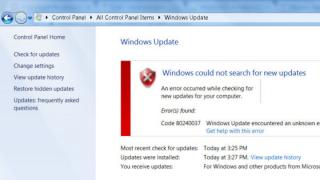
Last June, a scandal erupted in Ukraine around mobile operator"MTS-Ukraine", associated with illegal "wiretapping" of telephone conversations of Ukrainian subscribers. As it turned out, the MTS-Ukraine network suffered an unprecedented hack. Using a vulnerability in the GSM protocol, FSB agents switched some of the operator's subscribers to a server belonging to the Russian subsidiary of Tele2, as a result, the conversations of Ukrainian MTS subscribers were available to Russian special services.
In addition, as recently as yesterday, Kyivstar turned off a segment of the mobile communications network in the part of the Donetsk and Lugansk regions captured by the militants. The network was shut down due to freelance work that arose for unspecified reasons. The press service explained that since part of the Donbass is temporarily not controlled by the Ukrainian authorities, there is no possibility of physical control of the network. In other words, Kyivstar specialists suspected physical penetration into the network, that is, an attempt to install wiretapping. It’s not hard to guess who tried to install it, at least, not homeless people or bandits who proudly call themselves “militia”. The trail leads all the way to the same place – to its northern neighbor.
Thanks to the revelations of Edward Snowden, we learned that intelligence services wiretapping the phones of even the most senior government leaders is not difficult. And although most subscribers have absolutely nothing to hide (“Do you want to hear how my friends and I drank beer yesterday? So listen, we don’t mind”), sometimes they still want confidentiality. Of course, you are unlikely to be of interest to any intelligence agency (be it the SBU, FSB, NSA or CIA), but caution will not hurt. Moreover, achieving a completely sufficient level of privacy is not at all difficult if you turn to the following applications for smartphones on Android.
Orbot: proxy included with Tor
Orbot is free proxy server, which provides a secure Internet channel for various applications. To encrypt Internet traffic, Orbot uses the anonymous Tor network, which helps protect against online surveillance. According to New edition York Times, "When a connection comes from the Tor network, there is no way to know who or where it was activated from."
According to experts, Orbot truly creates a completely confidential connection and this is the most safe way for web surfing on the Android platform. Orbot redirects the user's encrypted traffic several times through computers around the world instead of connecting directly, as happens in VPN networks. Of course, traffic delivery in this case takes a little longer, but confidentiality and protection of the user profile are guaranteed.
In universal mode, Orbot can be configured to transparently pass all traffic through Tor. Also, the user can select specific applications whose traffic should be passed through Tor.
Orweb: private web browser
The Orbot proxy server is used in conjunction with other applications, such as Orweb, a private web browser that supports a proxy connection. When used in conjunction with Orbot, the Orweb web browser protects against analysis network traffic from the supervisory authorities, blocks cookies, deletes web browsing history and disables Flash for greater security.

ChatSecure: Encryption of chat messages
The free application provides unlimited exchange of encrypted private messages in GoogleChat (GChat), FacebookChat, VKontakte, Yandex, Hyves, Odnoklassniki, StudiVZ, Livejournal and Jabber. The application works on Android, iPhone, Mac, Linux and Windows platforms.

OTR encryption is used to protect messages. As a result, no one will be able to intercept or view your messages. It's worth noting, however, that all of these security measures only work if your interlocutors are using a compatible OTR client, such as ChatSecure, Adium or Pidgin.
Ostel: encryption of telephone conversations
The free Ostel utility is designed for full end-to-end encryption of phone calls. This public test application of the Open Secure Telephony Network (OSTN) project aims to promote free, open protocols, standards and software designed for securely protected voice communications on mobile devices and desktop computers. The utility is fully integrated with the CSipSimple application for Android. The OSTN Setup Wizard is included. To make calls, just enter your name, password and ostel.co!
DuckDuckGo: Safe Search
According to the developers, the DuckDuckGo search service does not collect user information at all. The app provides true privacy, no matter what you're trying to find.

Function smart search helps you quickly find what you are looking for. For this, instant responses from hundreds of sources are used, as well as requests to thousands of other sites.
CSipSimple: VOIP telephony encryption
CSipSimple is a free opensource SIP client for Android that provides end-to-end encryption using the TLS encryption algorithm for SIP, and SRTP/ZRTP for media files. It features easy setup, the ability to record calls, and an attractive interface.
TextSecure: SMS protection
The utility, developed by Whisper Systems programmers, provides reliable encryption of SMS text messages. It goes without saying that both subscribers conducting SMS correspondence must install this program on their Android smartphones.

K-9 and APG: Email Encryption
The open-source K-9 Mail application is based on a built-in utility for working with email on the Android platform. The project allows you to simplify the management of various accounts and large volumes of email, and also supports OpenPGP encryption when using Android Privacy Guard.
PixelKnot: steganography
Steganography involves the hidden transmission of information by keeping the very fact of transmission secret. With a secret message you can hide in graphic representation, and no one around will guess that this is not just a picture, but a “container with a secret.”
![]()
NoteCipher: a secure DBMS
The free NoteCipher app is easy to use Notebook, which stores records in encrypted form in the SQL Cipher for Android DBMS. All records created and saved using this application are encrypted using a powerful industrial algorithm - 256-bit AES. Moreover, NoteCipher never transfers information to open form to disk; when working with recordings, they are all stored in decrypted form only in RAM.
RedPhone – mobile app for Android, which allows you to make encrypted voice calls over Wi-Fi or mobile Internet using regular phone numbers. RedPhone only encrypts calls between two RedPhone users or between RedPhone and Signal users.
You can call other RedPhone users from the application itself or using the standard Android dialer. RedPhone will automatically prompt you to switch to an encrypted call.
Installing RedPhone
Download and install RedPhone
On Android phone run Google Play store and search for "RedPhone". Select the "RedPhone::Secure Calls" application.
Why can't I download RedPhone without registering on Google Play?
Many would prefer to download RedPhone from sources not associated with Google's Google Play service: there is less risk of substitution or data collection by third parties. Unfortunately, today developers use part of Google's infrastructure to update software and send push messages. The position of the developers (using the example of TextSecure) is outlined here.
Click "Install" and accept the "Terms of Use" by clicking "Accept". The program will be automatically downloaded and installed.
Register your mobile number
After the installation is complete, open the RedPhone program. You will be asked to register your mobile phone number.

After completing your phone number registration, RedPhone will send you verification code in an SMS message. This way the program can make sure that the number really belongs to you. When prompted, enter the code you received. You have successfully installed RedPhone and are ready to make encrypted calls!
Using RedPhone
To use RedPhone for calls, the person you want to call must also have RedPhone (or Signal) installed on their mobile phone. If you try to call a person who does not have a RedPhone, the program will offer to send an SMS invitation to the interlocutors to use the RedPhone service, but you will not be able to call from RedPhone (yet).

When you call another RedPhone or Signal user (using the standard dialer or from the app), the program will suggest a random pair of words. This pair will allow you to verify the authenticity of the interlocutor and his keys ( key verification).

The most reliable way to verify the identity of the caller is to use the mentioned pair of words and another communication channel. You can read the words out loud if you know the voice of the interlocutor, but keep in mind that some sophisticated attackers are able to fake the voice. The spoken and written pairs of words must match.
Talking on a cell phone. Is everyone listening?
The topic of wiretapping pops up in the media quite often. As a rule, interest in it appears after the publication of transcripts of conversations of famous people, pop stars and politicians. Let's try to understand the essence of this process.
Wiretapping
There are two main types of encryption for conversations on GSM mobile phones - one is easier to crack, the other is more complex. Just a few years ago, a device capable of tracking no more than 16 mobile subscribers with a complex type of encryption, cost up to half a million dollars on the world market. After combining the efforts of Israeli and US cryptographers, former employees of the largest Soviet defense enterprises scattered around the world, managers from South Africa and manufacturers from Southeast Asia, it was created portable device, which allows you to simultaneously listen to up to 10 thousand mobile lines and costs about $50 thousand. Moreover, this “suitcase” weighing 12 kg is capable of both simple and complex types of encryption. He successfully finds "holes" in the security of cellular modems. The most recent achievement of this device was the recent scandal with wiretapping of the Prime Minister of Greece - according to experts, the new technology was used there for the first time. Improving wiretapping technology also removes the problem of finding a subscriber. To identify the desired subscriber Now it is enough to have an audio recording of his voice. New technology allows you to find a subscriber's voice in less than a minute after he goes online. Frequently changing SIM cards, in this case, does not solve the problem.
Actually, the essence of the problem is that the state has official services who, by the nature of their activities, are engaged in wiretapping civilian conversations. In this case we are not talking about military radio intelligence - this is a separate diocese. Each cellular operator has equipment that forms the System of Operational Investigative Measures - the so-called SORM. Operational wiretapping of conversations is carried out on the basis of sanctions from the prosecutor's office and in accordance with the law. The main struggle is connected precisely with illegal wiretapping, which is carried out by criminal structures, security agencies and security services without any sanctions.
Equipment for listening, spying and other interference in privacy citizens are prohibited for open sale. In Russia, the article of the Criminal Code on telephone wiretapping using special means implies a maximum penalty of arrest for a period of two to four months. For illegal production or sale of special equipment, you can go to prison for three years. But this does not stop criminals. The best remedy Experts consider a scrambler - a special device that encrypts telephone conversations - to protect the phone. With each new phone call, the scrambler generates new key cipher. Scramblers cost $300 - 500. However, they are only suitable for wired telephone lines. All means active protection are subject to mandatory certification, which provides for the possibility of receiving ciphers by employees of law enforcement agencies. But does this mean that cell phone users are completely defenseless against penetration into their privacy? Most recently, a press conference was held in Moscow by a representative of the Secure GSM company, which is developing software for encrypting conversations in real time. But first, a little theory.
Interception
The cipher used in all GSM networks is based on an algorithm that is vulnerable. It has not yet been clarified whether this security hole was left intentionally or whether it simply happened due to an oversight by the developers. Subsequently, attempts were made to improve the encryption algorithm, but for a number of reasons it is impossible to completely change the data encryption standard. Therefore, it was only slightly modified.
The second problem is that traffic encryption occurs only on the segment between the subscriber and the base station of the cellular operator. Between two nearby base stations, the signal is transmitted completely openly via a microwave link using the SS7 standard. In theory, intercepting this signal is very difficult due to the narrow directional beam connecting the two base stations. In practice, such interception does not pose a problem for specialists if they have the necessary equipment. At a distance of about a kilometer, the beam divergence can reach 8 degrees, and this is quite enough to install a receiver. There is also a solution to the problem of selecting the required subscriber from the entire spectrum of transmitted conversation data. A laptop with the appropriate software costs no more than $10,000.
Software eavesdropping protection
The presentation of the program was held under the motto "Protection of telephony without exception". The program is designed to encrypt voice traffic using a 256-bit triple cipher, built on the AES, Twofish, Serpent algorithms, in real time. None of the applied algorithms is currently decipherable. But to be more precise, the material and time costs of decoding make this process impractical.
List compatible devices includes communicators running Windows Mobile and Pocket PC 2003 SE. Recently announced support for HTC Prophet, Charmer, XDA ATOM, Qtek 8310 and similar. Full list supported devices is available on the developer's website - www.securegsm.com. To familiarize yourself with the capabilities of the utility in free access A light version of the SecureGSM Evaluation product has been released, which uses a lightweight encryption mechanism and is distributed free of charge. When purchasing the full version of the program, the following restrictions are assumed:
1. The program may not be sold, leased or transferred to government or military organizations without the official permission of the Australian Department of Defense.
2. The program is not supplied to the following countries: Cuba, Iraq, North Korea, Iran, Libya, Sudan, Syria.
3. Upon registration end user the product must provide its data: full name, actual address, e-mail, telephone.
It is recommended to install the program in the area additional memory(Storage). In this case, in case of a forced hard reboot, to restore the functionality of the program, it is enough to run the startup file through Explorer. In this case, not only all settings are restored, but also the launch icon in the Programs menu.
 At the first launch, a device identification file is created in the program directory, which is sent to the developer. After checking the registration information, the user is sent a modified ID file and a license file, which must be copied to the directory with the program. The license takes into account hardware features specific device. Transferring the program to another device is possible only with the consent of the developers, and is done by canceling the previous license and obtaining a new one.
At the first launch, a device identification file is created in the program directory, which is sent to the developer. After checking the registration information, the user is sent a modified ID file and a license file, which must be copied to the directory with the program. The license takes into account hardware features specific device. Transferring the program to another device is possible only with the consent of the developers, and is done by canceling the previous license and obtaining a new one.
Interface
 At the bottom of the main program window there is a menu of options and quick control icons. From general settings programs available to adjust the ringer volume, microphone sensitivity, access to the program from standard contacts, and automatic activation when the communicator starts. In the presence of established managers personal information(Pocket Informant, Agenda Fusion, SPB Diary, etc.) calls in secure mode are possible directly from the main window.
At the bottom of the main program window there is a menu of options and quick control icons. From general settings programs available to adjust the ringer volume, microphone sensitivity, access to the program from standard contacts, and automatic activation when the communicator starts. In the presence of established managers personal information(Pocket Informant, Agenda Fusion, SPB Diary, etc.) calls in secure mode are possible directly from the main window.
The CSD protocol is used to transmit voice traffic, so the corresponding service must be connected and activated. This protocol is used when transmitting data or faxes. If, upon activation of the service, an additional number is issued, then it is better to use it for calls in secure mode. Although, experiments have shown the possibility of calling a regular number. The default CSD protocol settings are 9600 bps (v.32), which can be immediately changed to 9600 bps (v.110). At the same time, the quality of voice communication is significantly improved. The remaining icons at the bottom of the window allow you to voice call, switch to exchange mode written messages, open your contacts list, adjust audio settings, and open the help file.
Working with the program
 To make a call in secure mode, the program must be installed on both terminals. The subscriber's number can be dialed directly from the keypad or called from address book. If the software is not installed or the CSD channel is unavailable, a message indicating that communication cannot be established is displayed on the screen. If the utility is installed on both terminals, the connection establishment process consists of several stages. After receiving a signal about incoming call Devices are negotiated, then the communicators exchange dynamic keys. Ultimately, a picture containing a geometric figure and a digital sequence is displayed on the screen of both devices. Moreover, both the picture and the sequence are generated dynamically in real time. We conducted several communication sessions in secure mode - each time the picture and digital code were different from the previous call, but they were always the same on both devices. Before the conversation enters the “secret” phase, it is enough to simply inform the interlocutor of the digital code displayed on the screen and the type of picture. If the results on both devices are the same, you can enable confirmation and proceed directly to the conversation.
To make a call in secure mode, the program must be installed on both terminals. The subscriber's number can be dialed directly from the keypad or called from address book. If the software is not installed or the CSD channel is unavailable, a message indicating that communication cannot be established is displayed on the screen. If the utility is installed on both terminals, the connection establishment process consists of several stages. After receiving a signal about incoming call Devices are negotiated, then the communicators exchange dynamic keys. Ultimately, a picture containing a geometric figure and a digital sequence is displayed on the screen of both devices. Moreover, both the picture and the sequence are generated dynamically in real time. We conducted several communication sessions in secure mode - each time the picture and digital code were different from the previous call, but they were always the same on both devices. Before the conversation enters the “secret” phase, it is enough to simply inform the interlocutor of the digital code displayed on the screen and the type of picture. If the results on both devices are the same, you can enable confirmation and proceed directly to the conversation.
The logic of such a verification algorithm is that no one will conduct secret negotiations with unknown people - the voice of the interlocutor is always known. Possible voice distortions when using the CSD protocol must be foreseen in advance - in this case, before conducting secret conversations, it is better to practice several times in order to confidently identify the caller’s voice.
 An additional and unique way of transmitting information in the SecureGSM program is the ability to exchange text messages in protected mode. This possibility immediately prevents the use of directional microphones or bugs built into the device to record a conversation. You can go to the messaging window by clicking the corresponding icon. Previously, this feature was not implemented in any software product. Its convenience can be judged at least by the attempt to convey by voice a simple key of this type IASHER–HDTRIEU–HDTERIOTR–SHDGFGERT–SGKJHIS.
An additional and unique way of transmitting information in the SecureGSM program is the ability to exchange text messages in protected mode. This possibility immediately prevents the use of directional microphones or bugs built into the device to record a conversation. You can go to the messaging window by clicking the corresponding icon. Previously, this feature was not implemented in any software product. Its convenience can be judged at least by the attempt to convey by voice a simple key of this type IASHER–HDTRIEU–HDTERIOTR–SHDGFGERT–SGKJHIS.
Legal basis for the use of encryption algorithms
According to the legislation of Belarus, programs intended for personal use do not require certification. Moreover, only domestic products, to which this program does not apply, are subject to certification. The developers' office is located in Melbourne. This program does not conflict with the requirements of SORM - the operator must provide unhindered access to its equipment for intelligence agencies. According to experts, if necessary, filtering subscribers using such programs does not pose any technical difficulty. In addition, according to law enforcement agencies, the operator has the ability at any time to disable the CSD channel through which encrypted traffic is transmitted. The lack of the ability to talk in secure mode will allow the subscriber to independently decide what information makes sense to broadcast.
To clarify the operator’s position on the issue of restrictions on the use of CSD channels, a corresponding request was formulated. Here we're talking about about operator Velcom Those wishing to clarify the position of other cellular operators can do this independently.
Request:
Hello.
Are there legal restrictions on using the CSD channel? If so, which ones (with links to relevant regulations)? Can the data service be disabled by the operator unilaterally? If so, in what cases? The Agreement does not provide for restrictions on the use of the CSD channel.
Dear subscriber!
By providing the "Data Transfer" service, JV LLC "MCS" provides technical feasibility(transport) for data exchange between a network subscriber and Internet resources or other data transfer devices. When using the CSD service, data transmission is carried out over a standard voice channel. Communication services (including the Data Transfer service) can be disabled by the operator in cases provided for by the provisions of the agreement concluded between you and JV MCS LLC. The Company has the right to disconnect the Client from the GSM network in following cases:
– if the funds on the client’s balance (prepayment) are used in full (clause 3.7 of the agreement);
– in case of technical damage to the Company’s equipment (clause 3.10.1 of the agreement);
– when carried out by the Company preventive work(clause 3.10.2 of the agreement),
– in the event of force majeure circumstances (clause 6.1 of the agreement).
In all other cases not regulated by the agreement on the provision of telecommunication services GSM standard, JV LLC "MCS" is guided by the legislation of the Republic of Belarus.
Best regards, Velcom Customer Service Department
On this holiday, it is customary to congratulate and accept joyful congratulations, both from loved ones and not so close. Yesterday was Forgiveness Sunday, a rare opportunity to ask for forgiveness from the whole world and, perhaps, even receive it. I congratulate men, young men and boys on the fact that they know how to protect their loved ones from various misfortunes, I hint to girls that we need to be groomed and cherished, perhaps in a different order. I like the tradition of asking for forgiveness, a kind of reboot of everything, an attempt to leave all grievances in the past. Therefore, if I suddenly offended someone, then don’t be angry, in front of all the honest people, I apologize. Despite the holiday, we have a whole week ahead of us, which means it's time to prepare for it. Whoever owns the information owns the world. Let's start by figuring out how operators are going to make money during the crisis and what tricks they will use for this.
Operators raise prices for services, gimmicks and tricks
During each economic crisis, communication prices went up along with inflation, although in 2009 many Russian operators cheerfully reported that their service costs were falling and they were becoming more profitable for subscribers. Partly it was true, partly not. The configuration of this crisis is very different from that of 2009 from the point of view of operators. Almost all Russian operators are no longer focused on selling services by weight, that is, at retail, but are trying to offer package deals. That is, you profitably buy a package that contains so many GB of traffic, so many minutes, and certain options. When I say that such a wholesale offer is profitable, it really is for multi-talking subscribers. Let's try to figure out what operators will do so that, on the one hand, they are prepared, and on the other hand, they do not miss out on possible benefits.
Let me remind you that, conditionally, two waves of tariff creation can be distinguished in the Russian market, one in the spring, the second in the fall. In the meantime, existing tariff plans are adjusted, sharpened with a file, and the initiatives of fellow competitors are monitored. For the last ten years, the marketing departments of each operator have been trying to come up with moves when the offer will look beneficial to the consumer, but at the same time bring more money operator. At the first stage, all thoughts hit one point - to make the conditions as confusing as possible so that the devil himself would break his leg in them. Remember this - the first minute of a conversation costs 2 rubles, from the 2nd to the 10th minute inclusive - 0 rubles, then 3 rubles and so on? I could never understand these tariff plans, I was always confused by them and wanted simplicity. Then came the time for "simple" tariffs with one digit. Earned already on data transmission. Operators then began to create bulk package offers.
Why is the package interesting for the operator? The benefit is direct and uncomplicated - they sell a set of services in bulk, and it is not a fact that the consumer will choose all the services. By cutting the tariff line not very finely, you will get a good step in the number of services sold. The main task is to ensure that these tariffs are exactly in the middle of average consumption. For example, you see large group subscribers who consume an average of 500 MB of traffic per phone per month. They should be given 1 GB of traffic, this will increase the network congestion, which is also not bad, but the main thing is that people will not use up all the traffic. If we look at the statistics of one of the operators, we will see that consumers with 500 MB are gradually migrating to 700 MB, that is, there is still 300 MB left in stock. A complete increase in consumption and, accordingly, a change in people’s tastes takes from six months to a year. Every operator today is trying to get subscribers hooked on data transmission; voice sales have long risen and are falling, but data is growing. And here we need to teach even the slowest-speaking subscribers to surf the Internet, play online games, and watch movies online. As soon as a group of subscribers breaks the average limit of their tariff, the bar is raised again for them and a new tariff plan is released. It costs a little more, but GB is also poured into it more. In terms of one GB, it turns out to be more profitable than it was before.
Packages have another huge advantage - a person who is used to paying for a package knows approximately how much he spends on communications every month. And people get used to this amount, the operator can high accuracy guess what the cash flow will be. And this is an important parameter for him. During this crisis, all creativity will go into tuning package offers, and they will be quite interesting. Moreover, for most, the increase in tariffs will not be noticeable, since we will receive a high-quality service (count GB of traffic for our money). Those who want to stay on the old tariffs will be able to do so for a while. It turns out that there will be no coercion. That is, you can independently choose what and how to use it. However, in April we can expect an average increase of 10-15 percent, but we cannot say that this will be an increase in prices for everything. In fact, this growth will be spread across new proposals.
Those who do not take advantage of package offers will face increased prices for mobile traffic. It was already very expensive (1 MB for 10 rubles, as an example), and now it will become even more expensive. The same MegaFon introduced a minimum tariff per session of 1 MB. Let me explain - every time you access any service, for example, weather, where at most 10 KB are transferred, you will be charged as one megabyte. Robbery? Definitely. But this is a gentle reminder that you need to choose the smallest package, where the cost per megabyte will be an order of magnitude less.
Another trick that all operators will do is cancel free options or increase the cost of additional options in your tariff plans. The operator can, but does not seek to change the basic parameters of tariff plans; it is easier to introduce new tariffs to the market. And unilateral price changes always cause people's indignation. Less outrageous is the cancellation of free options, which are warned about on the operator’s website. Usually warnings come out on Friday evening, in the news archive, and not a single (normal) person sees them. They charge you a little more, you hardly notice it in your bills. By the way, all operator sites for this case are registered as media outlets, which allows you not to send you SMS messages. Pre-installed free options tend to turn into paid options after a certain period.
If you do not want to fall for such tricks, then you need to control what is happening. In 2015, this became noticeably easier to do than five years ago. Just go to your personal account on the operator’s website and see all the services that are connected to your number. Sometimes I hear from people that they do not want to monitor the operator, but dream that he will honestly track all expenses and not add unnecessary services. Utopia, since the responsibility for tracking what you use lies solely with you. This is an unpopular point of view, but still, after reading these lines, mark on your phone that you need to go to your personal account and see what you are using. At the same time, tell us what discoveries you made. It is possible that no unpleasant discoveries await you at all. But it's interesting.
In 2015, operators will closely monitor that users do not “optimize” their costs by buying SIM cards from other regions. In the last two years, it has become popular to buy a card in Tver and use it in Moscow (as an example only). You get more traffic for less money, and the savings are noticeable. If earlier operators turned a blind eye to this, now they will introduce all sorts of slingshots so that such “optimizers” cannot use such a trick.
Prices for international roaming have already increased, which was inevitable, since partners do not set prices in rubles, and the number of tourists coming to Russia (mutual offsets as a consequence) is small. Buying a local SIM card, as always, remains a rather interesting way out of this situation.
The bottom line is this picture. The mobile communications services market will carry out a very mild price increase, in which users will often not even feel it. You need to more closely monitor your services and changes in tariffs, track your bills (the bill has changed by so many percent, for example, they paid an average of 500, and then suddenly 600 - it’s a direct way to figure out what has changed). I hope this short excursion Operators' tricks will help you plan your communication expenses correctly and not spend more than usual.
How much time do you spend on your phone?
So, let's take a guess at how much time you spend on your phone. Think for a minute, try to remember how often you take out your phone, look at the weather, messages, mail or something else on it. Ten times a day? This is probably very little. Fifty times? One hundred? How many?
Not too long ago I read a rather amusing study that stated that every year we are starting to spend more time on our phones. A graph was presented in which the time curve gradually climbed upward. I decided to check how things were going with this for me, and performed an inhuman experiment on myself.
One of the programs that appeared on Android quite a long time ago is BreakFree, it can count how often you unlock the device, what applications you are using (this costs money, it just doesn’t show it).

But what I liked more was the Instant program (also available for iOS), application tracking also costs money (67 rubles per year, you can subscribe for a week for free).


Not everything is perfect in Instant either, but at least you can see the number of unlocks and usage time. At the peak, when I was counted 380+ minutes a day, my navigator was running in the background, the program was stupid, thinking that I was looking at the screen, although it was turned off. As you can see, there were some mistakes. But in general, everything is calculated correctly.
On weekends, when I have quiet time, I pick up the phone about 70-80 times (number of unlocks), on weekdays it’s 150-180 times. Crazy number! Think about how much time I spend with this device, on which I watch videos, answer emails, and surf some social networks. Am I addicted to my phone? Definitely not (every patient denies his addiction!). But it is true that this tool takes a lot of time.
I would like to invite you to participate in a small experiment for a week. Let's try one of these programs and then share your data. I am sure that you yourself will be curious to know how much time you spend on your phone, what you do, and so on. This is not at all as obvious information as it might seem at first glance. For example, I thought that in my case Twitter would come first, but it turned out that it was the Royal Revolt 2 toy, which I recently came across and now play from time to time. After I saw how much time I was wasting, I stopped playing. That is, such software certainly has useful feature– pull back, force you to control the time you spend. Of course, this won't suit everyone. Some people know how to do this consciously, others waste their time thoughtlessly, and the program will not help the matter in any way.






Send me your results on Saturday or Sunday, try to describe yourself and your lifestyle a little, so that in the next “Spillies” we will already talk with examples of who uses their phones and how. Thank you in advance for participating in our little experiment.
Hacking Gemalto and SIM card encryption key data
Almost every cell phone has a SIM card, it may vary in size, but not in function. This is a kind of key that opens the door to the world of cellular communications. The cards differ in memory capacity and functionality, but in all cases the SIM card contains encryption keys that allow you to establish a connection with the operator. When cloning SIM cards, almost all information is transferred to a blank, but it is impossible to crack the encryption key; it is a 128-bit cryptographic key. Each SIM card has two unique parameters that are not the same in theory with any other card - this is the IMSI number, as well as the 128-bit Ki authentication key. An authentication algorithm is also written into the SIM card; it may differ depending on different operators(A3), session key generation (A8). Algorithms A3 and A8 are closely related; they work in conjunction. Those interested can read, for example, it describes the mechanism of operation clearly and simply.
There are no proven cases of hacking of GSM networks in history; at various hacker conferences, work was demonstrated that, in theory, made it possible to carry out such a hack; in practice, there are many problems that make such techniques impractical. For example, in the city center, a base station can simultaneously serve thousands of devices. It is quite difficult to select from the mix the one that you need to intercept and listen to. Therefore, the intelligence services have always followed other paths. Moreover, the encryption key is contained inside the SIM card and to hack it you need to gain physical access to it.
In yet another revelation, Edward Snowden claims that British intelligence, together with the US NSA, hacked the Gemalto network and received data on SIM card encryption keys for several years. To understand the level of the problem, it is enough to say that Gemalto last year produced and supplied 2 billion SIM cards to the market. In fact, the company's cards are used in the vast majority of phones and other devices in the world.
It's hard for me to imagine how exactly the key leak could have happened, since Gemalto's security procedures are quite convoluted. On the production line where cards are created, the equipment does not have memory to store a series of keys; here you need to physically break in and intercept the data on the fly. Considering that the security system is quite strong, it is difficult to imagine such a scenario. But the company’s network was purposefully broken.

The company has several factories that produce SIM cards, all with a high level of security. Ciphers are created on separate machines internally corporate network, they are created by a special algorithm. For each operator, its own set of keys is created taking into account the wishes and requirements. These keys are then automatically generated and placed in production. A copy of them is recorded on disks and transferred to the operator. No data is stored in Gemalto; if the operator loses his disk, he can safely throw away all SIM cards, they will be useless. Sounds very common sense. But it is alleged that the system was somehow hacked and they were able to collect all the data about SIM cards.
This is potentially a big problem, as it calls into question the very foundation of modern cellular networks. An attacker, knowing the encryption and identification system of a specific SIM card, is theoretically able to intercept and decrypt the signal in real time. Purely in theory. So far, no one has created such equipment, although, perhaps, it already exists somewhere, but this is unknown to the general public. That is, someone received the key to the SIM card and all communications. But another question remains: it is necessary to physically receive a signal from a cell phone, that is, to constantly record the entire broadcast. It is expensive, complicated and of little use in other countries, on foreign territory. Installing a classic bug on your phone is much cheaper and easier. It is a matter of economic feasibility in stealing SIM card data. It seems to me that they did this to have it or as a reserve. In practice, it seems unlikely that such hacking methods will be justified.
For example, in Russia, operators provide all SIM card data to the FSB. Which, in theory, makes it possible to intercept and decipher all signals on the fly. In practice, during all emergencies and terrorist attacks, operators disable the encryption mode so that intelligence agencies can listen to the broadcast. This indirectly indicates that even knowing the encryption of the cards, it is not so easy to receive conversations from them on the fly. It is possible that I am mistaken in this matter and everything is exactly the opposite. Although this is hard to believe.
The theft of SIM card encryption keys is a dangerous bell, as they ensure the security of conversations and are the main barrier to hacking. With this data, attackers receive a master key that can decipher all conversations. But the most important thing is the correlation between the IMSI number and the protection algorithm. I certainly don't like the possibility that someone got hold of all this data. But I repeat, there has not yet been a single proven and confirmed case of hacking of GSM networks. Proven in practice. Rumors, conversations, assumptions, but no facts. Against the backdrop of ongoing leaks that many systems corporate security turned out to be full of holes (remember Sony), this story does not seem impossible. But we as users can only hope that operators will take appropriate measures. The only catch is that if it turns out that the cards are compromised, you will have to physically replace SIM cards around the world. I highly doubt that anyone will do this; these costs amount to billions of dollars, and yet someone must also pay for the production of new SIM cards. Therefore, regardless of the results of the investigation, the replacement will be gradual, and the public will not be nervous. Gemalto promises to make every effort and is conducting its own investigation, but so far they have not seen any security holes. This is a serious crisis for the company, but there is simply no one to replace Gemalto on the scale of our world.
Confidential communication in Russia and abroad
The potential vulnerability of SIM cards has always been taken into account, so military and government officials began to use specially designed Cell phones, which had a separate chip for cryptography and encrypted all conversations and messages. Almost no one supplied such devices to other countries. Cryptography is a product for internal use, and even more so in such devices. Availability similar devices in the wrong hands can potentially lead to vulnerabilities being found in them, this is one of the explanations why they are not found on every corner.
My first acquaintance with a device that encrypted communications took place in the early 2000s; a friend brought me a couple of Sagem phones that he used on Russian networks until strong men in civilian clothes approached him and asked him to explain what he was hiding from his native state. The motivation was extremely simple - you are using prohibited technologies. Then everything worked out, they took away the phones and asked not to do that again.
In 2006, a completely different person decided to do business with Sagem devices, it was already a different model - vectroTEL X8, it was created on the basis of the regular X8.

The cryptomodule was not built into the phone, it was installed in the miniSD memory card slot, you had to enter the PIN code from this card on the screen, and then you could call a person who had the same phone or encryption system. The identification key was 1024-bit, the voice was encrypted with a 128-bit key.
This separate design was due to export restrictions; the cryptographic chip was sold separately. A pair of phones could cost up to $10,000, depending on what keys you bought.
Remember last year's scandal in Germany, when it turned out that Mrs. Merkel was being spied on by her allies and her phone was tapped? Then, secure devices based on Blackberry phones were created for her and senior German officials, but some did not receive them, and others received them with incorrect algorithms. Therefore, Mrs. Merkel could not contact her colleagues via secure communication for more than a week, then the phones were updated, and everything got better. The cost of such a phone is 2,500 euros; the German press reported a figure of 50 purchased devices. This figure shows well the prevalence of such devices and the number of their users. It numbers in the hundreds of people in every country.

In Russia, if you are not higher executive state or a significant figure in industry or politics, it is impossible to get a phone with the latest generation crypto protection. But you can buy several models from telecom operators (the first was MegaFon, then MTS began to provide confidential communications).

Lenovo and laptops that track users
I feel that the topic of security does not want to let us go today, the news seems to be a selection. Lenovo is known for following in Sony's footsteps by packing a ton of unnecessary garbage, there are so many applications that it can be easy to get confused. There are almost no useful ones among them. At one time, Sony came up with a special utility that painlessly removes all this garbage and allows you to enjoy life. The existence of the problem is indirectly recognized by Microsoft; the company launched Signature Edition, this is Windows, which does not have any additional programs third party companies. A site with a corresponding offer from MS.

At Lenovo, between September 2014 and the beginning of 2015, they installed the SuperFish program on their PCs, which intercepts all user traffic, displays advertising from third companies, but most importantly, due to its architecture, has a large security hole. The vulnerability was found by security experts; it is unknown whether anyone took advantage of it in practice or not. But Lenovo quickly began to understand what was happening, and as a result they released a utility to remove this software - it was impossible to simply remove it, an entire utility was needed! You can find it.
It is clear that manufacturers install a bunch of garbage, applications that consumers do not need, and do it for a certain bribe.
This topic resonates well with the campaign of Yandex against Google, which I talked about in Sofa Analytics last week. The FAS accepted the case for consideration and promised to sort it out within two weeks, as a matter of urgency. Apparently, the matter is really so urgent that in Europe they have been considering them for years, but in our country they promised to get it done in two weeks. I would like to be wrong, but everything looks like the outcome is a foregone conclusion.
People who have encountered in the past how Yandex imposes the installation of its products are already joking about what it will be like if the company wins the case and the FAS punishes Google.
I will repeat the main idea - instead of competing with products and creating an attractive solution for users, Yandex took out an administrative club with which they will beat the enemy for being able to become successful. A typical Russian way of solving one’s business problems at a time when it is clear that the game has already been lost. There are two weeks left to wait; it will be interesting to see what Yandex will get in the end and whether his victory will be Pyrrhic.
Do you like it when your brand new phone (regardless of the company) comes with a bunch of pre-installed apps, most of which you don't need and often can't be uninstalled?
Sony reorganization - abandonment of all electronics
Sony company continues to be in a fever, and so much so that its president decided to fight the losses, which the manufacturer has been showing for the seventh year in a row, using very interesting methods. The company will spin off its audio and digital divisions into separate businesses. That is, now only Sony Entertainment (film production and the like), the production of camera modules (since there are two large customers - Apple and Samsung), and Playstation will remain in the big Sony.
Sounds weird? This sounds extremely unusual to me. Desperate to make a profit, Sony is separating unprofitable areas into separate companies and, apparently, will try to sell them, as they did with VAIO laptops. This is a very, very dangerous trend that could leave us in the future both without smartphones and without company tablets. I don’t know about you, but I’m tired of losing market players who leave one after another into great nothingness, leaving in their place the Chinese, who often have not yet gained sufficient experience. And this is very confusing, since Sony has always had the charisma of two or three manufacturers, as well as design, which pleases.

Although here, of course, everyone chooses something for themselves, I have always been impressed by Sony Style, and if it weren’t for the technical problems, I would have used their devices with pleasure. Moreover, it seems to me that this is Sony’s karma with phones. Let me remind you that the roots of this division lie in Ericsson. The company was losing money in the 90s, but pulled itself together and released the Ericsson T68m, which became iconic, like many subsequent models. But by that time, Ericsson had already had enough of problems, did not believe in the future, and organized a joint venture with Sony. Then they pushed a problematic company onto Sony, since at some point it began to lose the market. Now there is a feeling that Sony can play normally in the market again; they have resolved many small and large issues. Yes, they do not fall into their own sales forecasts. Yes, the market situation is extremely difficult for them. Yes, there is a loss in the mid-range and budget segments. But there is also a chance that with proper management, Sony devices will sell better. And not just chances, but huge prospects. The company despaired of conquering its main markets - America, India and China. And this is bad, because it deprives Sony of its future. But the more interesting the task. The company clearly lacks young and ambitious managers, because they are already by and large, nothing to lose. This means that you can only grow upward, experiment and surprise. Fingers crossed, I really hope that such people will come to Sony and we will not discuss the company’s final departure into oblivion.
There is no room left in the issue for other topics that I outlined in advance, so we’ll talk about them this week or next Monday. For some holiday entertainment, I suggest watching short review 3D pens, which can be quite interesting entertainment for adults and children.
P.S. Happy holiday! Have a good mood, kind and smiling people around you. The next issue will already be released from Barcelona, as well as several subsequent ones. A week until the main announcements of this year, the countdown has begun.
About the bill, which was supposed to prohibit officials from using uncertified mobile devices, since, according to the author of the bill, they pose a threat to national security. Still would! If the American intelligence services knew what our deputies were talking about, then they would understand that they would never defeat our country! After all, if we somehow develop with like this elected, then what will happen to us if adequate people come to the State Duma?..
Last time I reviewed various alternatives iPhones, but they all have one thing in common - we need to give up the usual phone and switch to new device or carry a second one with you, especially for confidential negotiations. Is it convenient? Of course not. That’s why, at the very end of the last post, I suggested that no one would voluntarily give up their Vertu and iPhones. And then the other day journalists asked me a question - have I heard about Russian headsets for mobile devices that encrypt voice traffic starting immediately from the headset?.. I didn’t hear it, but I started digging. Actually, brief results of my digging (without claims to completeness).
So, if we discard the option of ensuring confidentiality on the phone itself (too much dependence on the version of the mobile OS and platform) and using a special telephone device (inconvenient), then we are left with two options for solving the problem:
- encrypt in the headset itself
- encrypt in the “layer”, an intermediate crypto-module between the headset and the phone.
Journalists also told me about the first option, mentioning Ruselectronics, which should flood Russian market specialized headsets with built-in encryption. But no matter how I searched, I never found a company that was already producing such devices. I thought that this might be the Tula OKB "Oktava", which specializes in producing headsets for security forces, special services, the Ministry of Emergency Situations, etc., but I didn’t find anything related to cryptography from them. There was also a statement from Ruselectronics about the release of cryptomodules for YotaPhone, but it has little to do with headsets - it clearly depends on the platform of the device.
Basically, modern headsets, such as Plantronics or Jabra, encrypt the voice from the microphone to the computer (or other device to which the headset is connected) using the 128-bit E0 algorithm, which is part of Bluetooth protocol. But this option does not protect the voice connection from subscriber to subscriber. It's more of a protection solution. wireless connection from the headset to the computer or phone, between which there can be up to 100-120 meters. It is logical to assume that such a channel in an unprotected version is easily eavesdropped and therefore requires protection.
I didn’t find any more cryptographic information protection built into headsets. But I found several implementations of the second solution I mentioned. For example, TopSec Mobile from Rode-Schwarz.
This is a hardware device that does not depend on the model of phone or computer to which it is connected. Negotiations are conducted either through the TopSec Mobile itself, brought to the mouth during a conversation, or through a headset connected to the cryptomodule. The only disadvantage of this approach is the presence of a dedicated call control server between subscribers registered on the server. But this necessary condition construction distributed systems interactions.

The second device I found was the “GUARD Bluetooth” scrambler from the domestic company LOGOS. Original Soviet device. There is no design as such. The headset is tightly “sewn” into the device and can only be replaced together with the device. But the protection of conversations is guaranteed - the device connects via Bluetooth to a transmitter - a computer or phone (not a word is said about protecting the Bluetooth channel using E0). I haven’t tested the device, but you can find a review of it online. The appearance of "GUARD Bluetooth" in comparison with the same TopSec Mobile gives a very good idea of how domestic and Western cryptographic information protection systems (and according to appearance, both in terms of ease of use and functionality). But this device does not require any external server to operate - point-to-point operation is possible.

The last solution I'd like to look at is IndependenceKey, which aims to protect various types of interactions between users. Protected types of communication include: Voice connection. However this device is a kind of intermediate option between an independent crypto module and security software. In particular, a headset is connected to the IndependenceKey module, from which the voice is transmitted, encrypted in the module, but then it goes to the software installed on the personal computer, where the IndependenceKey is inserted into the USB connector. Connecting it to your phone will be problematic.

These are the solutions. True, none of them are certified, and it is unlikely that they will be. Maybe Ruselectronics will please you with something interesting in the near future?..