What I knew before about the "dark Internet" - well, that this is such a hidden segment of the network, in which no less dark personalities sell, buy and show everything for which on the regular Internet has long been criminalized. Drugs, weapons, fake passports, and everything off the radar of any regulatory agency, just like on the planet Tatooine. Quite enough to spark the desire to explore this hot spot.
Dark internet
Segment of the deep Internet (deep web), not indexed by search engines and sites inaccessible through standard browsers.
The most popular way to get there is Tor (The Onion Router), an onion router that pushes data through many of its own servers and thus covers all traces of users. The service was developed for the US Navy in 2004 and became a Pandora's box: its decentralization precludes the possibility of simply "turning off" the system.
We need to start with the main thing - for me, the Internet and technology have always been just tools for the transfer of content. Their filling and some non-obvious possibilities interested me no more than those of an iron or a juicer. VPN, Tor, IP2P, proxy - I learned all these magic words from social and political publications, not geek publications. The first ones dispersed a wave of interest in the topic a year or two ago, when Roskomnadzor had just begun to form a serious censorship body. Instructions on bypassing blockages, which the department actively imposed on interesting or politically objectionable resources, became relevant. Then the choice settled on ZenMate, only in order to enter the fenced, it seems, according to Alina Kabaeva's statement, "Luch". It turned out that when enabled, this thing significantly slows down the connection, and the culture hacker magazine predictably slowed down the pace of work, so I soon stopped turning on the plugin icon hanging in the upper right corner.
So, with the dark internet, it's even worse. Anonymity and security require sacrifice, so surfing in the Tor browser of my choice for the tour instantly revived payment cards with ladybugs from the days of pre-broadband Internet in my memory. The feeling is enhanced by the finished design of most "dark" sites - something like the web looked like on the monitors of the heroes of "Hackers" or "The X-Files". But this only adds charm to the process, we came here for content, not comfort.
First of all, the hand reaches for the forbidden fruit - here they are, the legendary drag markets Silk Road, Pandora, Agora. Everything there is exactly as you expect and at the same time you are afraid to see - right here with prices, descriptions, photographs, reviews of happy buyers
Internet structure
ORDINARY Internet
Vkontakte, FURFUR, Buzzfeed and everything else that we are used to constantly using.
"Underwater" Internet
Imageboards, FTP servers, marginal sites with naked teens, and other hobby clubs that fall outside the boundaries of ordinary people.
Proxies required
Deep internet
Websites blocked by censorship organizations, hacker forums, legally questionable content.
Tor or alternative systems required
Dark internet
Trade in drugs, weapons, documents and people, exchange of secret or dangerous documents, prohibited books.
THE CLOSED Internet (the existence of which is reasonably doubtful)
Secret government experiment reports, snuff, hitman services.
You can forget about search engines right away. At least about the special ones designed for dark web searches. There are not one or two of them, but using them is a real torment, there is no question of any relevance and effectiveness. It's easier to go straight to existing lists of links - for example, Hidden Wiki or TORDIR. Lurkmor also has its own version for beginners, but it's too small - it's not interesting.
First of all, the hand reaches for the forbidden fruit: here they are, the legendary drag markets Silk Road, Pandora, Agora - the list goes on for a very long time. Everything there is exactly as you expect and at the same time you are afraid to see - right with prices, descriptions, photographs, reviews of happy buyers. Most reminiscent of old Ebay or a forum for Japanese denim aficionados before the rise of popular specialty stores. The variety is striking - you feel like a Soviet person on a Baltic business trip, not otherwise. It's hard to believe that everything is that simple. "Is it generally legal?" But enough: firstly, it is illegal, and secondly - after the third studied market, it becomes boring, almost like with sneakers.
Why won't the valiant drug cops close all these shops? “That's why this doesn't happen in the real world,” says Dmitry Khomak, one of the founders of Lurkmore. - The district police officer usually knows where in the area under his account everything interesting is happening, but he does not break in there with the operatives and riot police. And the point is not corruption, but the fact that it is more profitable to keep small traders in forbidden goods on a short leash, and wait until someone big comes. Although there is always a chance to run into some kind of "Black Network" police operation. "
What's next on the list? Pornography, of course. Not that it is very lacking on the regular Internet, but it's still “dark”, “deep” - here you certainly won't have to look for something perverse for a long time. But no. Bloody torus search engines show links to the local Pirate Bay on the first few dozen pages of the query. Okay, let's dive into the link library and look for the code tags in the description. And here is the terrible truth - there are not so many of them at all, even much less than all kinds of illegal commercial services. The most extreme I came across is a porn tube resource entirely dedicated to coprophilia and related areas of the erotic. Even greasy pedophiles, who supposedly have taken a liking to the darknet, and they do not really advertise themselves. Unless on local imageboards, unlike in Russia and Asian countries, the loli section is not prohibited. There were also several portals for lovers of young boys, but, again, limited to hand-drawn content. For this, even Milonov Tor is too lazy to install.
The most extreme I stumbled upon is a porn tube resource entirely dedicated to coprophilia and related areas of erotic




Limits of anonymity

On the other hand, Pink Meth, which has long been closed on the surface, thrives on the deep network - a platform on which users post intimate photos of their exes, which is already there, partners, invariably accompanying the "drain" with screenshots and the address of the page on facebook. In general, it is impossible not to note a sufficiently high concentration of asocial types on the darknet. Popular Russian-language forums are packed with discussions of alternative types of earnings: blackmail with intimate photographs, fraud on social networks under the guise of a psychic or a prostitute. On another thread, they are discussing the possibility of purchasing a grenade launcher by mail, almost in case of a zombie apocalypse. Against the background of such threads, users who come in to buy prohibited substances look like stupid tourists in an oriental bazaar.
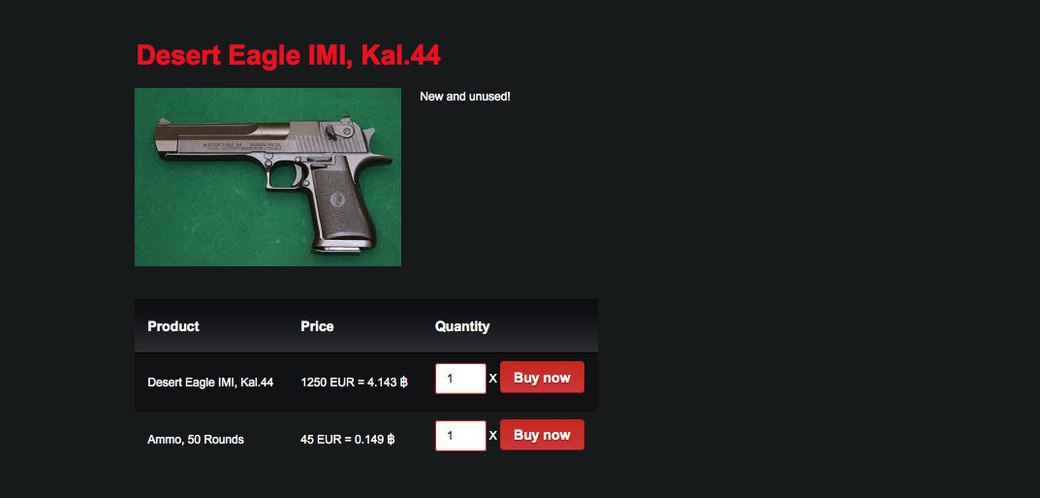
What else can be purchased in the .onion domain zone? Not much, but everything an action hero needs: firearms of all stripes (some shops chastely ban only "weapons of mass destruction"), passports, driver's licenses, credit cards, counterfeit bills, gold bars and iPhones. They say you can still buy killers, slaves or human organs. Have not found. But I found a couple of excellent trackers, one of them specializes in Mondo films and shock documentaries, from which, even if you are not a big fan of dead bodies, you can select something interesting. Others simply store content without any problems, which copyright holders mercilessly clean up on the regular network.
Systematically finishing off links from a catalog that seemed at first huge, out of curiosity I came across only a couple of high-quality libraries, several postcard sites with dubstep and eight-bit animation, and a certain number of radical portals like Kavkaz Center or CyberBerkut. There are also havens of anarchists (many) of all stripes and neo-Nazis (not so many), filled with tons of thematic content with loving care. The platform for the exchange of hot information between journalists, opposition politicians and other interested parties seems to be the most advanced and adjusted to modern design standards. This is understandable: the process is organized there seriously, the site administration takes 20% commission from each transaction.
Popular Russian-language forums are crammed with discussions of alternative types of earnings: blackmail with intimate photos, fraud on social networks under the guise of a psychic or individual prostitute




All financial transactions in the Tor universe are carried out using BitCoin. Decentralized cryptocurrency is the only reasonable monetary equivalent for buying prohibited products.
The Ministry of Finance of the Russian Federation recently published a bill according to which the use of cryptocurrencies will be punishable by fines of up to 50 thousand rubles for individuals and up to 1 million rubles for legal entities. Users of darknet forums are sure that there is no question of any effective fight against cryptocurrencies in Russia: the relevant departments of the Ministry of Internal Affairs simply do not have enough competence.
Everything turned out to be approximately the same as they had been warned: there is almost nothing to do on the dark Internet without special consumer intentions. Super-secret documents and reports of experiments on people, apparently, still lie on the next, deeper level, but the "Anarchist Cookbook" is not difficult to find "on the surface." In the process of dating, it turns out that there are a huge number of extreme sites, for which you also do not need to turn on the Tor browser at all. The illusion of absolute, arcade freedom, of course, fascinates, but the spell wears off as soon as you realize that you, in general, do not need a fake British driver's license.
Will the young and free go to the dark internet to avoid the undue attention of the increasingly active network oversight bodies? Unlikely. For this, according to Homak, a cataclysm must occur, which will make the regular Internet completely unsuitable for communication. Even the romantic craving for complete digital anonymity can hardly replace the convenience of multi-million dollar services and media that suck personal data from their users. Tor is not required to read news, even those uncontrolled by anyone's censorship, and the pages of 99% of social network users, it is bitter to admit, do not actually contain anything interesting. And, in the end, well, not all of us are destined to become heroes of an action movie.
How much do you know about the internet? And how much does the Internet know about you?
What is deep web
The Deep Web is a shadow Internet, which is based on maximum anonymity, a complete rejection of provider servers, which makes it impossible to determine who, where and what is sending. Before you get to any site via the deep web, your data is encrypted and transmitted through the same network participants as you, which makes the transfer of data as anonymous as possible, but rather slow. The Deep Web now resembles the speed of the first Internet using dialup modems. The concept of the Deep Web has gained popularity quite recently and still does not have a clear meaning. In a broad sense, this phrase denotes information hidden from indexing by search engines, and includes closed communities and forums, certain pages of sites are prohibited from indexing, databases, as well as encrypted networks for anonymous surfing (the latter most often mean TOR and i2p). In a narrower sense, the Deep Internet is a pseudo-domain space created using encrypted connections that ensure user anonymity by hiding the IP address given to him by the provider.
Usually, interest in the deep Internet is associated with the desire of more or less experienced users to find something secret on the Internet, hidden from the eyes of the majority. Novice internet stalkers are sure that the deep internet includes a lot of interesting information, which, only by misunderstanding, turned out to be hidden from the eyes of the majority. In fact, this opinion is only partially true, and the so-called Deep Web includes both information that is not needed by the majority of law-abiding citizens (the vast majority of TOR and i2p network sites), and very interesting discussions and opinions of people united in a closed community. to isolate themselves from people with alien views and opinions or inexperienced newcomers to their field of activity (a typical example is closed SMO or SEO forums). In addition, the closed nature of some communities makes them elite in the eyes of other users (a vivid example is the closed collective blog Leprosorium).
Scale
The size of the deep web is unknown. There are relatively reliable estimates of the total number of sites leading to online databases: about 600 thousand of such sites on the entire Internet and about 30 thousand on the Runet. The most interesting thing is that the amount of information concentrated in the deep web is tens of times greater than the amount of information in the ordinary Internet space.
Below are some links to interesting (in my opinion resources)
Https://onion.cab/ - Tor search engine and gateway to the Internet.
http://www.deepweb.us/ - M. Zillman's collection of deep web resources.
https://www.wilsoncenter.org/sites/default/files/stip_dark_web.pdf - Study material with verified clickable links to Deep and Dark Web search resources.
https://www.deepdyve.com/ is a paid deep web search engine.
http://www.hozint.com/ is a platform for collecting information about political stability, security of countries, various incidents and unrest, collecting and scanning information on the deep web.
http://www.gwu.edu/~nsarchiv/search.html - US National Security Archive at George Washington University.
http://www.base-search.net/ is an invisible web search engine for open academic web resources belonging to top universities and research centers in the US and UK.
http://citeseer.ist.psu.edu/index - an invisible web search engine for various publications, books, articles in the field of computer solutions and information sciences in English.
http://www.findthatfile.com/ - The most comprehensive file search on the Internet. Allows you to search for files in 47 formats. The search can be carried out by the author of the file, its name, a fragment of the content. Supports not only basic types of text and table files, but also compressed files, audio-video files and much more.
Http://www.deepwebtech.com/ is a leading provider of "deep web technologies" that implement a federated search approach, creator of a number of deep web search engines, Internet and intranet solutions.
http://www.ipl.org/ is a search engine for collections containing the most relevant and interesting information resources created as a result of the voluntary joining of efforts of thousands of students, volunteers of information cataloging and classification and leading specialists in the field of information technology.
http://publicrecords.searchsystems.net/ - Search over 50,000 of the largest open source databases for free. For example, it can provide information about business applications, available licenses, and even about participation in criminal proceedings, bankruptcies and many, many other interesting things.
http://www.resourceshelf.com/ - is a collection of the most in-demand business and scientific issues supported by a community of researchers and specialists in collecting and cataloging information.
http://vlib.org/ - the world's largest virtual library uniting digital resources from many countries, training centers, commercial organizations, etc.
http://biznar.com/biznar/ is the most advanced federated deep web search engine for business.
http://lookahead.surfwax.com/index-2011.html - The first real-time deep web search engine with elements of semantic analysis. Allows you to grasp news and facts inaccessible to other systems. It integrates into browsers.
http://infomine.ucr.edu/ - a virtual library of Internet resources, contains data from libraries of many of the richest and most successful American universities.
Not of course many sites inaccessible on the regular network, such as WikiLeaks, Piratebay, The Hidden Wiki and a bunch of other sites, as they say: everyone has ...
How and who is using the Deep Web?
Tor users use this network by connecting through a series of virtual tunnels rather than direct connections, thus allowing organizations and individuals to exchange information over public networks without revealing their privacy. Tor is effective in circumventing Internet censorship by allowing users to browse sites that would be prohibited on the regular Internet.
Criminals of all stripes, terrorists, drug dealers, hired killers feel at ease in these open spaces, although from time to time information leaks into the media.
Tor can also be used by software developers to create new and improve old communication tools with built-in privacy protection.
Hidden services allow individuals to create websites without revealing the webmaster's IP address and true location. For example, Tor is used to discuss socially problematic topics: chat rooms and web forums are formed for victims of domestic violence or people with certain diseases.
Journalists can freely and safely correspond with dissidents and denunciators of the regime. Employees of nongovernmental organizations (NGOs) gain access to correspondence with families when they are out of their country without revealing to the general public that they are working with the organization.
It is clear that such a place cannot be bypassed by the military, special services, law enforcement officers to ensure the secrecy of their messages and tasks. They also use the Deep Web when searching for terrorists, other criminal elements and their illegal actions.
What currency is used in the Deep Web
Bitcoin is a commonly used currency in the deep web of black markets, and they do not exist in physical form, but computers, and sometimes entire computing centers, are used to acquire them.
What distinguishes bitcoins from conventional currencies is that it is unrealistic to trace their owners and the chain of transactions, which makes them the most preferred form of settlement for illegal transactions.
Most likely, this space in the near future will be under the control of supervisory authorities, but time does not stand still and we should certainly expect the emergence of new programs and browsers, since the secret Internet allows you to cash out huge amounts of money.
P. S. this is my first post, if anything - sorry ...
What is the Dark Web or Darknet, how does it differ from the Deep Web, and why are these two terms always confused? We decided to help you figure it out and at the same time warn you - after all, the Darknet, with all its attractiveness, accessibility and alluring spirit of freedom and permissiveness, is a very dangerous place, wandering around which can cost you quite a lot (both literally and figuratively).
What is the Dark Web?
The Dark Web is a term referring to a certain group of specific websites that exist in the encrypted network space. They cannot be found by traditional search engines and cannot be reached using traditional browsers. It is also often owned by the Dark Net, but don't confuse it with the Dark Internet (we'll talk about it below)
Almost all Dark Web or Dark Web sites hide personal information using Tor encryption tools. This network (and did you know, by the way, that it is an acronym for The Onion Router - "onion router"?) May be familiar to you due to its ability to hide user identity and network activity. You can use Tor to hide your location in a way that makes it appear that you are logged in from a different country than where you are. This is very similar to how VPN services do it.
.png)
If a website is running through Tor, it has about the same effect, and even multiplies it. Sites designated as the Tor Hidden Service are only accessible when connected to the Tor network. Simply put, without connecting to this network, you will receive nothing.
The pseudo-suffix "Hidden Services. onion does not work with DNS servers, and Hidden Services URLs are an alphanumeric set of 16 characters automatically generated using the public encryption key when the site is created. You can copy the Tor link and try to open it in a regular browser, but this will lead you to a dead end.
To visit a Dark Web site using Tor encryption, the Internet user will have to use Tor themselves. Just like an end user's IP address bounces through multiple layers of encryption to get to another IP address on the Tor network, so is the case with Internet sites. Each of the nodes knows only those nodes that are connected to it directly (it does not know anything about the ways of connecting your PC to the web server). Any transition from one node to another is done using its own set of encryption keys. This reduces performance and speed, but significantly increases the security of your anonymous movements.
There are several levels of secrecy, even more than the already secret fact that you use Tor to visit a regular Internet site itself.
What follows from this? That anyone can visit the Darknet sites, but it is extremely difficult to figure out what kind of people are behind them. But it can get dangerous - in certain cases.
Silk road to oblivion and others
But not all Dark Web sites use Tor encryption. Some people use similar services like I2P or Silk Road Reloaded. The visitor will have to use the same decryption method that is used on the visited site, and - which is critical - know exactly how to find this site, up to manually entering a link just to enter this site.
Notorious examples of Darknet sites include the Silk Road (which translates to "Silk Road") and its derivatives. Silk Road was (and may still be) a site for the purchase and sale of drugs "for entertainment purposes" - for those who want to unwind from time to time illegally. This is one example of the Darkweb being used for disgusting purposes.
.jpg)
The Darknet made massive headlines in August 2015 after it was revealed that 10 GB of information stolen from Ashley Madison, a site designed to make bored spouses conveniently cheat on their partners, was posted on the vastness of the Dark Web.
The hackers who stole the data threatened to spread it all over the internet if the site didn't shut down, and it has operated under that threat ever since. Now the spouses of Ashley Madison subscribers have begun to receive blackmail letters demanding the transfer of $ 2,500 in bitcoins - or all personal data will be made public.
In March 2015, the British government established a dedicated cybercrime unit on the Dark Web with a focus on organized crime and child pornography. The National Crime Agency (NCA) and the British intelligence unit GCHQ have jointly created the Joint Operations Section (JOC) for this purpose.
But there are still quite acceptable reasons for using the Darknet. We're talking about freedom of information.
The population of closed countries with a totalitarian system sometimes only through the Dark Web can communicate with the outside world. And the recent revelations of the surveillance of the Internet activity of their citizens and you by the American and British government special services may give you a sound idea of transferring your network communication to the Darknet. (I'll stay on Facebook, but I just like the outside attention.)
What is the Deep Web?
While these terms - Deep Web and Dark Web - are often used interchangeably, they are by no means the same. There is some nuance here. The Deep Web refers to all sites that cannot be found by search engines.
Thus, the deep web includes not only the Dark Web, but all user databases, post pages, abandoned sites and personal pages, online forums with required registration, and paid online content. There are a lot of such pages, and most of them exist for the most common reasons.
For example, as an online publication, we have “mock” versions of all of our web pages blocked from indexing by search engines so that we can check the content and design of the publication before releasing it to the public. Therefore, every page available for public viewing on this Internet site (and literally millions of similar pages and sites) has a duplicate in the deep web.
The content management system in which I am preparing this article is also located in the deep web. Here's another hidden take for every page on the public site. At the same time, our working corporate network is also closed from search engines and protected by a password. And since all this has existed for about 20 years, our network has grown pretty much with secret duplicates.
Are you using online access to your bank account? Your password-protected data is somewhere deep in the deep web. And if you estimate how many pages a Gmail account alone generates, then the true size of the deep web will become at least approximately clear.
This is why newspapers and popular news sources regularly return to the "90% of the Internet" horror stories of the "dark web". They simply confuse the massively risky and unkind Dark Web with the vastly larger but mostly harmless ocean of the Deep Web.
At the same time equalizing with each other and such actions as deliberate concealment of activities from the law and normal fencing from the access of search engines for the sake of confidentiality or simply for banal business purposes.
What is the Dark Internet?
Even more confusing is the term "Dark Internet", sometimes used to describe the following examples of networks, databases, or even websites that cannot be found on the open Internet. In this case, this happens either for technical reasons, or because they contain some kind of private information not for public use.
The main practical difference is that the terms Dark Web or Deep Web are usually used by newsmen to refer to corners of the web full of dangers and someone's hidden agenda, while the "dark Internet" is just boring warehouses where scientists store raw data. for their further research.
But, of course, you are interested in how to get into the Darknet
Technically, it's not particularly difficult. You just need to install and run Tor. Download the Tor Browser Bundle from www.torproject.org - all the tools you need are already there. Open the downloaded archive, select the location on your hard drive for the files after unpacking, then open the folder and run the Start Tor Browser file. That, in fact, is all.
The Vidalia dashboard will automatically connect to the mysterious encrypted network and, once connected, will open a browser. To disconnect from the Tor network, you just need to close this browser.
.png)
Depending on what you intend to do, some conspiracy theorists advise you to tape up your laptop's webcam in order to prevent the overly curious and tech-savvy "big brother" from spying on you. In this case, we can recommend wearing a foil hat at the same time.
The hardest part is figuring out where, what and how to search on the Darknet. Here, reader, we will leave you and wish you good luck and a safe search. And one more warning before you go even one step further: by entering the Dark Web, you will have a real opportunity to get to all those sites that the tabloids use to scare us. This means that right now you may be a couple of clicks away from places offering drugs, weapons and - frankly - even worse.
Aggregators like the Reddit site offer long lists of links, as do some pages on the Wiki - a list offering access to some really dirty places. If you wish, you can briefly familiarize yourself with them, however, we would not recommend that you do this.
Also keep in mind: Darknet sites crash from time to time - such is their dark nature. And if good customer support is important to you - stay out of the dark and closer to the light!
And again: take our warning carefully: this article is not an attempt to either inspire or endorse your further, possibly illegal or immoral behavior.
Panda Security in Russia and the CIS"" (Or "The Invisible Internet") is on the rise. People are curious by nature, and therefore more and more Internet users are going to his "dark side". Everyone knows that the Internet is a never-ending source of information, and search engines like Google, Yahoo and Bing can quench our thirst for information with just a few keywords, resulting in huge lists of information in seconds. But did you know that most of us have access to only 4% of the World Wide Web?
We only know the tip of the iceberg: the structure of the "shadow Internet"
As we said above, in order to better understand the "shadow Internet", it is necessary to imagine the entire Internet as an iceberg, which is divided into five parts, each of which is even more submerged than the previous one.
Level 1... At the tip of the iceberg, we will find all the pages that we can access using search engines. This part of the Internet is visible and accessible to "mere mortals", and the information on it is fully traceable.
Level 2... Just below the surface of the water, we will find those pages or sites that are not indexed (in other words, sites that are not visible in search engines) by traditional search engines (like Google or Yahoo). Thus, they are only available to those who are "in the know" of these sites.
Level 3... If we plunge even deeper into the cold water, the iceberg surrounding us, then we can see information (mostly illegal), which is very difficult to find "openly".
Level 4... As we get closer to the lowest point of the iceberg, we will be able to find any type of illegal site. Most of them are monitored by the US government (for example, child pornography websites).
Level 5... After traversing four levels of the "shadow Internet", we will be able to reach the lowest point of our iceberg - the most hidden part of the Internet, known as the "dark side of the Net" (The Dark Net). A haven for hackers, this part of the web is based on a collection of private networks that can only be accessed by "trusted" users. This is the darkest side of the Internet: it does not obey standard protocols and it is insecure.
Tor: How to Access the Shadow Internet
Each of us can access the "shadow" parts of the World Wide Web, but for this you must use alternative search engines. Tor (The Onion Router) is a free program that was developed at the US Naval Research Laboratory in the mid-90s to protect the online communications of the US intelligence services.
Tor has a layered structure (hence its name) that allows a user to navigate the network from one level to another, while the user is protected by a cipher that hides their IP address. One of the main distinguishing features of the "shadow Internet" is the user's anonymity.

Is it really possible to browse the web anonymously?
Industry experts say connecting over Tor can be risky. Tor does not allow the user to control the proxy to which he connects, as a result of which he can face man-in-the-middle attacks and JavaScript infections that violate the user's privacy.

Hearing about the mythical Deep or Dark Internet, the user immediately wonders how to get there, how to enter a site that is not available to ordinary Internet users. If you are also tormented by such curiosity, then this article should help you.
What is the Dark or Deep Internet
First, you need to briefly understand what the Deep Internet is and what the Dark Internet is. There is a lot of confusion with these terms, but to speak in simple terms, these two names mean the same thing, namely the hidden part of the World Wide Web.
Different parts of this Deep Internet operate on different principles. Sometimes these are just sites that are not indexed by search engines and therefore only accessible via a direct link. Sometimes these are sites for access to which you need to know the password. And in some cases, these are sites operating in the TOR network.
In this article, we will tell you how to get into this part of the Dark Internet, which works on the basis of the TOR network. The TOR network is a computer network that runs on top of the regular Internet and uses the principle of onion routing. All information on the TOR network is encrypted and transmitted through several intermediate servers in order to make it more difficult to track the location and identity of the user.
Resources in the TOR network have their own top-level domain - ONION. Of course, this domain is not officially registered anywhere, but this does not prevent its use if the software for working with the TOR network is installed on the computer. Thanks to this domain, it is very easy to distinguish links to regular websites on the regular Internet from links to Dark Internet resources on the TOR network.
How to get to the Deep or Dark Internet
From the outside it may seem that in order to get into the Deep Internet you need to be a hacker and have some significant knowledge in the field of computer networks. In fact, everything is much simpler. All you need to enter the Dark Internet is a special browser called TOR Browser. Well, you will also need access to the regular Internet, but I think this is understandable.
So, we take the first step to enter the Deep Internet - download the TOR Browser. To do this, go to the site, click on the "Download" button and download the installation EXE file to your computer.
Next, run the downloaded EXE file and install the TOR Browser on your computer. The installation process for this browser is no different from installing other programs, so this should not cause any problems. Just select the Russian language, select the folder for installation and wait until the TOR Browser is installed on your computer.

After installation, launch the TOR Browser and click "Connect" in the window that appears. This will connect you to the TOR network with standard settings. This connection option is suitable for most cases. But, if there are problems with the usual connection, then you can click on the "Configure" button and change the standard connection settings. You can read more about this in our article "".

After connecting to the TOR network, a message "Congratulations" or "Welcome" should appear in the TOR browser. This means that everything is working and you can enter the Deep Internet.

Now, in order to get into the Dark Internet, we enter the site "thehiddenwiki.org" into the address bar of the TOP browser and go to it.

After loading thehiddenwiki.org site, you will see a list of links to popular resources on the Deep Internet. Go to any resource and you are already on the Deep Internet. As it was written at the beginning of the article, you can distinguish links to resources of the Deep Internet from regular links by the first-level domain. All site addresses on the Deep Internet end in ONION.

It should be noted that some of the links to the resources of the Dark Internet may not open. This is quite normal, don't be surprised. This is no ordinary Internet for you, not everything here works as smoothly as you are used to.



