In short: If you use a pattern to access the phone, then 99% of this is enough for no one without your knowledge to be able to access the information on the phone. If the data on the phone is very sensitive, then the built-in full encryption of the phone should be used.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and use special means to protect the phone from unauthorized access in the event of its theft or loss.
- Who should protect your phone data from.
- Built-in data protection in Android.
- Full Phone Memory Encryption
- Outcomes
What information is stored on the phone and why should it be protected?
A smartphone or tablet often acts as a mobile secretary, freeing the owner's head from storing a large amount of important information. The phone book contains the numbers of friends, employees, family members. In a notebook, they often write credit card numbers, access codes to them, passwords to social networks, e-mail and payment systems.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen on purpose to infiltrate personal life or share the profit with the owner.
Sometimes they are not stolen at all, and they are used for a short time, imperceptibly, but a few minutes is quite enough for an experienced attacker user to find out all the details.
Loss of confidential information can turn into financial ruin, personal ruin, family breakdown.
I wish I didn't have it! - the former owner will say. - How good that you had it! - the attacker will say.
And so you need to protect on your phone:
- Accounts. This includes, for example, access to your gmail inbox. If you have set up sync with facebook, dropbox, twitter. Logins and passwords for these systems are stored in clear text in the phone profile folder /data/system/accounts.db.
- History of SMS-correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that the Web Browser (built-in or third-party) remembers all passwords and logins for you. All this is stored in open form in the program profile folder in the phone memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to the account open, even if you did not specify to remember the password.
If you use synchronization of a mobile browser (Chrome, FireFox, Maxthon, etc.) with the desktop version of the browser to transfer bookmarks and passwords between devices, then we can assume that you can access all passwords from other sites from your phone. - Memory card. If you store confidential files on the memory card or download documents from the Internet. Typically, the memory card stores photos and videos.
- Photo album.
Who should protect phone data from:
- From a random person who finds your lost phonel because from “accidental” phone theft.
It is unlikely that the data in the phone will be of value to the new owner in this case. Therefore, even simple protection with a graphic key will ensure the safety of data. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers / children / wives), who can access the phone without your knowledge, taking advantage of your absence. Simple protection will keep your data safe.
- Granting access under duress
It happens that you are voluntarily forced to provide a phone and open access to the system (information). For example, when your wife, a government official, or an employee of the service center asks you to look at your phone number, where did you take the phone for repair. In this case, any protection is useless. Although it is possible, with the help of additional programs, to hide the fact of the presence of some information: hide part of SMS correspondence, part of contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protections on Android devices .
1. Lock screen with Pattern.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, then no one can use it. But if you deliberately fell into the wrong hands for your phone, then it is unlikely to save. Hacking can even happen at the hardware level.
The screen can be locked with a password, PIN and Pattern. You can choose a blocking method by running the settings and selecting the Security -> Screen lock section.
Pattern - c The most convenient and at the same time reliable way to protect your phone.

None- lack of protection,
Slide- to unlock, you need to slide your finger across the screen in a certain direction.
Pattern- this is the Graphic Key, it looks something like this:
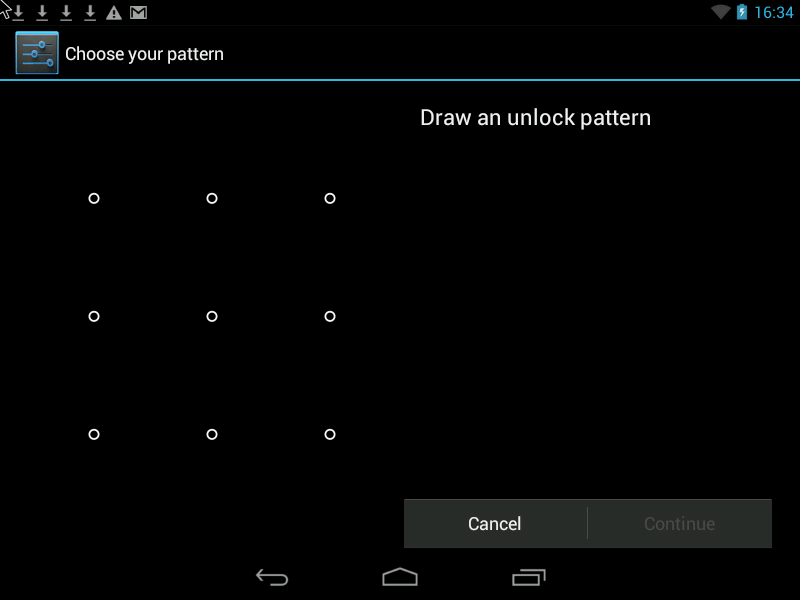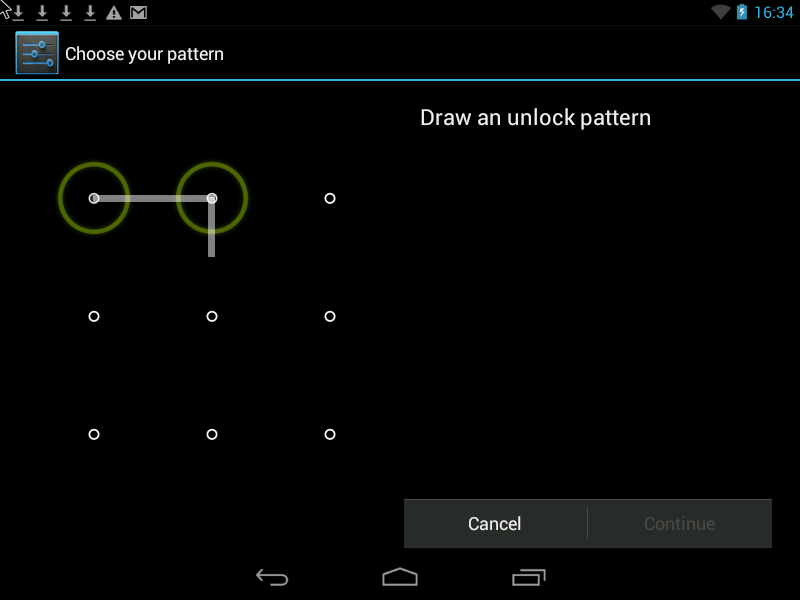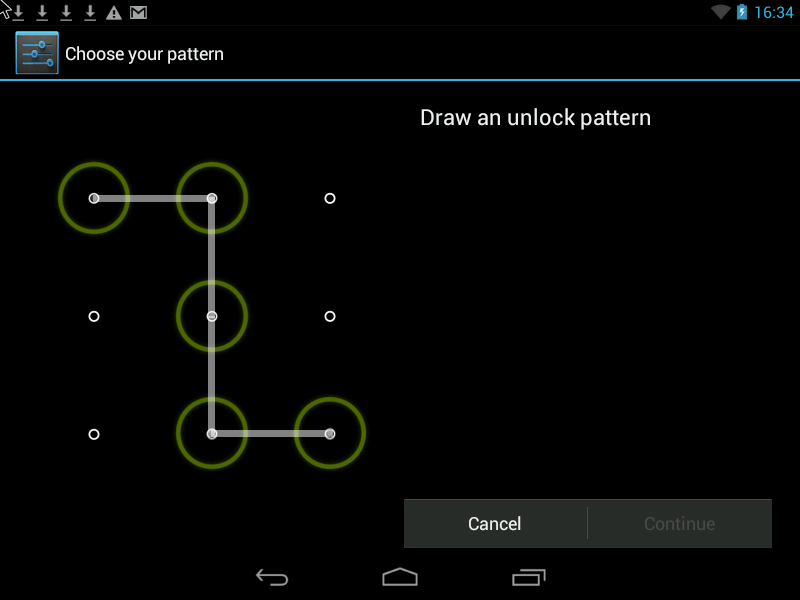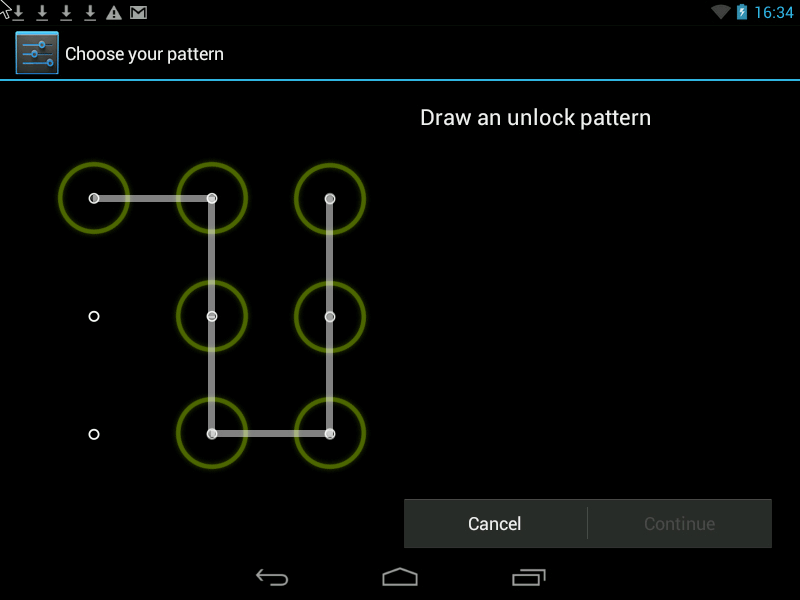
There are two ways to improve security.
1. Increase the input field of the Pattern key. It can vary from 3x3 pixels on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of points and the "path" of the pattern on the smartphone screen so that it is impossible to peep the key.
3. Set automatic screen lock after 1 minute of inactivity of the phone.
Attention!!! What happens if you forget your pattern:
- The number of incorrect attempts to draw a Pattern is limited to 5 times (in different phone models, the number of attempts can be up to 10 times).
- After you have tried all your attempts, but still have not drawn the Pattern Key correctly, the phone is locked for 30 seconds. After that, you will most likely have a couple of tries again depending on your phone model and Android version.
- Next, the phone asks for the login and password of your Gmail account, which is registered in the phone's Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It so happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN Is a password consisting of several numbers.
Finally, Password- the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Phone memory encryption.
This feature is included in the Android package version 4.0 * and higher. for tablets. But this feature may not be available on many budget phones.
It allows you to encrypt the internal memory of the phone so that it can be accessed only by a password or PIN-code. Encryption helps protect information on your phone in the event c
targeted theft. Attackers will not be able to gain access to your data from the phone in any way.
A prerequisite for using encryption is to set up a screen lock with a password.
This method is used to save the user's data located in the phone's memory, for example, the phone book, browser settings, passwords used on the Internet, photos and videos that the user received with the camera and did not transfer to the SD card.



- SD card encryption is enabled as a separate option.
- Encrypting memory may take up to an hour depending on the amount of memory on your device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery in this case is not provided. You can make your phone or tablet a full RESET, i.e. reinstall Android, but the user data from the phone or tablet memory will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get the phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply be absent on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have encryption function. On some phones, this function is located in the "Memory" section.
Flaws:
- You will have to constantly enter a rather complex password (6-10 characters), even if you just want to call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when the phone screen is turned on. On some phone models, the minimum password length can be 3 characters or more.
- On some phone models, it is not possible to turn off encryption if you want to opt out of entering your password permanently. Encryption is disabled only by restoring the phone to factory settings and deleting all data.
External SD card encryption
The feature is included in the standard Android 4.1.1 package for tablets. Absent in many budget builds.
The function provides reliable protection of data on an external SD card. Personal photographs, text files with commercial and personal information may be stored here.
Allows you to encrypt files on the SD-card without changing their names, file structure, while preserving the preview of graphic files (icons). The function requires a lock password to be set on a display with a length of at least 6 characters.




It is possible to cancel encryption. When the password is changed, it is automatically re-encrypted.
If the user has lost the memory card, the encrypted files cannot be read through the card reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet to a computer via a USB cable, the encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write any other unencrypted files to the card through the card-reader, they will also be encrypted after the card is inserted into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- The data is encrypted at the file level (the names of the files are visible, but the contents of the file are encrypted).
Disadvantage of the program:O Absence in most Android assemblies.
It should be emphasized that the best data safety is a complete copy of it on your Computer in A smartphone is a rather fragile device of small size, which means there is always a possibility of its breakage or loss.
Improving the usability of a secure smartphone
Fully encrypting your phone provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
In the Android system since version 4.2 *, it is possible to bring some applications \ widgets to the lock screen, and thus you can perform simple actions without permanently unlocking the phone (without entering a 6-digit password).
Outcomes:
- The built-in and free features to protect your phone are very reliable. They are able to protect the user's contacts, his correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone's memory and on a removable SD card from prying eyes.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use a too complex PIN-code or password on the lock screen (Pattern is not suitable), the irreversibility of encryption of the internal memory of the phone, i.e. the only way to turn off encryption is to reset your phone completely.
- Important! Make sure that in case you forgot your password or Pattern, you can restore access to the phone, or you can easily restore the phone settings and information in case you have to do a hard reset (reset the phone to factory settings with the loss of all data).
- It is only necessary to store a backup copy of confidential data on your PC, on a DVD or in the cloud.
Data encryption tools have been around for a long time, but all of them are either very expensive or require extensive knowledge of encryption from users. A group of free and open source advocates known as Open Whisper Systems hopes to correct this injustice with a new Signal app.
Signal is said to be the first iOS app designed to provide a simple and efficient way to encrypt calls for free.
It should be noted that Open Whisper Systems has accumulated considerable experience in this area. Open Whisper Systems is known to many users as the developer of RedPhone and TextSecure Android applications for encrypting calls and messages, respectively. And now they have decided to prove themselves in the iOS ecosystem.
Signal uses the well-proven ZRTP cryptographic protocol and 128-bit AES to encrypt telephone conversations. In theory, this protection is more than enough to resist all attacks known today, orchestrated by anyone, from crack kiddies to the NSA.
Even though Signal uses end-to-end encryption, the conversation itself looks familiar. The application uses the user's phone number to work, no additional identifiers are required. Essentially, Signal is a VoIP system. The application allows organizing an encrypted voice communication channel between end users over IP networks, therefore it does not use cellular networks and minutes provided within the tariff plan, but relies on a cellular connection or Wi-Fi networks.
The only indication that a telephone conversation between two Signal users is encrypted and immune to man-in-the-middle attacks is a pair of randomly generated words exchanged between the parties. The user must say these words aloud to his interlocutor at the other end of the line for authentication.
The technology behind the Signal IP telephony service is not new. Renowned computer security expert and co-founder of Open Whisper Systems Moxie Marlinspike challenged the lack of encryption on smartphones 4 years ago with the aforementioned Redphone VoIP system for Android.
RedPhone, like Signal, uses the ZRTP protocol, one of the developers of which is Philip Zimmerman, the creator of the cult encryption software PGP. Mr. Zimmerman also developed his own ZRTP implementation for his startup Silent Circle (hello), which sells call and message encryption software for iPhone and Android. However, unlike Open Whisper Systems, Silent Circles' customers are mainly corporate users who monthly transfer $ 20 to companies for using the proprietary Silent Circles software. Another benefit of the Open Whisper Systems solution is that Signal users can make secure calls to Redphone users. All friends who are using Redphone are displayed in the contact list of the Signal user.
It is worth noting that Signal benefits not only from the existing Redphone user database, but also from the physical infrastructure of Redphone - a network of servers around the world for routing local calls to reduce latency. To reassure users, the development team stated that Signal does not leave metadata, no call logs are stored on the company's servers. All encryption takes place locally, on the smartphone itself.
Signal offers the same services as Silent Circle but completely free of charge, making it the first free iOS call encryption app of its kind. It's also worth mentioning once again that Signal is open source. The Signal iOS source code is published on Github. The application is still under development and the company invites everyone interested to test it for reliability. It is also reported that this summer, support for message encryption may appear in the application.
Rather than going commercial, Open Whisper Systems chose to remain independent and funded by donations and government grants. It is worth noting that the well-known anonymous Tor network and the secure messenger Cryptocat are also funded within the framework of special US government programs.
Like every new encryption-enabled software, Signal has yet to be tested for lice, so don't rely entirely on the application until it has been thoroughly reviewed by a variety of independent security experts. Moxie Marlinspike acknowledges that there are always invisible threats, such as vulnerabilities in iPhone software, that would give attackers the opportunity to eavesdrop on conversations.
The Signal app can be downloaded free of charge from the app store
--------
Encrypting cell phone conversations: how to protect yourself from wiretapping
As practice shows, it is far from only the computer of the "suspect" that can be hacked - the crypto protection of GSM cellular networks also does not help to 100% protect your communications from interception and eavesdropping (although it is much more difficult to do this). How to protect confidential information from prying eyes and ears?
You can view sent text messages and mail, record conversations in several completely different ways, let's look at the main ones. The first and most common of them is a "bug" in the subscriber's premises. The required devices can be found on the Internet at the corresponding request in Yandex. Surprisingly, anyone can buy a bug. A device with a built-in SIM-card will allow listening to the “victim's” replicas during telephone conversations in the room where it is installed. As you yourself understand, it is impossible to protect yourself with any software from such a "hacking" - all that remains is to turn on paranoia and search the premises or even go out into the street before an important call.
A very popular method of espionage is the so-called "Trojan Horse" - a smartphone presented to the "victim" with a "back door" wide open. Modern smart phones offer a variety of means for recording all conversations and text messages. At the same time, the spyware is easily disguised in the system - an inexperienced user will hardly be able to immediately recognize that he is being tapped. Apple iPhones have become a real find for such "operations" - the device allows you to record everything that happens and unload the archive remotely through built-in services. A godsend for an industrial spy. Alternatively, hackers can get hold of your favorite mobile phone and secretly install spyware on it. Hence the advice: do not trust such friendly "gifts" and do not leave your phone in a conspicuous place if your car is a Mercedes-Benz of the latest model, and a pretty secretary is sitting in the waiting room.
Then there are much more sophisticated wiretapping methods, which are only achievable if your confidential conversations cost a lot of money. We are talking about specialized mobile stations with antennas and computers, such as the GSM Passive Cellular Interceptor. They scan the frequency bands on which cell phones operate, intercept the conversation and decode it. Such devices do not attract the attention of cellular operators or the subscriber being tapped. Of the minuses - a very high price and the need to be at a distance of no more than three meters from the subscriber being listened to. Otherwise, the device will not be able to correctly intercept the desired frequency.
Finally, employees of state bodies can listen to your conversations with the permission of the prosecutor / court - specifically for such operations, there is SORM (System of technical means for ensuring the functions of operational-search measures). Here everything is carried out according to the law - a court or a high-ranking official issues permission to restrict the secrecy of communication of a subscriber suspected of illegal acts. There is only one way to protect yourself from this kind of interference with your privacy - not to break the law. In another case, the authorities will find how to influence your actions, you can be sure.
Alternatively, attackers can find some frivolous employee of the operator's company and pay him to listen to the already decrypted conversations through the switches. Telephone call encryption programs can protect against such mobile interceptors. To use encryption software, you need a modern smartphone, and the more powerful it is, the better - real-time encryption using long keys takes up a lot of system resources, so the device will have to work under increased load. Understandably, ordinary cell phones with Java-based programs will not cope with the intensive flow of computations.
CELLCRYPT
The list of software tools is opened by one of the most popular ransomware called Cellcrypt Mobile, originally from Britain. The program with a nice interface must be installed on both phones on which you will talk. In this case, the exchange of encrypted data takes place via the CSD channel, that is, you call, as it were, from a modem to a modem. In addition, the software successfully works through a packet data connection (GPRS, EDGE, UMTS, HSDPA, EV-DO), as well as via Wi-Fi - however, in these cases you will have to pay not for time, but for traffic.
To encrypt the signal, Cellcrypt uses the AES algorithm with a 256-bit key and appropriate integrity checks. The developer promises very reliable, clear voice communication without interference and loss of fragments - even the military can use Cellcrypt Mobile. The program has passed tests for compatibility with cellular networks, received FIPS 140-2 security certification in the United States, and is available for owners of Nokia Symbian-based smartphones and advanced mobile phones of the Canadian company RIM Blackberry.
As a nice addition, the latest version of Cellcrypt Mobile has learned how to make secure calls via satellites using all the same Nokia and BlackBerry smartphones. All that is needed for such a call is a broadband terminal with satellite connection. The subscriber will be able to receive a call from the satellite to his cell phone with the preinstalled Cellcrypt application. The issue price is £ 500.
SECUREGSM
The rather expensive SecureGSM software is designed to be paired with cell phones running the Microsoft Windows Mobile operating system - the developer portfolio includes versions for devices with touch and conventional displays.
The program allows you to make confidential telephone conversations and send encrypted text messages over the CSD data channel in cellular networks, providing effective two-way protection against wiretapping and message interception. You can view the list of supported smartphones on the developers website.
SecureGSM uses a reliable 256-bit cipher based on three algorithms at once - AES, Two sh, Serpent. None of these algorithms are currently decipherable. Private and public keys are generated only for one message transmission session and are destroyed upon termination of communication. On the part of the caller, verification procedures are carried out to ensure the safety and invariability of the transmitted information. In the crypto community, such protection measures are called "paranoid", while the developer promises the ideal voice quality.
SecureGSM will cost $ 600-850, those who wish can buy a device with already installed software for $ 1600-1800 (HTC Touch II, HTC S730 and others).
CRYPTOGIC
Cryptogic software is a class of low-cost encryption tools. A utility for Nokia smartphones based on the Symbian operating system (3rd, 5th Edition) costs only € 100.
The application tightly integrates with the smartphone operating system, allows you to make well-encrypted calls between two mobile phones (yes, you will have to install Cryptogic on both). AES algorithm with a 256-bit key is used to encrypt voice, and DES is used to transfer secret data. It will take years to crack the chosen encryption methods, unless, of course, the multimillion-dollar IBM Roadrunner supercomputer is at hand. In other words, it is almost impossible to crack the algorithm. The ability to work using the HSCSD protocol provides the best voice quality for encrypted calls. True, it is usually not supported on our networks. Of the minuses - the program does not support encryption of text messages, but at such and such a price ...
5PRO SOFTWARE SECURE VOICE
You can choose a program for encryption at your own will - numerous products are available within a couple of mouse clicks. But what do the cell phone makers themselves offer? Nokia recommends encrypting conversations using the Secure Voice application from the German-Ukrainian developers 5Pro Software.
The program for smartphones based on Symbian 3rd Edition is distinguished by a completely paranoid encryption method using two algorithms at once with incredibly long keys - 2048- or 1024-bit RSA and 256-bit AES (or ARC4). It will certainly not be possible to crack such a well-encrypted stream. Before starting the connection, two cell phones with preinstalled Secure Voice exchange randomly generated keys; in the process of communication, the keys are changed more than once.
The easy-to-understand interface of the application allows you to dial numbers manually or make a secure call to a contact from the address book. The key audience of Secure Voice is government organizations, bankers, businessmen. The license price depends on the number of ordered copies, the developers report the price themselves.
Note that a similar version of Secure Voice is available for owners of BlackBerry cell phones.
PHONECRYPT
Meet the most powerful encryption encryption program for Apple iPhone phones (the developers have provided support for iPhone 3G and 3GS) - PhoneCrypt. In addition, the application works with smartphones based on Microsoft Windows Mobile 6.1.
When dialing a subscriber's number, PhoneCrypt automatically performs a 4096-bit exchange of a secret key between two phones, immediately after that a 256-bit key is generated. In the course of work, powerful algorithms AES and Diffie-Hellmann are used. The preparation of actions takes only 5 seconds. After the end of the conversation, the used key is deleted. At the same time, special check functions allow you to determine if a spy is trying to intervene between two subscribers - another degree of protection, this is always nice. All information, as in other applications, is transmitted over the CSD data channel.
The software successfully copes with the encryption of text messages and even memory areas - all e-mails, documents will be stored in encrypted form (the latter function is available for devices based on Windows Mobile). PhoneCrypt does not require high power to function - a processor of 150 MHz or more is enough. PhoneCrypt software costs $ 350.
GOLD LOCK
Israeli Gold LockAES application with 256-bit key, Diffie-Hellman and RSA. All keys needed to connect to another device are generated on the fly and deleted after the session ends.
The developers release two versions of the program at once - Gold Lock GSM and Gold Lock 3G. The first one is compatible with Nokia smartphones based on Symbian 3rd Edition and works through the data channel of GSM networks (CSD). In case of using Gold Lock GSM, the cost of calls will not differ from the cost of regular calls. The second version is a much more advanced modification with support for a wide range of Nokia smartphones (including touchscreen models), BlackBerry (OIS 4.6+), iPhones and even desktops and laptops. The program communicates with subscribers through any available communication channels - Wi-Fi, 3G, GPRS, EDGE, UMTS, CDMA, you will have to pay for Internet traffic. The developer claims traffic consumption at 250 Kb per minute. The program also successfully encrypts text messages and even transmitted files.
The cost of Gold Lock is specified for each case on the developer's website.
COMPUMATICA GSM
Another tool for encrypting mobile conversations, text messages and emails is offered by the German developer Compumatica. Compumatica GSM is a very young but very ambitious project. To begin with, the developers promise flexible compatibility with any mobile operating system, but they did not disclose details. Judging by the picture on the company's website, the tool is available at least for Windows Mobile and ordinary cell phones, like the well-worn Motorola RAZR - this gives reason to believe that Compumatica GSM is based on Java technologies. But will not new phones have enough power for adequate operation of encryption mechanisms?
Compumatica GSM uses the AES algorithm with a 256-bit key to encrypt conversations; when creating an identification key, the 4096-bit Diffie-Hellman protocol is used. They say that encrypted calls can be made without transferring the shared key to the second device. The reliability of the connection in this case, presumably, will be lower. Of course, the developers guarantee the safety even without the simultaneous use of three different algorithms. The program monitors the absence of third-party listeners in the communication channel - in which case, Compumatica GSM will not allow you to tell any very important data to an outsider.
SMS ENCRYPTION
For those who do not need to encrypt conversations, but would like to protect precious SMS from prying eyes, there are simple clients for encrypting messages. Take SafeTxT, for example, is a free application for Symbian smartphones. The functionality of the program allows you to send and receive encrypted SMS, encrypt a book with contacts and personal records. All data will be available only after entering the password.
For encryption, advanced algorithms AES and RC4 are used (the developers call them "army-level algorithms"). As a nice addition, the program allows you to erase all data stored on your smartphone remotely.
Another lightweight Java program for encrypting text messages is CryptoSMS. Unlike SafeTxT, it provides archiving of sent SMS so that the user does not have to pay for a double-sized message (encryption algorithms greatly inflate the file size).
Finally, the completely free open source SMS Salama program offers to send messages under a password known to only two subscribers. In addition, the program encrypts your contact list.
EPILOGUE
As you can already understand, professionals from the world of encryption algorithms have come up with and developed many tools for the reliable transmission of voice, text messages, emails. At the same time, many programs do not require paying for Internet traffic, transferring through the data channel of GSM networks.
Unfortunately, there is one problem - the legislation of the Russian Federation prohibits the use of encryption algorithms when exchanging voice data. According to the Law "On Communications", all cellular operators in the territory of the Russian Federation must provide access to negotiations for any subscriber in the presence of appropriate decisions of the prosecutor or judge. Therefore, your innocent conversations about girls and complaints about your mother-in-law in encrypted form will instantly attract the attention of the security officers. It is possible that after a while the pative will come to visit, and people who have left it will politely ask never to use programs for encrypting voice communications.
Published almost every day, new details concerning the work of the PRISM electronic intelligence program of the American National Security Agency (NBA) have caused quite a predictable reaction in society.
Citizens of the United States and other countries began to be massively interested in various alternative search engines, social networks and other online services that provide for an increased level of confidentiality of communication and anonymity of their users, and in particular encryption.
And given the fact that both Apple and Google were convicted of involvement in the PRISM program (at least in terms of collecting metadata from Verizon Wireless operators), many mobile users were puzzled by finding ways to protect their smartphones and tablets from the undue attention of special services, and simply from prying eyes.
Of course, everything is quite complicated: switching to another website, renegotiating a contract with another provider and buying a new mobile device are not the measures that allow you to hide from PRISM.
To protect your personal information, let's say, at the household level, experts recommend using rapid data encryption in smartphones and tablets.
This method means that before being sent, the data is first encrypted on the outgoing device, and after being sent, it is decrypted on the receiving device. This sounds a bit spy. But in practice, operational encryption looks less mysterious, works quite efficiently and looks like ordinary mobile applications that allow you to transfer data bypassing servers controlled by PRISM.
There are a lot of software products that use operational encryption, although they are not among the super popular. Here is a small list of mobile applications and services with which your smartphone and / or tablet will be able to withstand much more successfully both PRISM and other equally unpleasant tracking systems from data collection.
Encryption of telephone conversations
- RedPhone (for Android): Free open source software that can encrypt phone calls. Of course, RedPhone is only effective when installed on both (or all) mobile devices participating in the conversation. RedPhone works over Wi-Fi or mobile Internet, and not through a telephone connection, thus a mobile operator cannot access the metadata of a telephone conversation.

- Silent Phone (for iOS and Android): Provides a certain monthly fee, however, unlike RedPhone, it allows cross-platform calls. In Silent Phone, the user is provided with a unique 10-digit number that can be used in parallel with the usual number of the operator company. For an additional fee, Silent Phone customers can also use their numbers to call third-party subscribers, however, in this case, the encryption of the conversation will be one-way.


- ChatSecure (for iOS) encrypts data transmitted by the participants in the conversation, works with Google Chat and Jabber (* you can download Jabber ), can also be used for cross-platform data transfer.

- TextSecure (for Android) developed by the authors of RedPhone and can be used as a replacement for the standard Android application for sending SMS / MMS messages. To protect data, TextSecure must also be installed on all mobile devices participating in the correspondence. It is also worth noting that in its present form, TextSecure allows mobile operators to receive conversation metadata, but the developers promise to solve this problem in the next version of the application.
- Ekboo (for BlackBerry) is a BlackBerry BBM encryption plug-in with a separate TextBomb feature that allows you to send text messages that are automatically deleted after a user-specified time.
Encrypt mobile data

- Orweb (for Android) - the program was created by the specialists of the Guardian Project and recommended for use by the Electronic Frontier Foundation. Orweb is a web browser that uses the free Tor software to bypass network restrictions and encrypt a user's network activity. In other words, Orweb allows you to hide which device is used to surf the web, control cookies and block Flash. In addition, Orweb does not store any browsing history. To work more efficiently with Orweb, its developers advise you to use Orbot .
- Onion browser (for iOS): For just $ 1, an iOS user is given access to the Tor network, as well as the ability to hide their IP address and web activity.
Encrypting email messages

- Enlocked (for iOS, Android and other OS) can be downloaded and installed as a regular application on any iOS or Android device, where it will function as a plug-in to a standard web browser. Enlocked allows you to send and receive encrypted emails in Gmail, Yahoo, AOL, and Outlook. Enlocked is distributed free of charge, the only condition for using the program is that it must be installed on the mobile devices of all participants in the correspondence.
About the bill, which was supposed to prohibit the use of uncertified mobile devices by officials, since, according to the author of the bill, they pose a threat to national security. Still would! If the American special services found out what our deputies are talking about, then they would understand that they will never defeat our country! After all, if we somehow develop with such elected, then what will become of us if adequate people come to the State Duma? ..
Last time I considered various alternatives to the usual iPhone deputies, but they all have one thing in common - you need to give up your usual phone and switch to a new device or carry a second one with you, especially for confidential negotiations. Is it convenient? Of course not. Therefore, I am in at the very end of the last note and suggested that no one voluntarily would give up their Vertu and iPhones. And here the other day journalists asked me a question - have I heard about Russian headsets for mobile devices that encrypt voice traffic starting immediately from the headset? .. I didn’t hear it, but I started digging. Actually, the brief results of my digging (no claim to completeness).
So, if we discard the option of ensuring privacy on the phone itself (too much dependence on the version of the mobile OS and platform) and using a special telephone set (inconvenient), then we have two whole options for solving the problem:
- encrypt in the headset itself
- encrypt in a "layer", an intermediate crypto-module between the headset and the phone.
Journalists also told me about the first option, mentioning Ruselectronics, which should flood the Russian market with specialized headsets with built-in encryption. But no matter how I looked, I never found an enterprise that would have already produced such devices. I thought that it might be the Oktava design bureau in Tula, which specializes in the production of headsets for security officials, special services, the Ministry of Emergency Situations, etc., but I did not find anything from them that had anything to do with cryptography. There was also a statement by Ruselectronics about the release of crypto modules for YotaPhone, but it has little to do with headsets - a clear dependence on the device's platform.
In principle, modern headsets, such as Plantronics or Jabra, encrypt the voice from the microphone to the computer (or whatever device the headset connects to) using the 128-bit E0 algorithm, which is part of the Bluetooth protocol. But this option does not provide protection of the voice connection from subscriber to subscriber. Rather, it is a solution for protecting a wireless connection from a headset to a computer or phone, between which there can be up to 100-120 meters. It is logical to assume that such a channel in an unprotected version is easily tapped and therefore requires protection.
I did not find more cryptographic information protection devices built into the headsets. But then I found several implementations of the second solution I mentioned. For example TopSec Mobile from Rode-Schwarz.
It is a hardware device that does not depend on the phone or computer model it connects to. Negotiations are conducted either through TopSec Mobile itself, brought to the mouth during a call, or through a headset connected to the cryptomodule. The only drawback of this approach is the presence of a dedicated call control server between subscribers registered on the server. But this is a necessary condition for building distributed interaction systems.

The second device I found was the "GUARD Bluetooth" scrambler of the domestic company LOGOS. A primordially shovel device. There is no design as such. The headset is firmly "sewn" into the device and can only be replaced with the device. But the protection of negotiations is guaranteed - the device is connected via Bluetooth to a transmitter - a computer or a phone (not a word is said about protecting a Bluetooth channel using E0). The device has not been tested, but its review can be found on the net. The appearance of "GUARD Bluetooth" in comparison with the same TopSec Mobile gives a very good idea of how the domestic and Western cryptographic information protection tools are related (both in appearance, and in terms of ease of use, and functionality). But for the operation of this device, no external server is required - it can work "point-to-point".

The final solution that I would like to consider is the IndependenceKey, which aims to protect various types of interactions between users. Among the protected types of communication, there is also voice communication. However, this device is a kind of intermediate option between an independent cryptomodule and security software. In particular, a headset is connected to the IndependenceKey module, from which the voice encrypted in the module is transmitted, but then it goes to the software installed on a personal computer, where the IndependenceKey is inserted into the USB connector. It will be problematic to connect it to the phone.

These are the solutions. True, none of them is certified, and it is unlikely to be. Maybe Ruselectronics will delight you with something interesting in the near future? ..