How to monitor employees, monitor children or monitor a person at a computer?
It is difficult to imagine the everyday life of a modern person without the use of a computer or mobile devices connected to the global network and used daily to receive and process information for personal and business purposes. Computers have become a part of the lives of not only adults, but also teenagers and children who spend several hours on the Internet every day.
Modern schoolchildren from the first grades learn to use computer technologies and actively use them for educational and entertainment purposes. Unfortunately, the Internet is flooded not only with workshops on solving problems in physics or mathematics, which do not pose a threat to the fragile child’s psyche. The global network contains countless unsafe websites, including extremist, sectarian and adult sites, which can cause serious harm to the normal development of a child as an individual and lead to problems in the future. Agree, you would not want your child to study occult rituals or view pages of dubious content instead of doing homework after school.
Due to the above, many parents may have a very reasonable question: “How to protect a child from the harmful influence of the Internet?”, “How to find out what a child does in his free time at the computer?”, “Who does your beloved child communicate with?”, “ How to organize supervision of children?».
There are a lot of programs for monitoring computer activity and spyware, but, as a rule, they are all paid, reduce the performance of the computer and are easily detected even by inexperienced users. In reality, you will only be able to view the contents of log files with data entered on the keyboard and, in some cases, screenshots. In addition, you can view these log files only on the computer where these files were created. Those. if you are in a remote location, you will not be able to view these files. Of course, you can set up automatic sending of these logs to your email or server, but this involves additional difficulties and waste of time. Besides, it's just inconvenient.
For full control over children, it can be very convenient to use programs for remote access to a computer via the Internet. Some of these programs are very easy to set up, or to be more precise, they practically do not require it and are able to instantly establish a connection with any computer connected to the Internet.
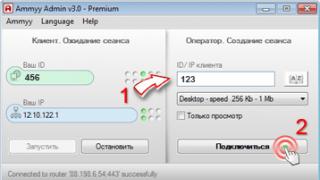
One such program is Ammyy Admin. And despite the fact that the main application area of the program is the provision of remote technical support, the features and versatility of Ammyy Admin make it easy to use it as a means of remote monitoring of children. When it comes to business, monitoring and control of employees is also one of the areas of application of the program.
Why should you use Ammyy Admin for remote control of children?
- You can connect to any PC in a few seconds.
- You can view the image of the remote computer from any other computer connected to the Internet. No tedious settings, registrations or installations!
- Ammyy Admin bypasses all known firewalls and antiviruses (which cannot be said about keylogger programs) and does not require installation. With the correct settings, it will be practically impossible to detect Ammyy Admin.
- Your child will never realize that someone is watching him in real time.
- You can interactively enable voice chat and listen to what is happening on the remote PC side.
- Ammyy Admin is completely free for home use, provided that you have not exceeded the usage limit of the free version.
How to set up child monitoring using Ammyy Admin?
So, the procedure for setting up the program is extremely simple and will not take more than a minute.
What to do on the remote computer that we will monitor:
What to do on the computer from which we are monitoring:

If you want to organize employee control by monitoring their work computers, then the laws of some countries require you to warn them about this. In any case, it will be useful to do this, because... Knowing that the computer is under surveillance, the employee will not engage in extraneous activities on the work computer, which will reduce the risk of infecting the computer with viruses and leaking confidential information, and will also increase useful working time.
Have you ever felt worried about the safety of confidential data on your computer? Do not rush to answer that you do not have confidential information. If you think that there is “nothing to steal” from you, you are most likely mistaken. If you have made a purchase at least once in an online store, paying with a credit card or electronic money, then your computer is already bait for a potential thief. The problem exists, and an ideal solution for it has not yet been invented. Of course, there are various ways to protect confidential data, for example, restricting access rights in the system, anti-virus software, firewalls, etc. We have repeatedly talked about many of them on the pages of 3dnews. However, relying entirely on an antivirus and a password protection system would be somewhat presumptuous. In addition to the danger of a virus attack, there is a threat of a completely different kind, caused by the human factor. What happens when you are away from work? Perhaps, while you are finishing your cup of coffee at the cafeteria during your lunch break at work, someone is reading your email correspondence?
Having got someone else's computer at his disposal, even for a few minutes, an experienced user can easily find out all the information he is interested in - the history of negotiations via ICQ and e-mail, a list of passwords used in the system, links to resources that the user viewed, not to mention access to documents on disk. Utilities that help spy will be discussed in this review. Such programs can be used both at work to control the working time of employees, and at home as a means of parental control or as a tool for obtaining information about the personal life of your spouse. Note that due to the specific nature of spyware, antiviruses and firewalls are often very suspicious of them, often mistaking them for malware. The developers of some utilities even place a corresponding notice on their websites. However, in most cases, it is enough to configure the firewall once, and it will no longer respond to spyware.
Power Spy 2009
Developer: eMatrixSoftDistribution size: 5 MB
Spreading: shareware Power Spy can be called a universal spy. It is suitable for monitoring employee workplaces, monitoring your child’s activities on the computer, and finding out what your wife is doing on her home PC in your absence. The program can record all keystrokes, save screenshots of windows opened by the user, record the addresses of visited websites, intercept messages sent by e-mail, as well as through instant messaging systems (MSN Messenger, Windows Live Messenger, ICQ, AOL Messenger, AIM, Yahoo !Messenger, Windows Messenger and Skype text chat). In addition, it is possible to save all windows opened by the user, applications launched, passwords typed and information entered into the clipboard.
In hidden mode, Power Spy is completely invisible to the user, it does not appear in the list of running applications, does not show an icon in the system tray, it is not in the list of installed programs and in the Start menu, and in addition, the folder in which Power Spy was installed , is also hidden. To interrupt the program or uninstall it, you need to enter a password, and you can delete the program using its window. The administrator can open the program window with the collected data by pressing a specific key combination. Information about computer activity is presented in a convenient form: screenshots can be viewed in slide show mode, information about keystrokes is organized chronologically by application and window, and the Email tab displays the text of all emails that the user has read and sent. In addition, the program saves the contents of all documents that users have worked with. Moreover, if the file was opened several times, then Power Spy will save it only once, which allows you to reduce the size of the report. In addition, you can configure Power Spy to send reports via email in HTML format or upload them to an FTP server.
Real Spy Monitor 2.89
Developer: ShareStarDistribution size: 1.4 MB
Spreading: shareware Another utility that will help you keep track of who is doing what and when on the computer. The program supports working with multiple Windows accounts and, by generating a report, indicates which user performed certain actions. During the program setup process, you can select accounts that will automatically launch the program.
Reports compiled by Real Spy Monitor include information about all keys pressed and the titles of the windows in which typing was performed; about sites visited (addresses, headers, loading time); about opened windows (title, path to the program executable file) and files; about launched applications indicating start and close times. In addition, the program records messages exchanged between users of IM clients and can take screenshots at specified intervals. The collected information can be viewed in the program window (called by a keyboard shortcut), and also received in the form of an HTML report. To search for information among a large number of log files, a search is provided, and there is a function for automatically cleaning outdated data.
If you use a program to monitor the activities of children, then appreciate the ability to install filters on applications launched and sites opened. In the Real Spy Monitor settings, you can specify the path to executable files that cannot be launched by a particular user. As for sites, you can block certain resources by adding to the black list the full address of the resource or a keyword that the program will search for on the page. For young children, you can set more severe restrictions - allowing access only to those sites that are on the “white” list.
Maxapt QuickEye 2.8.8
Developer: STBP "Maksapt"Distribution size: 5 MB
Spreading: shareware If some other programs in this review can be equally successfully used for monitoring the actions of company employees and for tracking users on a home PC, then Maxapt QuickEye is aimed primarily at corporate users. Its main focus is on tools for viewing and analyzing reports. Thanks to this, the boss can quickly find out how much time each employee was actively working on the computer and what programs he was running. Interestingly, Maxapt QuickEye not only records open applications, but also takes into account whether active work was carried out with them. Thus, if the application window was open all day, but the user only worked with it for half an hour, then Maxapt QuickEye will display this in the report.
In the Maxapt QuickEye window, the applications that users work with are grouped into categories. Thus, by going to the “Games” or “Internet Communication” category, you can see on which computer such programs were active and for how long. All data can be presented in the form of a table grouped by computer or by time. In addition, you can see the report in the form of a chart or graph.
Reports provided by Maxapt QuickEye also contain information about the presence of employees at the workplace. The program records the moments of logging into the operating system, turning off the computer, going into sleep mode, and then automatically calculates how many hours and minutes the employee spent at the computer. In this case, the time when the computer was in sleep mode is subtracted from the total time when the computer was turned on. With Maxapt QuickEye, you can not only receive reports on how employees spend their working time, but also limit the use of certain applications. Using the utility, you can create a list of allowed and prohibited programs for each employee, and set a working time schedule.
Mipko Employee Monitor 5.0.4
Developer: LLC "Mipko"Distribution size: 4.8 MB
Spreading: shareware Previously, the Mipko Employee Monitor program was called KGB Keylogger. The main advantage of this utility over various keyloggers is that activity monitoring can be done remotely. Even during the installation process, the installation program warns about the presence of an antivirus in the system and the need to configure it accordingly by adding Mipko Employee Monitor to the list of trusted applications or exceptions.
The program is very flexible in working with multiple users; in this sense, Mipko Employee Monitor is an indispensable tool for a system administrator. For each user whose computers need to be monitored, you can set different monitoring options. So, for example, for one user you can set up tracking only the text typed, for another - to track only visited websites, for a third - to keep statistics on running programs, etc. The program can work using alarm mode. This means that when the user types certain words, Mipko Employee Monitor marks the user's activity with an alarm icon, and, with appropriate program settings, sends a warning message to the administrator by email or uploads it to an FTP server. The program is perfectly camouflaged; its monitor cannot be detected either in the list of running processes or in the list of services. To display or hide Mipko Employee Monitor, you need to type runmipko in the Windows command line or use a keyboard shortcut. Mipko Employee Monitor allows you to use tracking filters. Thus, you can create a list of programs whose activity needs to be monitored, but other running applications will not be monitored. The log size for each user being monitored can be strictly limited. By default, the program stores records about user activities for up to 90 days; if necessary, this period can be increased or decreased.
The information about user activity that this program collects would be incomplete without the ability to take screenshots. A snapshot can be taken only of the active window or the entire working area of the screen. By the way, on configurations with multiple monitors you can also take screenshots. When capturing the entire work area, the image is obtained in the form of two combined screenshots - the first and second monitors. The screen is captured either at certain intervals or when a new window is opened. In the absence of any activity, the creation of screenshots automatically stops so as not to generate identical and useless screenshots. Mipko Employee Monitor intercepts messages in all popular instant messaging programs - ICQ, Yahoo! Messenger, AIM, Windows Live Messenger, Miranda IM, Skype, Google Talk, Mail.Ru Agent, Qip.
Actual Spy 3.0
Developer: Keylogger Actual Spy SoftwareDistribution size: 1.6 MB
Spreading: shareware Using this program you can get information about different types of active use of your computer. Thus, it monitors the contents of the clipboard, stores information about the time when applications are launched and closed, takes screenshots of the desktop at certain intervals, and keeps track of the time the computer is turned on/off and rebooted. Actual Spy monitors keystrokes and sites visited, and also monitors documents sent for printing. The program saves changes to files and directories and records any links used by the browser.
The program is hidden using a keyboard shortcut and is then not visible either in the tray or in the list of running applications. Despite this "disguise", Actual Spy reveals itself by adding a corresponding entry to the list of programs in the Start menu, so if you decide to use this keylogger, do not forget to delete the folder of the same name in the menu. The user activity report can be saved in text or HTML format, on one or more pages. When viewing the report generated by Actual Spy, a flaw in the program immediately catches your eye - it only accepts keystrokes in the English keyboard. Therefore, if it becomes necessary to read, say, the text of an email in Russian, reading will turn into solving a rebus. However, Russian text copied to the clipboard is displayed correctly. Please note that the demo version of the program can perform its functions for forty minutes. Sometimes this is enough to protect your work computer during your lunch break.
NeoSpy 3.0
Developer: MC-Soft SoftwareDistribution size: 2.7 MB
Spreading: shareware
The most important thing for a spy program is not to give yourself away. The NeoSpy developers made sure that after installation the program is invisible on the computer. When installing the utility, you can choose administrator or hidden installation. In the latter case, shortcuts will not be created in the Start menu and on the desktop, the folder with the program will be hidden, and it will not be visible in the list of installed applications. To run NeoSpy, the administrator will need to use the Start>Run command. NeoSpy can intercept messages sent using various IM clients. It is gratifying that not only clients popular among English-speaking users are supported, but also those that are installed by the majority of Russians. We are talking about Qip, Miranda and Mail.ru Agent. In addition, NeoSpy copes with intercepting messages sent using &RQ, ICQ, SIM and other programs.
Using NeoSpy you can collect information about all applications that run on your computer. The program saves the start and launch time, the path to the executable file, and the window title. In addition, the report will indicate whether a screenshot was taken for each program. Screenshots can be viewed in a built-in utility with easy navigation tools. The module for viewing screenshots has a special scale indicating time, so if you want to find out what the user was doing at the computer at a certain time, just move the slider on this scale to the desired position. Using NeoSpy, you can monitor Internet activity on your computer. The program not only saves the addresses of visited sites, but also records when you connected to and disconnected from the Internet (of course, if the connection is not permanent), and tracks the amount of incoming and outgoing Internet traffic. By and large, NeoSpy makes it possible to track all the actions that were performed on the computer. Thus, the program saves everything that was typed on the keyboard, stores data that was entered into the clipboard, tracks changes in files, the creation of new files and their deletion. In addition, if necessary, you can save a complete list of applications installed on your computer.
Modem Spy 4.0
Developer: SoftCabDistribution size: 380 kb
Spreading: shareware This program offers a completely different method of "spying" - telephone. If a modem is connected to your computer, then using a small utility called Modem Spy you can record all telephone conversations. A very convenient feature, especially if your desk phone does not have this capability. Recording of telephone conversations can be performed automatically, while the program will keep statistics of telephone conversations in a special call log. During the recording process, the interlocutor's sound will not sound too low, since the program uses automatic signal gain control.
Audio recordings can be saved in any audio format - MP3, WAV, etc. Recorded telephone conversations can be played back through a sound card or played directly into the telephone line. Modem Spy can record conversations, even using modem models that only support data transfer (data modem). To do this, you need to connect the modem and the linear input of the sound card using a special adapter. You can also use Super Spy mode, in which calls will be recorded without the user noticing. Another feature of the program is recording from a microphone in voice recorder mode. Directly from the Modem Spy program, you can send your recordings by email. If the modem's technical specifications allow, the program can determine the caller's number. You can record conversations without the knowledge of the remote subscriber, or with his prior notification by enabling the appropriate program setting. Modem Spy has many parameters that allow you to fine-tune the modem to work with a telephone line - correctly detect a busy signal, detect silence in a conversation and cut it to obtain a smaller file, enable recording after a certain call, etc.
WillingWebcam 4.7
Developer: Willing SoftwareDistribution size: 4.6 MB
Spreading: shareware If we're talking about telephone spying, we can't help but mention video surveillance. It can be carried out using a webcam connected to a computer. This simple device, which many are accustomed to using to communicate with friends, may well be a real spy. You can turn a webcam into a spying device, for example, using the WillingWebcam program. Using it, you can remotely monitor what is happening near the computer next to which the webcam is installed. WillingWebcam can take pictures continuously at regular intervals or only when movement is detected in the frame. The resulting photos can be sent by email or uploaded to an FTP server. In addition, WillingWebcam can notify the user about the appearance of new pictures in other ways: by sending an SMS, launching another application, or playing an audio file.
Videos recorded using the program and photographs taken can be accompanied by text messages, as well as an indication of the recording time. In addition, there are many effects available that can be used to improve image quality, for example, increase clarity. WillingWebcam has a built-in module for viewing images and video files, organized like an Explorer. In it you can view thumbnails of images, play saved videos, and select different modes for viewing the list of files. If desired, images can be viewed in full screen mode. WillingWebcam can work in hidden mode. In this case, it will not be visible either on the taskbar or in the system tray. To exit the program from this mode, the default key combination is used, but it can be changed to another.
Elite Keylogger 4.1
Developer: WideStep Security SoftwareDistribution size: 5.3 MB
Spreading: shareware WideStep Security Software company releases three versions of its keyloggers - Family Quick Keylogger, Perfect Handy Keylogger and Elite Keylogger. The last option is the most functional and has the most features. For example, the Elite version is absolutely not detected by antiviruses, while Perfect Handy Keylogger is detected, but not by all antivirus packages, and Family Quick Keylogger is detected by any antivirus program. Due to the fact that the keylogger works at a low level of the system kernel, Windows does not slow down and good “compatibility” with antivirus programs is ensured. And yet, when running Elite Keylogger for the first time, Kaspersky Internet Security 2009 was suspicious of the new object and recommended sending it to quarantine.
The appearance of Elite Keylogger suggests that it is intended not just for tracking the user, but for continuous monitoring of activity over a long period of time. You can view activity statistics in the program by day using the calendar built into the program. Elite Keylogger allows you to define lists of Windows users who should or, conversely, should not be monitored.
Elite Keylogger monitors the operation of Internet messengers ICQ, MSN, AIM, AOL and Yahoo, monitors email, application activity and printed documents. The program can send the monitoring result by email, upload it to an FTP server, or copy it to a specified folder on a network drive. In the program, you can set a period of time, after which all user activity logs will be automatically deleted. You can also set the maximum size of the activity report, and also set the size of the log file, upon reaching which it will be sent by email. We draw your attention to one detail - if you want to remove this keylogger, you will not be able to do this using the standard Add or remove programs tool, or even using special utilities that control Windows startup. In order to uninstall Elite Keylogger, you need to go to the Options section and use the Uninstall keylogger button in the interface of the utility itself.
Conclusion
Those wishing to try a utility for monitoring user activity may notice that there is quite a large selection. The demand for such software is consistently high. First of all, such applications are in demand by organizations and firms where strict discipline reigns and strict requirements are imposed on employees regarding what they do at their workplaces. If recently the term “keylogger” meant a utility that recorded keystrokes, today such applications make it possible to monitor almost any type of activity - mouse clicks, launching programs, changing system settings, etc. Moreover, using the programs described in this article , control can be carried out remotely, tracking in real time what the user is doing, which window is active, what text he is typing and even with whom he is talking on the phone. Those who are concerned about privacy may be advised to use comprehensive protection (for example, an antivirus package and a activity monitoring utility) and rely mainly on themselves. Because for every lock, a thief, unfortunately, has a master key.Applications and special programs on smartphones are increasingly used by us in everyday life. We get used to using them to make purchases, conduct financial transactions, and communicate with friends around the world. If there is a need to further monitor your child’s social circle, listen to the conversations of company employees or family members, you will need a spy program for Android or iOS, which can be easily downloaded and installed on your smartphone. It will be useful for monitoring children, the elderly, household staff or employees.
What is spyware
To use the phone monitoring service, you must personally register on the program developer’s website. When registering, you must remember your login and password to enter the service, and confirm your phone number or email address. Spy programs differ from each other in their control functions and the types of presentation of information “taken” from the monitored device to you. This could be a screenshot, a table of calls, SMS, call recordings. The program for spying on an Android phone must be downloaded, installed, and activated on the smartphone secretly from the user.
Types of Spyware
Smartphone remote control programs are divided into the following types:
Spy functions
By monitoring a smartphone, the spy program for Android implements the functions of tracking and logging all actions of the object. Having collected information, depending on the type of functions you have chosen, on your smartphone or computer via the Internet, the utility will provide the opportunity to receive data:
- a log of incoming, missed, outgoing calls from subscribers with their names, duration of the conversation;
- audio recordings of telephone conversations;
- list and texts of all SMS, mms messages with the time of their receipt or sending;
- photo and video information captured by the spy camera of the controlled device;
- current location of the subscriber with online tracking of movements using geolocation using GSM operator base stations or GPS navigation;
- history of visiting smartphone browser pages;
- accounting of downloaded, installed, used applications;
- Sound control of the environment using remote microphone control.
Spyware for Android
Among the range of spyware programs offered, there are free utilities that, when analyzed and tested, turn out to be ineffective. To obtain high-quality information, it is necessary to spend money on collecting and storing photo, video, and audio information. After registering on the developer’s website, the client receives a personal account indicating the connected control functions and the collected information.
A paid mobile phone wiretapping program for Android is being developed taking into account the need to satisfy the most demanding customers in several respects:
- ease of installation;
- invisibility of being on a controlled smartphone;
- Convenience for the customer to receive and save the collected information.
Neospy
One of the simplest spy programs for a computer or smartphone is Neospy. NeoSpy Mobile for the Android platform is a legal application that can be downloaded from Google Play. When downloading the new version of NeoSpy Mobile v1.9 PRO with installation, downloading the apk archive, settings are possible in which the program will not appear in the list of Google Play applications, will be able to monitor the smartphone’s keyboard, and intercept photographs from the camera. The cost of using the program depends on the selected functions and will range from 20 to 50 rubles per day.

Talklog
More serious is the Android phone spy Talklog. Before installing it on your smartphone, you will need to disable your antivirus software. You will need to allow installation of apps from other sources in your phone's security settings. The Talklog service is a full-fledged spy that can obtain almost all the information about the activity of the monitored object. The utility has a free trial mode and several basic free functions. The cost will be from 10 to 50 rubles per day, depending on the functionality you need.

Flexispy
The spy program for Android Flexispy includes a huge number of ways to access a smartphone - intercepting SMS, mms messages, wiretapping the phone, recording telephone conversations, reading dialogues from 14 internal chats (Facebook, WhatsApp, Viber, Skype, WeChat, Telegram, etc.) , real-time call interception, listening to the phone's surroundings through the microphone, more than 140 more functions. The cost of using the utility is appropriate - the minimum Premium package will cost you 6,000 rubles for 3 months, the maximum Extreme package will cost you up to 12,000 rubles for 3 months of use.

Mobile Tool
The MobileTool spy application for the Android operating system will provide you with information about calls, SMS, MMS, phone location, phone book. It can remove its shortcut from the list of applications. You will have access to the following functions: viewing photos, protecting against theft by locking the device, turning on the siren. All information will be available in your personal account on the application website. There is a two-day trial mode to test the functionality; discounts depend on the period of use. The average payment for using the utility will be about 30 rubles per day.

Mobile Monitoring
Mobile spy for Android Mobile Monitoring (mobile monitoring) after registering on the site, choosing a tariff plan and payment will make it possible to save telephone conversations, the voice recorder function, save all SMS messages, geolocate the phone’s location, and build travel routes. The program works on smartphones of any mobile operators in Russia. The cost when choosing only geolocation will be 800 rubles for 3 months, full functionality – 1550 rubles for 3 months, with a 40% discount when paying annually.

How to install spyware on your phone
Installing a mobile spy begins with registering via the Internet on the manufacturer’s website, choosing a tariff plan, and paying for services. Then a link is provided that must be entered in the smartphone browser to download the program. Some spy programs for Android are available through Google Play and can be downloaded like regular applications. When installing and activating the program, you will need permission to access all the smartphone functions necessary for its operation. You may need permission to use programs that are obtained from unknown sources.
How to detect spyware on Android
Most spy programs for Android have the function of masking their presence on a smartphone. They can exclude themselves from the list of applications and not show their activity during periods of using the phone. Many antivirus programs can detect such software. To protect yourself from spyware and malware, you should get into the habit of running a full phone scan once a week or setting it up to run automatically on a schedule. The main signs of such programs running on your phone may be:
- slowdown of mobile phone operation;
- rapid battery drain;
- unjustified consumption of Internet traffic.

Video
Found an error in the text? Select it, press Ctrl + Enter and we will fix everything!If you are already interested in spyware and are monitoring this market, then your situation is favorable, all that remains is to choose a program and find out the truth. But for many users, the problem arises precisely in the choice - who to trust, what really works, and how much does the best quality cost? If you're at a crossroads, then this roundup of the best spyware on the market is for you...
Thanks to my ex-wife, I became a pro at spying capabilities. So, I found out that various bugs, cameras and other attributes are of little use for catching an unfaithful spouse, since the main activity is usually carried out on social networks and chat messages. Therefore, only a wiretapping program can give a complete picture. But which program should you choose?

First of all, you must clearly understand that when Google is such a service, in the Internet search results you will receive a lot of offers from detective agencies to magical ways of reading any information over the air. Therefore, to save your time searching, I give you a clear schedule right here and now:
— Only airborne infections are transmitted through the air!!! Remember this!
— Detective agencies are expensive!
— The wiretapping program should not cost more than $500! Because for this money she should not only transfer data to me, but also cook borscht and feed the cat. Spy technology doesn't cost that much.  — There are a lot of spyware sellers on the Internet, and only a few manufacturers. Vendors buy software from manufacturers and resell it to you and the walrus. Therefore, it is always more profitable to buy from the factory.
— There are a lot of spyware sellers on the Internet, and only a few manufacturers. Vendors buy software from manufacturers and resell it to you and the walrus. Therefore, it is always more profitable to buy from the factory.
Separating sellers from manufacturers is easy if you understand it. The location, IP, links and the brand itself are all googled at once. Therefore, I present to your attention the TOP 3 spy software manufacturers from which you can choose:
Manufacturer: Flexispy Ltd., USA Website: https://www.flexispy.com/ru/
First of all, I would like to mention the FlexiSPY product. Its manufacturers spare no expense on new developments, product safety and customer support in their native language. For this, respect and first place to them!  Advantages over competitors by points:
Advantages over competitors by points:
— Invisibility
For me, the most important thing is my safety, the program should not give away its work, because there is always a chance to improve the relationship... For almost a year of testing, FlexiSPY has never shown a single unmasking sign!
— The widest functionality
Basic functions such as interception SMS, calls, tracking by GPS And internet activity FlexiSPY clicks like a nut.
The most popular functions are interception of messengers, FlexiSPY also has the widest range of functions - 18 current ones and they are not going to stop - WhatsApp, Facebook, Viber, LINE, Skype, WeChat, iMessage, BBM, Blackberry PIN, Yahoo, Snapchat, Hangouts, KIK, Telegram, Tinder, Instagram, QQ… Let's move on to the advanced features - access to the camera and microphone is offered in the full Extreme package - recording telephone conversations subscriber camera pictures And environment recording phone via microphone.
Let's move on to the advanced features - access to the camera and microphone is offered in the full Extreme package - recording telephone conversations subscriber camera pictures And environment recording phone via microphone.
I can’t help but note the unique features of FlexiSPY – call interception And wiretapping the environment in real time. Today, due to legal nuances, these functions have been canceled for all other programs.
When my wife went to a bar with her ‘colleagues’, I heard a lot of interesting things right here and now, and not later in the recording, so sometimes these functions are simply vital...  - Price
- Price
The product has a golden mean in this regard too. Quality costs money, but reasonable ones. Therefore, the cost of programs starts from 68 USD per month, which is quite acceptable. You can upgrade to the advanced version by paying the difference at any time. There is no need to reinstall anything! 
— Russian support
The product has instructions and support in Russian. When I installed the program, I received advice about rooting and jailbreaking, including in Russian. This is very helpful for unsure users.
— Stability
Many competitors - Shadow copy, StealthGenie, SpyBubble and others have been forced to close in recent years due to legal issues that are very controversial in this business. Of course, no one returned anything to the users, so you need to choose a stable service.
The product has existed since 2005, those 10 years, and this is more than stable for the spy business!
Flaws
Unfortunately, the developers never released a Russified version of the personal account, citing the fact that they have users all over the world. However, a very important part has been translated into Russian - this is the installation and configuration section of the program. 
mSpy
Manufacturer: Bitex Group LTD., England Website: https://www.mspy.com
The next winner of the rating is a manufacturer called mSpy. I can’t help but note that these developers also know their stuff and produce cool software. But there is one feature for the Russian-speaking audience - they do not have a Russian version of the site. Therefore, if your English is not very good, then read above about the competitor, and if this is not a problem for you, then below is my review of mSpy. 
Advantages of mSpy over competitors by points:
- Price
The cost of the standard mSpy package starts from 29.99 USD, which is undoubtedly lower than its main competitors and this is the main advantage. For this money you will get the basic functions of spy software - SMS, MMS, call history, contacts, email, photos and videos, Internet activity, calendar, notes, applications, GPS tracking, as well as full service. 
- Solution without jailbreak
Here you can give a standing ovation! Of course, anyone forced to spy on someone wants to do it without access to the device... but the reality is that this is impossible. However, the mSpy developers offer one solution, which I cannot call an alternative, but it may suit a certain category of users - transferring data to a personal account from iCloud.
This solution is only available for iOS devices, only if you know the login and password for your iCloud account, and only if data synchronization with the cloud is enabled on the device.
The available functionality in this case is Whatsapp, iMessage, SMS, MMS, call history, contacts, internet activity, calendar, notes, applications for 69.99 USD per month. 
These are unique features of mSpy; no other competitor has them.
If you control your child, then blocking applications and sites is a very important function, you will agree. The child will not be able to open and view what you do not want, but cannot forbid him.
In the case of spouse control, a situation may likely arise where you do not want any subscriber to get through. But don't forget about alternative methods of communication. 
— Skype for support
Customer support is important for every client, especially when you are not buying Russian software and speak only your native language. In this case, of course, you need to choose a program that is supported in Russian. However, large corporations cannot approach each client individually, and they use special websites to support their clients; this is not entirely convenient for users who are accustomed to simple methods of communication. In this case, the advantage of mSpy is obvious - customer support via regular Skype at any time! 
Flaws
Like FlexiSPY, mSpy has not translated its personal account into any other language from English. This is a drawback to using the program for many users. 
TalkLog
Manufacturer: Talklog.Net
Third place in the ranking is occupied by very interesting software TalkLog, but it only works on the Android platform. It is interesting because it is sold by the manufacturer, and it is completely Russian-language.
This is a huge advantage, you might think, but this application has very little functionality. 
In detail:
Russian-language software
The entire program is in Russian, including the installation file. I tested it myself on my phone, and I must note that the installation takes no more than five minutes, everything is very simple and understandable to the most dense user. However, I recommend reading this post to the end. 
Due to such an easy installation, TalkLog cannot be considered as a full-fledged tracking program, but rather as a lightweight monitoring application for some phone functions - calls, audio control, SMS, MMC, media, location, Internet activity, applications and the ability to turn the device off and on.
Built-in chats are completely absent; who uses SMS these days? The cost of the program corresponds to the functionality. 
Since the program is installed without , it remains in the list of applications and can always be detected by the user, but this is the difference between downloading a powerful tracking program to the root folder of the phone and installing a simple application in 2 clicks - remember this! 
I can briefly summarize this long post like this - if you are looking for value for money, are worried about not being found out and want to know everything, then your choice. If you're on a budget or looking for some way to read information via iCloud without access to your phone, definitely choose mSpy. Well, if you need a solution for Android, but you don’t want to use customer support and want to see only the general activity of the subscriber without details and at a very low cost, then TalkLog should suit you!
If you have questions or suggestions, I will always comment!
Personal Monitor
YOUR CHOICE
for parental control
The best computer tracking program
The Mipko Personal Monitor program monitors (also covert surveillance is possible) the computer in 14 positions. Options for monitoring and covert surveillance of employee computers can be configured for each of the positions, or for several at once. The program interface is simple and easy to use; anyone can operate it.
I purchased your program when the need arose to control the child. He spent a lot of time on social networks, then disappeared somewhere on the street. To somewhat know what to expect, I looked for a program to track visited pages on social networks and intercept clicks. Your program has these functions in full.
Sergey Fedorov
Protection for your child
personal monitor for windows
Free version
for 3 days
Very convenient and intuitive interface
In order for anyone to use the program, its creators gave each interface action a simple name. Here you will not find complex technical terms, and the display of settings, work process and monitoring of computer tracking results will be clear even to those who have just begun to get acquainted with a PC.
Interception of messages in Skype, GTalk, Qip, ICQ, Mail.Ru Agent, Miranda and other instant messengers
It's no secret that instant messaging services are now extremely popular. Often, with their help, not only personal communication takes place, but “bad” matters are also discussed. ICQ interception occurs due to the fact that the user types his message on the computer keyboard.
Recording information entered from the keyboard
It is rare that a computer at home or in the office does not have a keyboard. The surveillance program records words and phrases in any language, as well as symbols, in its database.
Monitoring the contents of the clipboard
The great advantage of the program is the ability to covertly monitor even seemingly insignificant operations. This way you will always know the contents of the clipboard, which an ordinary user simply cannot do without while working on a computer.
Screenshots (screenshots) after a specified period of time
Monitoring intermediate stages of work on a PC also includes screenshots. Together with textual "intelligence" they help to get a complete impression of what is happening on the computer on which the program is installed. Depending on the settings, screenshots can display what is happening on the PC, either at regular intervals or with each mouse click.
Monitoring visited sites
Are you surprised where your traffic is going? Monitoring your computer will help you answer this question. You will receive a detailed report of all sites visited by the user. In addition, a list of addresses where your child accessed the Internet will easily explain why you are once again called to school. Hidden monitoring of visits to Internet sites will also make it clear why an employee of your company did not have time to prepare the monthly report on time.
Visible/invisible operating mode
Depending on the tasks you set, the monitoring program can work in both visible and invisible mode. In invisible mode, keylogger is not noticed not only by the users themselves, but also by anti-virus programs installed on computers (for this you must add Mipko Personal Monitor to the exceptions).
Monitoring program startup and termination
A significant addition to the picture of what is happening on a particular computer is monitoring the startup and closing of programs. This function can be useful both for finding out the causes of any technical problems, and for determining the timeliness or untimeliness of using a particular software application.
Monitor computer startup/shutdown/reboot
Another function of the monitoring program, designed to reveal the mysteries of PC behavior. Monitoring the computer's on/off/reboot allows you not to miss a single detail in the chain of events occurring with the machine/machines.