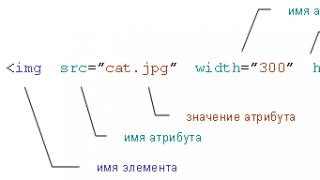
Description:
Router Scan is able to find and identify various devices from a large number of well-known routers / routers and, most importantly, extract useful information from them, in particular the characteristics of the wireless network: how to protect the access point (encryption), access point name (SSID) and access point key (passphrase).
Additional Information:
It also receives information about the WAN connection (useful when scanning a local network) and displays the brand and model of the router. Information is obtained in two possible ways: the program will try to find a login / password pair for the router from the list of standard passwords, as a result of which it will gain access. Either non-destructive vulnerabilities (or bugs) for a specific router model will be used to obtain the necessary information and / or bypass the authorization process.
The program will help you remember the login / password to enter the settings of your router, as well as the security key from your Wi-Fi network.
The program finds its router in 2-3 seconds, and after 20-40 minutes of scanning, it finds other devices. If you need to find data about your device, then after 10 seconds. the program can be stopped and turned off.
What's new in version 2.53:
(build 04.11.2015)
1. Added models of routers: (see the documentation for a complete list)
2. Updated parsers: (see the documentation for a complete list)
3. Added the ability to customize the table of successful results (selection by successful authorization, wireless or wired devices, as well as additional information)
4. Added generation mode selection: off, automatic, or always on (automatic mode checks delays and can turn off generation when resources are used intensively)
5. Fixed line break bug when copying device information
6. The range editor is now able to pull the IP address from the URL
7. Improved loading of program settings - if there are no settings files, they will be created with default parameters
8. Slightly improved utilization of streams during timeout or forced stop
9. Added the ability to exclude certain IP addresses with ports from scanning
10. Now you can select all records in the selected table at once by pressing Ctrl + A
11. Added support for downloading found access points to the 3WiFi database
12. Fixed bug of UTF-8 encoding when exporting reports
13. The HNAP module will now skip the check if the main module has successfully received all the information before (to force the HNAP vulnerability check - disable the main module)
14. Fixed a freeze bug with frequent pressing on pause scanning
15. The number of active threads in the status bar is now displayed in two numbers - active threads of the port scanner and handler
16. HTTP Referer headers are now sent automatically
17. Fixed bug with importing the last CSV column
18. Added function for debug recording of TCP packets
19. Added D-Link DAP-1360 exploit to bypass authorization and obtain administrator password
20. Updated authorization dictionaries
21. Reports in TXT and CSV formats now support only UTF-8 encoding (export / import)
22. Position and size of the window are now saved in the settings
23. Fixed a bug with changing the interval for automatic saving of results in the settings
24. Added Micro DSL exploit (Sagemcom) to get administrator password (https://www.exploit-db.com/exploits/37801/)
25. Fixed bug with importing CSV with double quotes at the end of the field
26. Added exploit for ASUS Boa ADSL (service account)
27. Tab characters are now filtered when entering ranges
28. WPS PIN Companion can now import BSSID list from JumpStart Wireless software (also known as TP-LINK QSS)
29. Fixed bug in checking IP exclusions from scanning
30. Improved use and utilization of scan threads, now the program consumes less system resources
31. The set of provided LibRouter APIs has changed, when using the library in your applications, see the updates in the manual
32. Port 4343 added to the list of HTTPS ports
33. Added an exploit to get the administrator name and password on Realtek eCos Webs devices
34. Added exploit to get administrator name and password on D-Link COMM firmware
35. Fixed bug with automatic installation of the definition page during the initial redirection
36. Added the ability to import reports by adding them to the existing data in the table
37. Added the ability to set a comment for several lines at once
38. Added the ability to delete rows in the main table and search results
39. When the stream stops, all open connections are automatically terminated.
40. When Watchdog is enabled, the IP address will be logged, during the scan of which problems with the connection were found
41. Now in the range editor, you can double-click by mistake to select the problem line
42. Added an exploit for obtaining data from some NETGEAR access points without authorization
43. Added an exploit to get the name and password of some D-Link access points without authorization
44. Fixed bug in HTTP client when processing redirection to HTTPS
45. Added a license agreement and improved documentation for the program
Portable Features:
Portable version of the program, works without installation on a computer.
Router Scan is able to find and identify various devices from a large number of well-known routers / routers and, most importantly, extract useful information from them, in particular the characteristics of the wireless network: how to protect the access point (encryption), access point name () and access point key ( passphrase). It also receives information about the WAN connection (useful when scanning a local network) and displays the brand and model of the router. Information is obtained in two possible ways: the program will try to find a login / password pair for the router from the list of standard passwords, as a result of which it will gain access. Either will be used non-destructive vulnerabilities (or bugs) for a specific router model, allowing you to obtain the necessary information and / or bypass the authorization process.
Version 2.51
1. Added models of routers:
- @irLAN:
R04P (wired)
- 3Com:
OfficeConnect (in development)
- Boa ADSL:
Sitecom Wireless 300N
- Cisco:
WAP4410N
- D-Link:
DES-2108 (wired)
DVG-N5402GF
DVG-N5402SP
— :
@irLAN WR150
- ECI:
B-FOCuS (wired)
- EVDO 3G Firmware:
Shenzhen AirTouch 3G Wireless Router
- Huawei:
HG8240 (wired)
HG8240R (wired)
HG8245T
WS319
- Micro DSL:
Eltex NTP-RG-1402G-W
Eltex NTP-RG-1402G-W Rev. C
Siemens ADSL SL2-141
TP-LINK TD-W8960N V4
- NETGEAR:
WNDR3700
- ONT GPON Home Gateway:
Cambridge Wireless Router
- OpenWrt LuCI:
TP-LINK TL-WR841N / ND v9
- OpenWrt X-Wrt:
Eltex NTE-RG-1402F (wired)
Eltex NTE-RG-1402G (wired)
Eltex NTE-RG-1402G-W
- Thomson:
Firmware STCF.01.16
Firmware STCF.07.02
Firmware STED.07.01
- TP-LINK:
TL-MR3020
- ZyNOS ADSL:
Kraun Wireless Router ADSL2 / 2 +
- Other:
Verizon Jetpack MiFi (in development)
ZyNOS / TP-LINK (in development)
MikroTik Router (under development, there may be bugs)
2. Updated parsers: OpenWrt LuCI, D-Link DSR, D-Link VoIP, Huawei Tech 1, Huawei Tech 2, Thomson / Technicolor, GPON ONT, EVDO 3G, Micro DSL, DD-WRT, NETGEAR WNR
3. Added exploitation of a vulnerability for D-Link DSR routers with old firmware - bypassing authorization and obtaining an administrator password (http://www.exploit-db.com/papers/30061/)
4. Fixed bug with saving XML with disabled columns (all are saved with the correct column width)
5. Added exploitation of vulnerability for ECI B-FOCuS switches - getting administrator name and password
6. Fixed a bug when copying to the clipboard the URL of the host with port 443 (link to HTTPS)
7. Partially fixed a design bug - the size of the scroll bar in tables
8. Fixed order of authorization check (Use credentials function)
9. Fixed a bug in determining the type of authorization during the initial redirection
10. Fixed processing of router Huawei HG8245H
11. Most of the parsers have been transferred to a new format, there may be degradations and bugs, testing is required
12. Now the state of the main window is saved in the settings (normal or maximized to full screen)
13. Fixed display of time (hours were displayed more than 24)
14. Now the contents of the tables move when dragging the sliders
15. Added exploitation of vulnerability for Boa ADSL / Ralink firmware - getting administrator name and password
16. Added support for rebranded DD-WRT WISPR / Optisprint
17. Fixed bug with copying device information
18. Added exploitation of vulnerability for Technicolor / Thomson - getting network settings without authorization
19. Added a query when stopping scanning (useful, because in some cases you can press accidentally)
20. Added exploitation of vulnerabilities for NETGEAR - obtaining administrator password and network settings (http://cxsecurity.com/issue/WLB-2015020059)
Demonstration of the program.
Description:
Router Scan is able to find and identify various devices from a large number of well-known routers / routers and, most importantly, extract useful information from them, in particular the characteristics of the wireless network: how to protect the access point (encryption), access point name (SSID) and access point key (passphrase).
Additional Information:
It also receives information about the WAN connection (useful when scanning a local network) and displays the brand and model of the router. Information is obtained in two possible ways: the program will try to find a login / password pair for the router from the list of standard passwords, as a result of which it will gain access. Either non-destructive vulnerabilities (or bugs) for a specific router model will be used to obtain the necessary information and / or bypass the authorization process.
The program will help you remember the login / password to enter the settings of your router, as well as the security key from your Wi-Fi network.
The program finds its router in 2-3 seconds, and after 20-40 minutes of scanning, it finds other devices. If you need to find data about your device, then after 10 seconds. the program can be stopped and turned off.
What's new in version 2.53:
(build 04.11.2015)
1. Added models of routers: (see the documentation for a complete list)
2. Updated parsers: (see the documentation for a complete list)
3. Added the ability to customize the table of successful results (selection by successful authorization, wireless or wired devices, as well as additional information)
4. Added generation mode selection: off, automatic, or always on (automatic mode checks delays and can turn off generation when resources are used intensively)
5. Fixed line break bug when copying device information
6. The range editor is now able to pull the IP address from the URL
7. Improved loading of program settings - if there are no settings files, they will be created with default parameters
8. Slightly improved utilization of streams during timeout or forced stop
9. Added the ability to exclude certain IP addresses with ports from scanning
10. Now you can select all records in the selected table at once by pressing Ctrl + A
11. Added support for downloading found access points to the 3WiFi database
12. Fixed bug of UTF-8 encoding when exporting reports
13. The HNAP module will now skip the check if the main module has successfully received all the information before (to force the HNAP vulnerability check - disable the main module)
14. Fixed a freeze bug with frequent pressing on pause scanning
15. The number of active threads in the status bar is now displayed in two numbers - active threads of the port scanner and handler
16. HTTP Referer headers are now sent automatically
17. Fixed bug with importing the last CSV column
18. Added function for debug recording of TCP packets
19. Added D-Link DAP-1360 exploit to bypass authorization and obtain administrator password
20. Updated authorization dictionaries
21. Reports in TXT and CSV formats now support only UTF-8 encoding (export / import)
22. Position and size of the window are now saved in the settings
23. Fixed a bug with changing the interval for automatic saving of results in the settings
24. Added Micro DSL exploit (Sagemcom) to get administrator password (https://www.exploit-db.com/exploits/37801/)
25. Fixed bug with importing CSV with double quotes at the end of the field
26. Added exploit for ASUS Boa ADSL (service account)
27. Tab characters are now filtered when entering ranges
28. WPS PIN Companion can now import BSSID list from JumpStart Wireless software (also known as TP-LINK QSS)
29. Fixed bug in checking IP exclusions from scanning
30. Improved use and utilization of scan threads, now the program consumes less system resources
31. The set of provided LibRouter APIs has changed, when using the library in your applications, see the updates in the manual
32. Port 4343 added to the list of HTTPS ports
33. Added an exploit to get the administrator name and password on Realtek eCos Webs devices
34. Added exploit to get administrator name and password on D-Link COMM firmware
35. Fixed bug with automatic installation of the definition page during the initial redirection
36. Added the ability to import reports by adding them to the existing data in the table
37. Added the ability to set a comment for several lines at once
38. Added the ability to delete rows in the main table and search results
39. When the stream stops, all open connections are automatically terminated.
40. When Watchdog is enabled, the IP address will be logged, during the scan of which problems with the connection were found
41. Now in the range editor, you can double-click by mistake to select the problem line
42. Added an exploit for obtaining data from some NETGEAR access points without authorization
43. Added an exploit to get the name and password of some D-Link access points without authorization
44. Fixed bug in HTTP client when processing redirection to HTTPS
45. Added a license agreement and improved documentation for the program
Portable Features:
Portable version of the program, works without installation on a computer.
We present to your attention a new course from the team The codeby- "Penetration Testing of Web Applications from scratch". General Theory, Work Environment Preparation, Passive Fuzzing and Fingerprinting, Active Fuzzing, Vulnerabilities, Post-Exploitation, Tools, Social Engineering and more.
By the way, this Router Scan from Stas'M is amazing! What I like most about this program:
- scanning, which shows both routers and other hardware and software elements (cameras, servers, etc.)
- brute force attack of typical passwords for found routers
- use of exploits for a number of routers
- if it was possible to guess the password or the exploit worked, then all the information that we managed to get is parsed. And this, usually, a login password, a Wi-Fi password, local network data, etc.
The program is unique in that, in the best traditions of graphical interfaces, you need to press one button and it will do everything by itself. No knowledge is needed.
I liked the program to such an extent that I began to look for alternatives for Linux. I did not find alternatives.
But the main idea of this program - to scan the network and look for routers with default passwords or with weak firmware - seemed so amazing to me that I wanted to do something similar for Linux. This is a task of medium complexity, that is, quite achievable. Fortunately, most of the modules are already ready-made: nmap (for port scanning) + curl (for authentication and using exploits) + grep (for parsing authentication pages (when determining the router model) and parsing passwords and other useful things with a successful password guess / exploit application) ...
I even managed to make a working concept that collected over 1000 Wi-Fi passwords for me in a day. The concept turned out to be terribly slow: the scanner is written in PHP, and it is written without any optimizations - everything is done in one thread, and the scanner is implemented on an attempt to establish a socket connection. Those. if the connection occurs, it means it starts trying standard passwords and pulling information out of the router if successful. If the connection does not occur, then the program waits until the timeout has elapsed. It is clear that more often the connection does not occur and, as a result, almost all the time the program is waiting for the end of timeouts. All this can be accelerated and optimized, new router models can be added. In general, if over the summer there is enough time to finish (at least on the basis of nmap, at least based on PHP) to the level of "not ashamed to show the source code", then I will definitely share my work. Fortunately, the exploit algorithms used in the Stas'M router scanner are available as source codes and can be easily rewritten under curl.
Let's go back to Router Scan from Stas'M. He's gorgeous! With it, you yourself can collect a lot of passwords from routers, from Wi-Fi networks and learn a lot about networks and the devices that live there.
If you are a Windows user, then everything is quite simple for you - download, launch, enter a range of addresses and wait for the scan to finish.
For Linux users it is also possible to run Stas'M's Router Scan program under Wine. I'll show you how to do this using Kali Linux as an example.
Installing Wine on Kali Linux
Attention, if you have Kali 2.0, then go to the instructions "".
If you look at the information about the Wine package in Kali Linux, it will indicate that the package is already installed. If you try to start it, you will find out that this is just a stub, which tells how to carry out the installation. The entire installation is done with three commands:
Dpkg --add-architecture i386 apt-get update apt-get install wine-bin: i386
Next, download Router Scan from Stas M (http://stascorp.com/load/1-1-0-56), unpack (to any place), right-click on the RouterScan.exe file, select “Open with using Wine ... ", and then everything is like on Windows.
Here's an example of how Stas'M's Router Scan works in Linux (I scan the address ranges of my hometown of Murom):

Only good results:

If someone does not fully grasp the principles of the program:
- the program does not need a Wi-Fi receiver or anything else - it works over a wired connection;
- to try to hack a neighbor's Wi-Fi (and not on the other side of the world), you need to know the IP of the neighbor, or at least the IP range of the neighbor's Internet provider. You can use
New 2019:
Beta version 2.60 has been released with wireless network auditing capabilities, if you have any problems with downloading, use Download Master or a browser plugin friGate.
What's new:
Version 2.53
1. Added models of routers:
2. Updated parsers:
(see the documentation for a complete list)
3. Added the ability to customize the table of successful results (selection by successful authorization, wireless or wired devices, as well as additional information)
4. Added generation mode selection: off, automatic, or always on (automatic mode checks delays and can turn off generation when resources are used intensively)
5. Fixed line break bug when copying device information
6. The range editor is now able to pull the IP address from the URL
7. Improved loading of program settings - if there are no settings files, they will be created with default parameters
8. Slightly improved utilization of streams during timeout or forced stop
9. Added the ability to exclude certain IP addresses with ports from scanning
10. Now you can select all records in the selected table at once by pressing Ctrl + A
11. Added support for downloading found access points to the 3WiFi database
12. Fixed bug of UTF-8 encoding when exporting reports
13. The HNAP module will now skip the check if the main module has successfully received all the information before (to force the HNAP vulnerability check - disable the main module)
14. Fixed a freeze bug with frequent pressing on pause scanning
15. The number of active threads in the status bar is now displayed in two numbers - active threads of the port scanner and handler
16. HTTP Referer headers are now sent automatically
17. Fixed bug with importing the last CSV column
18. Added function for debug recording of TCP packets
19. Added D-Link DAP-1360 exploit to bypass authorization and obtain administrator password
20. Updated authorization dictionaries
21. Reports in TXT and CSV formats now support only UTF-8 encoding (export / import)
22. Position and size of the window are now saved in the settings
23. Fixed a bug with changing the interval for automatic saving of results in the settings
24. Added Micro DSL exploit (Sagemcom) to get administrator password (https://www.exploit-db.com/exploits/37801/)
25. Fixed bug with importing CSV with double quotes at the end of the field
26. Added exploit for ASUS Boa ADSL (service account)
27. Tab characters are now filtered when entering ranges
28. WPS PIN Companion can now import BSSID list from JumpStart Wireless software (also known as TP-LINK QSS)
29. Fixed bug in checking IP exclusions from scanning
30. Improved use and utilization of scan threads, now the program consumes less system resources
31. The set of provided LibRouter APIs has changed, when using the library in your applications, see the updates in the manual
32. Port 4343 added to the list of HTTPS ports
33. Added an exploit to get the administrator name and password on Realtek eCos Webs devices
34. Added exploit to get administrator name and password on D-Link COMM firmware
35. Fixed bug with automatic installation of the definition page during the initial redirection
36. Added the ability to import reports by adding them to the existing data in the table
37. Added the ability to set a comment for several lines at once
38. Added the ability to delete rows in the main table and search results
39. When the stream stops, all open connections are automatically terminated.
40. When Watchdog is enabled, the IP address will be logged, during the scan of which problems with the connection were found
41. Now in the range editor, you can double-click by mistake to select the problem line
42. Added an exploit for obtaining data from some NETGEAR access points without authorization
43. Added an exploit to get the name and password of some D-Link access points without authorization
44. Fixed bug in HTTP client when processing redirection to HTTPS
45. Added a license agreement and improved documentation for the program
Router Scan is able to find and identify various devices from a large number of well-known routers / routers and, most importantly, extract useful information from them, in particular the characteristics of the wireless network: how to protect the access point (encryption), access point name (SSID) and key access points (passphrase). It also receives information about the WAN connection (useful when scanning a local network) and displays the brand and model of the router. Information is obtained in two possible ways: the program will try to find a login / password pair for the router from the list of standard passwords, as a result of which it will gain access. Either will be used non-destructive vulnerabilities (or bugs) for a specific router model, allowing you to obtain the necessary information and / or bypass the authorization process.