when cabling is not possible. Ground-based microwave channels can be a good solution when laying communications between two large buildings in a city. Satellite communication systems are the only possible way to connect networks located in different countries or on different continents, but this solution is very expensive.
Microwave communications have a theoretical bandwidth of up to 720 Mbit / s and higher, but in practice, speeds are currently usually in the range of 1-10 Mbit / s. Microwave communication systems have some limitations. They are expensive and difficult to deploy and operate. Microwave communications can be degraded by atmospheric conditions, rain, snow, fog, and radio interference. Moreover, the microwave signal can be intercepted, therefore, when using this transmission medium, authentication and encryption means are especially important.
Wireless networks basedlow-earth satellites
The orbits of the communications satellites are approximately 30,000 km above the Earth. Due to the large distance of these satellites and disturbances in the upper atmosphere, delays in signal transmission may occur, which are unacceptable for communications with high requirements for this communication parameter (including for transmission of binary data and multimedia).
Several companies are currently developing low-orbitsatellites(Low Earth Orbiting (LEO) satellite), whose orbits should be between 700 and 1600 km from the Earth's surface, which should speed up two-way signal transmission. Because of their lower orbit, LEO satellites cover smaller areas, and therefore, in order to completely cover the planet's surface, about thirty LEO satellites are needed. Teledesic, Motorola and Boeing are currently developing a network of such satellites that will make the Internet and other WAN services available anywhere in the world. Users interact with LEO satellites using special antennas and signal decoding equipment. Starting in 2005, LEO satellites can be used in the following areas:
· Broadcast Internet communications; conducting planet-wide videoconferences;
· distance learning;
· Other communications (transmission of voice, video and data).
Communication speeds based on LEO satellites are expected to range from 128 Kbps to 100 Mbps for upstreams (to the satellite) and up to
720 Mbps downstream (from satellite). LEO satellites use ultra-high frequencies approved by the FCC in the United States and similar organizations in various parts of the world. The electromagnetic spectrum of communications using LEO satellites is also approved by the ITU. Operating frequencies are in the range 28.6-29.1 GHz for uplinks and 18.8-19.3 GHz for. downstream channels. When this network goes live (the network architecture is shown in Figure 9.9), a project manager from, for example, Boston will be able to videoconference or exchange important binaries with a researcher living in a mountain hut in Wyoming, and a livestock farm owner from Argentina will be able to apply for agricultural data from the University of North Carolina (Colorado) network. (Complete Practice 9-8 for more information on using LEO satellites to build networks.)

Summary
1 Modern wireless networking technologies use radio waves, infrared radiation, microwave waves, and LEO satellites.
2 Wireless networks are based on experiments with packet radio communications, which have long been carried out by radio operators.
3 Wireless networks are currently used in many areas (for example, when it is difficult to deploy cable networks). In addition, such networks can reduce network setup costs and enable communication with mobile computers.
4 Radio technologies typically use line-of-sight communications that travel from one point to another along the Earth's surface (instead of reflecting the radio signal from the Earth's atmosphere). Such technologies also use spread spectrum communications, in which radio waves are transmitted over several adjacent frequencies.
5 The IEEE 802.11 standard is currently used in various types of radio networks. This standard has three main components: a wireless network adapter (WNIC), an access point, and an antenna. Two standards have been adopted (802.11a and 802.11b), which define the communication rates that correspond to the 802.11 standard. A new standard is being introduced - 802.11g, which is an extension of the 802.11b standard.
6 Common alternatives to 802.11 include Bluetooth, HiperLAN, and HomeFR Shared Wireless Access Protocol.
7 The 802.11R standard uses scattered infrared (IR) radiation to build small, relatively secure networks in fairly confined offices or work areas.
8 Microwave networks exist in two forms: networks based on terrestrial microwave channels and satellite networks. Satellite networks can, of course, be very expensive due to the high costs of launching a satellite into space.
9 Low-Earth Orbit (LEO) satellite networks employ a constellation of satellites in very low orbits above Earth's level, resulting in significantly less signal transmission delays than conventional satellite communications. When LEO satellites are deployed, network connectivity will become available anywhere in the world.
10 Table 9.2 lists the advantages and disadvantages of network communications using radio waves, infrared radiation and microwave waves.
Table 9.2. Advantages and Disadvantages of Wireless Communication Technologies
|
Radio waves |
Infrared radiation |
Microwave waves |
Low-orbit satellites |
|
|
Dignity |
An inexpensive alternative for when it is difficult to implement cable communications. One of the means of implementing mobile telecommunications Usually does not require licensing. |
The signal is difficult to intercept unnoticed. |
An inexpensive alternative for those cases where it is difficult to implement cable communications, especially over long distances. A terrestrial microwave channel over long distances may turn out to be cheaper than leased telecommunication lines |
It can be located above the Earth when creating a global network. They do not create such delays in signal transmission as geosynchronous satellites. |
|
Flaws |
May not meet high-speed network requirements. Susceptible to interference from cellular networks, military, conventional and other radio sources. Susceptible to naturally occurring interference. |
May not be suitable for high-speed communications. Susceptible to interference from extraneous light sources. Not transmitted through walls. The range of devices on offer is smaller than for other types of wireless networks |
May not be suitable for high-speed communications Roads to install and operate. Susceptible to natural interference (rain, snow, fog) and radio interference, and also depends on the state of the atmosphere. |
Available only in 2005 |
Man is a lazy creature. It is much easier for him to press a couple of buttons while sitting on the couch than to go to the kitchen and poke the same buttons on a kettle or toaster. This is probably how the archaic infrared remote control for TVs appeared, and then for other equipment - from stereos to air conditioners.
And "smart" wireless technologies, in fact, appeared in household appliances many years ago. And at first, their purpose was purely utilitarian: Miele luxury washing machines could update their firmware via Wi-Fi and add new washing programs.
Empowerment
Today's household appliances with Wi-Fi use the Internet mainly for remote control (for example, to start a kettle or brew coffee when you arrive) or to download new recipes (in the case of multicooker or coffee machines).
In general, this remote launch gave rise to such a seemingly wild thing as a kettle with a "blue tooth" (which connects to a control module with a Wi-Fi transceiver). Yes, this is the most ordinary kettle, which has the most real Bluetooth. For what? To start from your smartphone, go to the kitchen and pour yourself some tea. And if in the case of a coffee maker this can somehow be justified (I started the coffee grinder, the grains ground, then the coffee was brewed and you come to the kitchen for a ready-made drink), then in the case of an electric kettle it seems at least strange for now: they boil in a minute, therefore, at first glance, this function seems like an unnecessary bells and whistles. On the other hand, if you boil water for baby food and green tea, it may already take some time and then Wi-Fi makes some sense.

However, there is also a tangible plus from new technologies: extended control of household appliances. That is, if it has a lot of functions, managing them from a small and not always well-thought-out control panel is sometimes frankly inconvenient, and then a smartphone / tablet comes to the rescue, on the screen of which you can display as many functions as you like. This opens up enormous opportunities for manufacturers, and they have already begun to use them.
Future
Ideally, wireless technology should serve a person to the fullest. The refrigerator itself orders the necessary products on the basis of a list with payment by card (some already know how to do this), diagnoses itself and calls the wizard in case of a problem (they already know how to do the first part), monitors the condition of the products and warns of the expiration of their validity ... The washing machine, coupled with the dryer itself, will dose the powder and air conditioner, wash everything itself and transfer it to its drying section for drying, and the person will only have to take out and iron the dry laundry.

The kitchen will also house household appliances with Wi-Fi. The coffee maker will brew coffee or a kettle by itself - tea by your arrival (they can already), an appetizing dinner or breakfast will be prepared in the multicooker (they already know how, except that they cannot put anything in themselves), the TV will record an interesting program on Discovery and show it just in the moment of dinner or breakfast (and this has also been possible for a long time).
All this should take place under the complete and strict control of the user. That is, at any time he can go to the control interface and see how the kettle is doing and whether there is enough water there. And if necessary, you can add it (this is something that the devices do not yet know how to do).

The application for the control of household appliances should also be unified. If now each vendor develops its own ecosystem for their devices, then ideally all devices should work on a single OS under the control of properly developed communication protocols. Which will be convenient, open source, and most importantly, safe to use.
It is the issue of security that is important right now. The elements of a smart home system today have a limp in security, and this is an ideal environment for all sorts of fraudsters to penetrate directly into your home. Control interfaces for household appliances today are also very weakly protected, since so far smart home systems are not so implemented into our lives that precedents arise at every step.
What is on the market?
Home appliances with built-in wireless protocols from Redmond are currently the most diverse on the market: this manufacturer was the first to start mass production of devices with wireless technologies for remote control through the proprietary R4S application, but at a fairly high price, justified only for a new item. A huge disadvantage of all Redmond Wi-Fi devices is mentioned above: the need to keep an additional gadget at home that will transmit Bluetooth from the device to the Wi-Fi of the home network (and hereinafter - everywhere). These are the SkyCooker M800S multicooker (9 thousand rubles), kitchen scales SkyScales 741S (2.5 thousand rubles), a drip coffee maker with a built-in SkyCoffee M1505S coffee grinder (9 thousand rubles), floor scales SkyBalance 740S (4.5 thousand rubles). rubles) and the SkyKettle M170S (7 thousand rubles).

There are also little-known manufacturers. For example, the Bite kitchen smart scale from BlueAnatomy for 9 thousand rubles. Or Fitbit Aria Smart Scale bathroom scales with an average price of 12 thousand rubles. Kettles with Wi-Fi are also produced by Polaris: model PWK 1792 CGL with 12 (!) Water boiling programs for 6.5 thousand rubles.

And the Philips Saeco GranBaristo Avanti HD8969 coffee machine for 170 thousand rubles with Bluetooth is aerobatics even with fully automatic cleaning. And by the way, this is exactly the case when all the richness of functionality is concentrated in an application for a tablet (for a smartphone, the screen will be too small).
Ovens with Wi-Fi on the Russian market are now presented by Gorenje, but their price of 80-100 thousand rubles is no longer happy, and the possibility of downloading new recipes does not cost that much money at all.

Split systems with Wi-Fi are no longer a rarity: there are both models from Timberk in a wide price range from 16 to 60 thousand rubles of the TIM and STORM AC series, as well as modules that complement the functionality of conventional air conditioners from Haier or Fujitsu.

But in the multicooker segment, everything is much more interesting: some of them even know how to download new recipes via the Internet. On the Russian market, there are mainly the aforementioned model from Redmond and multicooker from Polaris: it is in the plural, since there are almost a dozen of them in the price range from 9 to 19 thousand rubles.
Can you do without it?
Of course, you can do without Wi-Fi and Bluetooth in household appliances. Our grandmothers and pots were hung over the fires to boil water, but they did not even dream of multicooker. The meaning of this innovation is quite obvious, as well as technological progress in general: to make life easier for a person so that he has more time for more enjoyable activities than cooking, brewing coffee, baking and other everyday household chores. Robot vacuum cleaners, again, can make this life easier.
On the other hand, there are even more problems. Social networks were invented for instant communication without using phones - and people almost stopped communicating with each other live. We have introduced a robot vacuum cleaner into the “smart home” ecosystem - but wet cleaning of the floor is still relevant, and buying another innovation - a steam mop - does not completely solve the problem, but simply offers another way of this solution. The dishwasher seems to eliminate the need to manually wash the dishes and even saves water - but there should be a lot of plates (an average dishwasher is designed for 8-10 sets of dishes for a full load), plus the sink will still have to be used to wash away food debris.

To this we can add the fact that the technology with wireless technology today is already complicating life. For example, the aforementioned Redmond R4S (Ready for Sky!) Series of wireless kitchen appliances, instead of connecting to a regular home router via 802.11, connects to another gadget like a tablet or smartphone via Bluetooth (that is, you need to have a smartphone or tablet lying at home all the time) ), a control program is put on it, and it already communicates with the user and allows you to control the kettle and coffee maker. Why it was necessary to wind up like this is not completely clear. Perhaps because the Wi-Fi module in each device could have made them more expensive. But this is unlikely, since the modules actually cost a penny: but the fact that they could complicate the software or hardware part in principle - it can be. And we are unlikely to be greatly mistaken if we assume that the introduction of Bluetooth / Wi-Fi into devices will still bring a lot of other surprises. In addition, the price for them is still very high: it is clear that it includes not only the price of a penny Wi-Fi / Bluetooth module, but also the work of both engineers and programmers.
The answer to the question "to buy or not" today can be as follows: more likely no than yes. Yes, now there is still a certain "wow-effect" from the fact that you can make yourself coffee while lying in bed. Of course, it is convenient to start the multicooker from work in order to have dinner immediately upon returning. But various "childhood diseases" like an excessive number of devices in Redmond SkyCooker devices have just begun to manifest themselves, and since the segment has just begun to develop, they will continue to grow.
Electronics is at the heart of virtually all communication. It all began with the invention of the telegraph in 1845, followed by the telephone in 1876. Communication has been constantly improving, and the recent progress in electronics has laid a new stage in the development of communications. Today wireless communication has reached a new level and has confidently occupied the dominant part of the communication market. And new growth is expected in the wireless communications sector thanks to the evolving cellular infrastructure, as well as modern technologies such as. In this article, we will look at the most promising technologies for the near future.
4G status
4G in English means Long Term Evolution (LTE). LTE is the OFDM technology that is the dominant structure of the cellular communication system today. 2G and 3G systems still exist, although the introduction of 4G began in 2011-2012 Today, LTE is mainly marketed by major carriers in the US, Asia and Europe and has yet to be completed. LTE has gained immense popularity among smartphone owners as high data rates have opened up opportunities such as video streaming for efficient movie viewing. less, it’s not so perfect.
Although LTE promised download speeds of up to 100 Mbps, this has not been achieved in practice. Speeds up to 40 or 50 Mbps can be achieved, but only under special conditions. With a minimal number of connections and minimal traffic, these speeds can rarely be achieved. The most probable data rates are in the 10-15 Mbit / s ranges. During peak hours, the speed drops to several Mbps. Of course, this does not make the implementation of 4G a failure, it means that its potential is not fully realized yet.
One of the reasons why 4G does not provide the declared speed is too many consumers. If it is used too much, the data transfer rate will be significantly reduced.
However, there is hope that this can be corrected. Most carriers offering 4G services have not yet implemented LTE-Advanced technology, an improvement that promises to increase data transfer speeds. LTE-Advanced uses carrier aggregation (CA) to increase speed. “Carrier aggregation” refers to the aggregation of LTE standard bandwidth up to 20 MHz into 40 MHz, 80 MHz or 100 MHz portions to increase throughput. LTE-Advanced also has an 8 x 8 MIMO configuration. Support for this feature opens up the potential for increased data rates up to 1 Gbps.
LTE-CA is also known as LTE-Advanced Pro or 4.5G LTE. These technology combinations are defined by the 3GPP Standards Development Group in Release 13. It includes operator aggregation as well as Licensed Assisted Access (LAA), a method that uses LTE over the unlicensed 5 GHz Wi-Fi spectrum. It is also rolling out LTE-Wi-Fi link aggregation (LWA) and dual connectivity, allowing the smartphone to talk to both a small hotspot and a Wi-Fi hotspot at the same time. There are too many details in this implementation that we will not cover, but the overall goal is to extend the lifespan of LTE by reducing latency and increasing the data transfer rate to 1 Gbps.
But that's not all. LTE will be able to deliver better performance as carriers begin to simplify their strategy with smaller cells, providing higher data rates for more subscribers. Small cells are simply miniature cellular base stations that can be installed anywhere to fill the macrocell coverage gaps, adding performance where needed.
Another way to improve productivity is by using Wi-Fi. This method provides fast downloads to the nearest Wi-Fi hotspot when available. Only a few operators have made this available, but most are considering an LTE enhancement called LTE-U (U for unlicensed). This is a similar method to LAA, which uses the unlicensed 5 GHz band for fast downloads when the network cannot handle the load. This creates a spectrum conflict with the latter, which uses the 5 GHz band. Certain trade-offs have been developed to accomplish this.
As we can see, the potential of 4G is still not fully revealed. In the coming years, all or most of these improvements will be implemented. It's worth noting that smartphone manufacturers will also make hardware or software changes to improve LTE performance. These improvements are likely to happen when the massive adoption of the 5G standard begins.
Discovery of 5G
There is no 5G as such yet. So, it is too early to make a loud statement about “an absolutely new standard capable of changing the approach to wireless information transmission”. Although, some ISPs are already starting to debate who will be the first to implement the 5G standard. But it's worth remembering the controversy over 4G in recent years. After all, there is no real 4G (LTE-A) yet. However, work on 5G is in full swing.
The Third Generation Partnership Project (3GPP) is working on the 5G standard, which is expected to be rolled out in the coming years. The International Telecommunication Union (ITU), which will “bless” and administer the standard, says 5G should finally be available by 2020. However, some early versions of the 5G standard will still appear in the competition between providers. Some 5G requirements will appear as early as 2017-2018 in one form or another. Full implementation of 5G will not be an easy task. Such a system would be one of the most complex, if not the most complex, wireless networks. Its full deployment is expected by 2022.
The rationale behind 5G adoption is to overcome the limitations of 4G and add capabilities for new applications. 4G limits are mostly subscriber bandwidth and limited data rates. Cellular networks have already moved from voice technology to data centers, but further performance improvements are needed in the future.
Moreover, a boom in new applications is expected. These include HD 4K video, virtual reality, the Internet of Things (IoT), and machine-to-machine (M2M) architecture. Many still predict 20 to 50 billion devices online, many of which will connect to the Internet via cellular. While most IoT and M2M devices operate at low data rates, high speed internet is required to work with streaming data (video). Other potential applications that will use the 5G standard could be smart cities and communications for the safety of road transport.
5G is likely to be more revolutionary than evolutionary. This will involve the creation of a new network architecture that will overlap with the 4G network. The new network will use distributed small cells with fiber or millimeter return channel, and will also be economical, non-volatile and easily scalable. Plus, there will be more software than hardware in 5G networks. Software networking (SDN), network function virtualization (NFV), self-organizing networking (SON) techniques will also be used.
There are also a few more key features:
- Using millimeter waves. The first versions of 5G can use the 3.5 GHz and 5 GHz bands. Frequency options from 14 GHz to 79 GHz are also being considered. The final version has not yet been selected, but the FCC says the choice will be made soon. Testing is conducted at 24, 28, 37 and 73 GHz.
- New modulation schemes are considered. Most of them are some variant of OFDM. Two or more schemas can be defined in the standard for different applications.
- Multiple Input Multiple Output (MIMO) will be included in some form for increased range, data rate, and link reliability.
- The antennas will have phased arrays with adaptive beamforming and steering.
- Lower latency is the main goal. Less than 5ms is specified, but less than 1ms is the target.
- Data rates from 1 Gbps to 10 Gbps are expected in bandwidths of 500 MHz or 1 GHz.
- Microcircuits will be made from gallium arsenide, silicon-germanium and some CMOS.
One of the biggest challenges in adopting 5G is expected to be the integration of this standard into mobile phones. Modern smartphones are already full of different transmitters and receivers, and with 5G they will become even more complicated. Is this kind of integration necessary?
Wi-Fi development path
Along with cellular communication, there is one of the most popular wireless networks - Wi-Fi. Like, Wi-Fi is one of our favorite "utilities". We look forward to being connected to a Wi-Fi network just about anywhere, and most of the time we get access. Like most popular wireless technologies, it is constantly under development. The latest released version is called 802.11ac and offers speeds up to 1.3 Gbps in the unlicensed 5 GHz band. There is also a search for applications for the 802.11ad standard with an ultrahigh frequency of 60 GHz (57-64 GHz). It's a proven and cost-effective technology, but who wants 3 to 7 Gbps speeds up to 10 meters away?
At the moment, there are several projects for the development of the 802.11 standard. Here are a few of the main ones:
- 11af is a Wi-Fi version in the white bands of the television range (54 to 695 MHz). Data is transmitted in local 6- (or 8) MHz bandwidths, which are not occupied. Data transfer rates up to 26 Mbps are possible. Sometimes referred to as White-Fi, the 11af's main appeal is that it has many kilometers of range at low frequencies and no line of sight (NLOS) (open areas only). This version of Wi-Fi is not yet in use, but has the potential for IoT applications.
- 11ah - designated HaLow, is another Wi-Fi variant that uses the unlicensed ISM 902-928 MHz band. It is a low-power, low-speed (hundreds of kbps) service with a range of up to a kilometer. The goal is application in the IoT.
- 11ax - 11ax is an upgrade to 11ac. It can be used in the 2.4 and 5 GHz bands, but it will most likely operate in the 5 GHz band solely to use the 80 or 160 MHz bandwidth. Along with 4 x 4 MIMO and OFDA / OFDMA, peak data rates of up to 10 Gbps are expected. There will be no final ratification until 2019, although preliminary versions are likely to be complete.
- 11ay is an extension of the 11ad standard. It will use a 60 GHz frequency band and the target is at least 20 Gbps data rates. Another goal is to extend the range up to 100 meters in order to have more applications such as return traffic for other services. This standard is not expected to be released in 2017.
Wireless networks for IoT and M2M
Wireless is certainly the future of the Internet of Things (IoT) and Machine-to-Machine (M2M) communications. Although wired solutions are also not ruled out, the pursuit of wireless is still preferable.
Typical for IoT devices is short range, low power consumption, low data rates, battery power, or battery power with a sensor, as shown in the figure below:

An alternative would be some kind of remote actuator, as shown in the figure below:

Or a combination of the two is possible. Both usually connect to the internet via a wireless gateway, but they can also connect via a smartphone. The connection to the gateway is also wireless. The question is, which wireless standard will be used?
Wi-Fi is becoming the obvious choice as it is difficult to imagine a place where it does not exist. But for some applications it will be overkill, and for some too power-hungry. Bluetooth is another good option, especially its low energy (BLE) version. New additions to the Bluetooth network and gateway make it even more attractive. ZigBee is another ready and pending alternative, and let's not forget about Z-Wave. There are also several options for 802.15.4 such as 6LoWPAN.
Add to these the latest options that are part of Low Power Wide Area Networks (LPWAN). These new wireless options offer longer range network connections that would normally not be possible with the traditional technologies mentioned above. Most of them operate in the unlicensed spectrum below 1 GHz. Some of the newest competitors for IoT applications are:
- LoRa is an invention of Semtech and is backed by Link Labs. This technology uses chirp at low data rates to achieve a range of up to 2-15 km.
- Sigfox is a French development that uses an ultra narrowband modulation scheme at low data rates to send short messages.
- Weightless - Uses television white spaces with cognitive radio techniques for longer ranges and data rates up to 16 Mbps.
- Nwave - This is similar to Sigfox, but we have not been able to collect enough information at this point.
- Ingenu - Unlike others, this one uses the 2.4 GHz band and a unique random phase multiple access scheme.
- Halow is 802.11ah Wi-Fi, described above.
- White-Fi is 802.11af, described above.
Cellular is definitely an IoT alternative as it has been the backbone of machine-to-machine communications (M2M) for over 10 years. Machine-to-machine communications use mainly 2G and 3G wireless modules to monitor remote machines. While 2G (GSM) will eventually be phased out, 3G will still be alive.
A new standard is now available: LTE. More specifically, it is called LTE-M and uses a reduced version of LTE in a 1.4 MHz bandwidth. Another version of NB-LTE-M uses 200 kHz bandwidth to operate at a lower speed. All of these options will be able to leverage existing LTE networks with updated software. Modules and chips for LTE-M are already available, just like on Sequans Communications devices.
One of the biggest problems with the Internet of Things is the lack of a single standard. And in the near future, most likely, he will not appear. Perhaps in the future, there will be several standards, but how soon?
Modern wireless networks can be broken down into three categories:
1. Interacting systems.
Interactive systems mean, first of all, the interconnection of computer components using short-range radio waves. Any computer consists of several parts: monitor, keyboard, mouse, printer ... Each of these external devices, as you know, are connected to the system unit using cables. Several companies, one after another, have come up with the idea of creating a Bluetooth wireless system, designed to remove cables and connectors from computer components. Using Bluetooth, you can connect to your computer almost any digital device located near the system unit. As a rule, interaction within the system is governed by the principle of "master-subordinate". The system unit acts as a master, and all others act as slaves. It is the system unit that assigns device addresses, determines the moments at which they can "broadcast", limits the transmission time, sets the operating frequency ranges, etc.
The characteristic features of Bluetooth are multi-point (i.e., there may be not two devices in the network, but several), no need for line of sight (since frequencies of the order of 2.44 GHz are used), range from 10 m.
2. Wireless LAN (LAN).
In wireless local area networks, each computer is equipped with a radio modem and antenna, with their help it can exchange data with other computers. Sometimes there is a common antenna located on the ceiling, and data transmission occurs through it, but if the network workstations are close enough, then they usually use a peer-to-peer configuration. Wireless networks are increasingly used in business and home use, where there is no point in laying Ethernet, as well as in old buildings rented for offices, in cafeterias, in office centers, conference rooms and other places. The most popular wireless networking standard is IEEE 802.11 or WiFi.
3. Wireless wide area networks (WAN).
An example would be a cellular system, which is actually a low-performance digital wireless network. There are already three generations of cellular communication. The first cellular networks were analog and were intended only for voice transmission. The second generation was already digital, but nothing but speech could still be transmitted. Finally, the modern, third generation is digital, with the possibility of transmitting both voice and other data. In a sense, cellular networks are the same as wireless LANs, the only difference is in the coverage area and the lower transmission speed. While conventional wireless networks can operate at speeds of up to 50 Mbps at a distance of tens of meters, cellular systems transmit data at 1 Mbps, but the distance from a base station to a computer or phone is measured in kilometers, not meters.
In a mobile telephone system, the geographic coverage area is divided into cells, which are in the order of 10 km. In the center of each cell is a base station, with which all telephones in its coverage area communicate. The base stations themselves are connected to each other by standard networking means. At each moment of time, the mobile phone is logically within the coverage of one cell and is controlled by the base station of this cell. When a phone physically leaves the cell, its base station notices the weakening of the signal and polls all surrounding stations for how well they can hear that phone's signal. The base station then transfers control of this phone to the cell that receives the strongest signal from it, thus determining the cell to which the mobile phone has moved. After that, the phone is informed about the transition to the maintenance of the new BS, and if a conversation is ongoing at this moment, the phone will be prompted to switch to a new channel (since the same frequency channels are not used in neighboring cells). This process is called a transfer and takes about 300ms. The assignment of the channel is carried out by the mobile phone switch MTSO, which is the central nerve of the system. Base stations are just radio repeaters. The transfer can be done in two ways. In a soft handover, the phone is taken over by the new base station even before leaving the old one. In this case, even a short-term loss of communication does not occur. The disadvantage of this method is that at the time of the transition from one BS to another, the phone must work simultaneously on two frequencies. Phones of the first and second generation do not know how to do this. In a hard transfer, the old base station cuts off the connection with the phone before the new one takes it under its wing. If the latter cannot establish communication with the telephone for some time (for example, due to the lack of free frequencies, the conversation may end.
Among the data transmission technologies used in cellular networks, GPRS should be highlighted. It works as an add-on to the existing voice system. Some time slots on some frequencies are reserved for packet traffic and IP packets can be transmitted in parallel with voice. Another technology is called EDGE and is a conventional GSM (Global System for Mobile Communications) with an increased number of bits per baud.