To ensure that two users can work on one computer at the same time is not such an exotic task. There can be many reasons for it: a banal saving of resources, the specifics of the software used (exists only on one machine, protected by a complex hardware license), an attempt to optimize the IT infrastructure with a minimum budget.
Depending on what the ultimate goal is, there are several ways to implement such a shared environment.
If you need just physical access, when only two sets of input-output devices are connected to one computer at once: monitors, mice, keyboards, then for this you must also have the appropriate software that allows you to share resources, and each get their own session. desktop, etc.
To connect two users to one computer, you need
1. Video card with two or more outputs. If there is only one monitor output, then you will need to purchase an additional video card.
2. Monitors;
3. Keyboards and mice;
4. Specialized software (only paid), which will allow the sharing of resources. Their list is quite wide - Aster (a Russian product, and one of the best in this regard), BeTwin, Multiseat (for Linux), Userful, MS MultiPoint, SoftXpand, etc.
The most practical in this regard is the multi-user Aster system, which fully supports hardware video acceleration, as well as the work of many popular office programs, at least 1C, etc.
This product stably performs its functions on Windows from XP to 8.1, and supports up to 10 simultaneous users.
Everyone can try this software, with a trial period of 30 days - just download it on the developer's website and install it.
The developer constantly maintains the product and introduces new versions - the next one will already fully support up to 12 sessions, and Windows 10.
Basic versions target small companies and knowledge is poorly represented. Sometimes copied documents are posted, but they give few answers, and upon close examination, raise more questions.
Perhaps this is due to the low cost, and therefore the profitability of the program, and they do not strive to engage in it. As a result, we get a manager who does not understand why you need to pay much more if you can put a pirated version.
Main differences with PROF versions
- The basic version is several times different in cost. For example, the price of 2014: 1C: Enterprise Accounting 8 for 3300 rubles, versus the PROF version for 13000 rubles.
- The basic version is provided with support for free (for PROF you need an ITS) and even receiving updates.
- It remains possible to expand the basic version to PROF with the deduction of the amount that was paid for it; it cannot be done in the reverse order.
- The technical limitations of the basic version are one of the big drawbacks. The main thing is that only one user can work with infobases.
The last limitation makes you think, and if the number of users is not important for you, then when buying a 1C program, think about the opportunity to purchase basic version, this will significantly save money. You need to solve problems in order. When the need arises for several users to work simultaneously, then just go to PROF.
An exception is the Trade Management program, ed. 11 Basic. The limitations that are set in it can really complicate the work in general.
Differences in details
Programs from 1C include a "technological platform" and an information base of various configurations. The platform itself has nothing to do with configuration and is the same for both versions. The license for the basic version is tied to the configuration. If you install Accounting and Trade Management in the basic version, then different licenses will hang on the computer. In the case of the full program, the license can be installed at all on any computer in the internal network. If the license is not found during the first launch, then software license, will offer to get 1C itself. Computer data and configuration are transferred to 1C and returned back with a key to enter this computer.
"PROF" license can run all bases, and "Basic" - only one configuration.
You can create as many databases in the configuration as you need and place where it is more convenient for you (local disk, network). If you change the field of activity, you can completely delete the infobase and start new ones. You do not need to re-license.
Basic version limitations
All restrictions are indicated in the documents and on the box, but we will reveal some in more detail.
1. Only one user can work with one infobase at a time.
This means that it is impossible to work with the database at the same time. You can create different rights for different employees, for example, salesman, accountant, director. One works during the day, the second in the evening, the third at night.
2. Modification of the configuration is not supported, you can apply only the standard configuration and install its updates.
In fact, the "configurator" itself is available, as in the full version. There is no possibility to change the configuration. In the database, you cannot change the "supplier object is not editable" feature, and in the basic version, in the configurator menu, you cannot work with the repository and configuration delivery, but a small company does not need it. If you remove the basic configuration from the full version support, then it will no longer be opened in the basic version.
3. COM connection and Automation server are not supported.
This means that you will not be able to start 1C this way, but at the same time, you can refer to other objects from the basic 1C using a COM connection. Without external connection mode, you can start 1C using data exchange via files.
4. Operation of RIB is not supported.
The configuration prohibits the exchange of adding new nodes to the "Full" plan. In another configuration, "Salary and personnel management", the same restrictions are on the exchange plan "By Organization".
Separately, we will clarify the configuration Trade 11 basic.
- There is a complete absence of source modules.
- More functional limitations.
Let's draw a line under all the restrictions. If users will work in the program at different times or only one employee, then you can save on updates. If you need the full version, use the extension, because the money you have already paid will also be credited.
Today, in the article, we will talk about how, without outside help, configure access to the documents necessary for work, various reports and reference books, and vice versa - restrict access to some information. For this, the so-called command interface with flexible settings, which appeared in the new version of the 1C program, is intended.
Based on the 1C configuration, we will discuss the specifics of differentiating access rights to different program objects. The same algorithm can be successfully implemented for the "1C" program of the latest version "3.0".
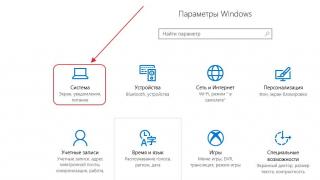
How to create a user in 1C in the normal user mode?
We want to say right away that we will have to work with 2 modes: program operation and. There is nothing difficult about this, since programming is unnecessary. Also note that the screenshots in this material were used from the Taxi interface of the 1C software version 3.0. To switch to it, open the service menu and find the parameter settings there. Among the "Appearance" radio buttons in the parameters window, select the "Taxi" interface and restart the program. Although, if you wish, you can work in the usual interface - all settings, reference books, documents in this appearance are identical to "Taxi".
Consider a situation where you don't have the required user yet. It needs to be created in the normal user mode. To do this, go to the main menu "Administration" and find there an item called "Configuring users and rights".
Select the "Users" link in the window, and after the new directory opens, add the name of the new user to it. In the user settings field, specify his name and check the boxes next to “Program entry allowed” and “Show in the selection list”. If you do not install the latter, then when you start the system, you will not see this user in the drop-down list. Then you will need to type its name manually.
Also, if necessary, you can immediately set a password.
Now let's dwell on the access rights to this newly created user. You don't need to install them. Access rights settings can be accessed from the form where the user is “configured”. To do this, follow the link "Access rights", which is located at the top of the link. It is also necessary that the tabs in the access rights - "Access groups" and "Permitted actions" - be empty.
But there is an important detail here. You need to have at least 1 user in the database who has administrative rights. For example, we have such a user is the Administrator. He is part of an access group called Administrator, and also has the Full Rights and System Administrator roles.
Next, go to the configurator mode and continue the settings in it. To do this, when starting the "1C" program, select the required base and click on the "Configurator" button. But you shouldn't log in as a new user. The job will be impossible, since he does not yet have any rights. And to enter, as you already understood, you need to use a user with full rights, in our case it is "Administrator".
To verify that the created user is visible, open the configurator window. For reference, the user list is saved in the main menu heading: "Administration" - "Users".
The figure shows that the user has a question mark. This means that no access rights have been specified for it. "Roles" is a configuration object. Each of them specifies a number of directories, documents, reports, to which only the user who has the role has access. By going to the bookmark, you can see all the roles.
Now the task is to configure employee access to an arbitrary set of various kinds of reports, documents and reference books. In this case, it is not so important what kind of set we are talking about. It is important for which cases in the configuration the role cannot be applied. After all, the developers of the 1C program are not able to foresee absolutely all options for differentiating access to objects that may be encountered in practice. And requests can be too unpredictable.
Configuration editing mode in "1C"
It follows from the above that you need to create your own role. The creation of such indicates that changes will be made to the typical configuration. For those users who have already finished it, there will be no changes.
Now let's determine if your configuration is typical or not. First open the configuration. To do this, click "Open configuration" in the "Configuration" section of the main menu. A window with the structure of information objects should appear in the left part of the configurator. base. Then go to "Support" - "Support settings" (menu "Configuration"). If an open window of the same name has a view as in the figure, then you have a typical configuration. This means the presence of an inscription called "The configuration is under support" and the button "Enable the ability to change."
If you have a typical configuration, you will have to enable the ability to change it, since otherwise you simply cannot create a new role. Note that all standard objects will remain common, because you do not need to change existing roles, but simply create new ones. To edit the configuration in the "Support Settings" window, press the "Enable Potential Changes" button.
After clicking, a warning will open stating that changing the mode will lead to the impossibility of automatic updates. But with this type, objects will be automatically updated, since the main task is to create a new role, and not modify existing ones. During the update, several new windows may appear, in which you must click "Next".
After that, open the window titled "Configure support rules" and select the radio button "Provider object is edited while maintaining support". Click "OK", and wait a little before proceeding further.
The locks will disappear in the tree of configuration objects opened on the left in the configurator. Immediately in the "Support Settings" window, the message "The configuration is under support with the ability to change" will be displayed.
Creating a new role in the 1C program configurator
Now focus on the work of creating the new role. Let us recall that "Role" is a right that provides the ability to edit or view various types of configuration objects: reports, directories, documents. Editing and viewing are the most well-known and understandable options for access rights. But there are many others. Let's talk about this in more detail. In the tree of objects open "Role" "Full rights" ("General" - "Roles" - "Full rights"). The program objects - documents, reports, reference books - will be listed in the left part of the settings window. And on the right side are those rights that are defined for each of the objects in this role. This process is reflected in the presented figure.
Let us recall that our task is to ensure that we work only with a limited number of program objects. The best option would be to create a new role and set access only to the objects you need. A configuration has a variety of different utility objects, in particular, general purpose objects, constants, common modules, and forms. And for normal operation, each user must have access forms to these objects. As we said, there are too many of them and one of them is very easy to overlook. Therefore, we will offer you a slightly different approach.
By copying a typical role called Full Rights, create a new role and name it Frolov_Role. And to change its name, just go to "Properties" and enter another name without spaces.
Now our task is to create a new role for the so-called user "Frolov". But before this operation it is necessary to save the information. base so that the role reappears in the list of user roles. To do this, press the "F7" button or the corresponding key on the toolbar. Now our user can set the role. By clicking "Administration" and "Participants" go to the list of users and on the "Other" tab mark the "Role_Frolov" checkbox. Click "Ok".
While the role is the same as the original one, we will leave it in this form for now. Using the flexible configuration of the 1C command interface, we will configure access to reference books and documents.
Configuring the elements of the command interface in the "1C" program
And now return to the user mode of operation, I mean, to normal work in the 1C program. Now, using the configurator, you need to start work under "Frolov S.M." - our new user. But first, set the settings so that when you start "Enterprise" from the configurator, the program will make a request for the user under which it will run. To perform the specified in the main menu, click "Service", then - "Parameters" and in the "User" section, which is in the "Launch 1C: Enterprise" tab, and select the "Name" switch. Click "OK", and from the configurator, using the command "Service" - "1C: Enterprise", start the user mode. We remind you that initially you must select the user Frolov.
When "1C" is launched on behalf of the user Frolov, the latter will have access to all the necessary objects, since his role was created on the basis of copying new rights. And we didn’t make any changes. Let's try to experiment, for example, leave for the user only such possibilities of personnel accounting as release, reception and movement. First, remove unnecessary sections, leaving only one - "Frames".
Now go to the service menu, click "View" - "Customize the section panel". In this window, move all unnecessary sections from the right column to the left.
We have 2 sections left under the names "Personnel" and "Main". We cannot eliminate the last of the above, since only the necessary links need to be left in it. To do this, go to this section "Main" and in the upper right corner click "Navigation settings". This window is very similar in appearance and operation to the one in which we removed unnecessary sections. In the right column, leave only the objects you need for work - directories and documents.
As a result, in the "Main" section you will only have the necessary number of reference books, reports and documents.
Now let's pay attention to the "Personnel" section. It can be left unchanged, or, if desired, set up more "subtly". This can be done if the employee does not have to deal with maternity, leave, or sick days according to the plan. Also, the above-mentioned documents in the navigation bar can be removed. But these are already separate nuances that depend on the specific task, so we will not dwell on this in detail.
Let's dwell on one more point - an element that also needs to be configured. This will prevent the user from accessing information that is closed to him. The item is called "Start Page" or "Desktop". It can be opened when starting user mode. To customize the start page in the service menu, open "View" - "Start page settings". In an open window, among a number of available forms, you can customize the composition of the right and left columns. The list of all available forms is not too long. For example, for a human resources employee access to the Payroll Form is not required. But in this case, we decided to remove all forms so as not to tempt the user. Therefore, the "Start Page" will be blank.
Screen 21
How to set up a user role in the 1C program configurator
Suppose that using the services of the command interface, we configured access to the necessary objects - directories and documents, a personnel officer. Now the question is how to prevent the user from customizing the interface and having access to taboo documents?
To do this, return to the configurator and select "General" - "Roles" - "Role_Frolov" in the configuration objects tree. Having opened this role, in the window click on "Salary and Personnel Management", and in the "Rights" column, find the settings under the name "User data retention". And uncheck the box next to this parameter. This means that from now on, the user will not be able to independently customize the section panels, in particular, the desktop and navigation panels, and, accordingly, will not be able to access prohibited sections from the command interface.
To verify the above, log into the system as Frolov and try to open access to navigation or sections. You will also not be able to open the "View" item in the service menu. The latter became unavailable, since we removed the rights to "Save user data" in the role of Frolov's user.
So, we have opened the user access only to those documents, reports and reference books that he needs for work. Please note that for such restrictions in the rights of an employee, we have removed only 1 mark.
We also restricted access to prohibited documents. However, there is one caveat: the user from the document available to him can get into the prohibited ones. For example, from the document “hiring” the HR officer Frolov can get into the directory “Organizations” and purposefully or accidentally make changes to certain data. To avoid this, we recommend that you view and analyze objects that have a connection with information available to HR personnel. Open the user role in the configurator and prevent viewing or editing unwanted documents or reports. Select the required option depending on the task at hand.
Today, many families already have a PC. At the same time, there is usually only one computer, and all family members want to work on it - both children and parents, and even grandparents.
At the same time, children most often want to play and communicate via the Internet, and parents often need a stable PC and the safety of their data. Therefore, it becomes necessary to configure the PC for the work of several users.
The purpose of this setup: separation of user access to files, folders, programs.
I will simplify the division of users into parents and children.
Depending on the importance and type of data that users work with, I will highlight the following ways to achieve this goal:
1. Installing multiple operating systems.
This method is best used when the data is very important and complex, for example, when working with databases based on MS SQL Server or Oracle.
Different operating systems are installed on different disks (disk partitions), users are configured in these operating systems, users choose their own operating system when starting the PC.
2. Using additional programs.
In this case, one OS is installed on the PC, and software for hiding data is additionally installed.
Examples of such software: BestCrypt, Hide Folders, Folder Lock, Kaspersky KryptoStorage, 1 Click & Lock.
As a result, access to folders and files can be restricted with a password, but if the encryption program fails or the password is lost, it is possible to permanently lose data. Most of these programs are paid.
3. Using virtual machines.
Virtual machine Is a special program that creates a "PC within a PC".
The user has the ability to configure multiple OS (virtual machines) to work.
This method requires a fairly powerful PC. virtual machines use actual resources - processor, memory, hard disk; the user gets two or more simultaneously running OS at the same time.
The virtual machine files on the actual OS are one file and cannot be accessed without starting the virtual machine.
4. Setting up multiple users on one OS.
In this case, several users are configured in the OS, then users are given different rights, and when the OS is started, the desired user is selected.
The first method requires deep system knowledge about the OS, the second is quite risky, the third requires a powerful PC (which not everyone has), the fourth is the easiest for most users.
In this article, I will show you how to set up your operating system. Windows XP Pro for multiple users.
In operating systems of the family Windows since NT, there is a concept "Account".
Account designed to identify the user and determine his rights in the OS.
When the user is alone, then usually when the OS starts, the welcome screen is visible, and then the desktop immediately appears. In this case, the user has all rights in the OS. In this case, the user logs into the OS under the built-in account. administrator.
To set up multiple users, you need to create multiple accounts. To do this, you need to start the console " Computer management».
Users can also be configured through the utility " user accounts"Which is launched from the Control Panel, but I believe that the console" Computer management"Has more customization options.
You can start the console like this: right-click on the icon "My computer" and select the item in the menu that appears "Computer Management" or through "Start" - "Settings" - "Control Panel" - "Administrative Tools" - "Computer Management".
Expand the branch in the left window "Local Users and Groups"(the "Utilities" branch is usually open) and select the folder "Users" as shown in the picture below:
Now the OS user accounts are visible in the right window. In this example, there are 5 accounts. Double-clicking on the account opens the properties window.
The following picture shows the Properties window for the Guest account.

Account « a guest» is intended mainly to provide minimal access to PC resources over the network.
Recordings « SUPPORT» and « HelpAssistant» are intended for help and support services.
Recording « ASPNET» designed to run some system programs.
Recording « Admin» - This is a built-in administrator account, usually after installing the OS, the user boots under it. Depending on the version (assembly) of the OS, this entry may also be called " Administrator" or " Administrator».
On the General tab, you can specify the full name and description of the account, as well as configure some properties of the account password.
I will provide a simplified description and purpose of these properties.
Require change user at next login.
If this checkbox is checked, then the next time you log on to the system, the OS will ask the user to change the password.
This property is supposed to be applied in the following way: the system administrator creates a new account with some standard simple password, for example "12345". Then the user, when logging into the OS under this new account, changes the password to his own.
As a result, it should turn out that only the user himself knows the user's password, while it is recommended to use a password of at least 6-8 characters, containing letters in upper and lower case, numbers, special characters.
This property is designed for conscious users who understand the importance of protecting information and are trying to ensure a high level of security.
Prevent the user from changing the password.
This checkbox during installation prohibits the user from changing the password on their own. This property should be used if users are unconscious and want to change a complex password provided by the system administrator to a simple password.
The password does not expire.
If this checkbox is not checked, then the user must periodically change the password. The default password expiration date, if I'm not mistaken, is 42 days. If the password has expired, the recording is blocked.
Disable account.
This checkbox is needed when disconnecting an account. The recording remains in the OS, but does not work. This is used, for example, when a user goes on vacation, his recording is disabled, and no one can log into the OS on behalf of this user, and after going to work it turns on again.
In my example, records are disabled « a guest», « SUPPORT" and " HelpAssistant» ... In the list of accounts, they are marked with a red circle with a cross.
Block account.
This checkbox is needed to unlock the entry. The user can only remove it. If the account is blocked for some reason, a checkmark appears in this field, and to unblock the record it must be removed.
A similar description of the fields of this window can be read through the built-in tooltip. To do this, click the "Question mark" icon in the upper right corner of the window, the cursor will change to a prompt, then move the cursor to the required field and click again. A prompt window with a description of the object should appear.
Creating a new account.
For this you need in the window "Computer Management" select branch "Users", then select from the menu "Action" - "New user" as shown in the picture below.

A window for creating a new account should appear. In it you need to enter Username, you can even use the Cyrillic alphabet.
If you want, you can enter the full name and description, these fields are more useful in organizations with many users.
After the name, you must enter the password in the fields 2 times "Password" and "Confirmation".
This is done in order not to make a mistake when typing the password. If the password and its confirmation do not match, a message about this will appear during creation.
At the end of the settings, press the button " Create". After that, the system will create a user and offer to create the next one. If necessary, create the next user; if not, press the button " Close».

Thus, we create accounts for all users. In the example, I created the records “ Parents" and " Children».
On your PC, you can create users for each family member. If there are several users, then I recommend creating their own account for each, and using the built-in OS administrator account only in case of problems.
After that, you need to create or change a password for the current administrator account.
To do this, select the entry in the right window « Admin» , then select from the menu "Action" - "Set password".

In this case, the OS will issue warnings about the consequences of such an action.
If you are an experienced user and use file encryption, personal certificates and / or other security measures, then the password must be changed / set in a different way.
For novice users, you must agree and set a password. The password must be entered twice to avoid typing errors.

ATTENTION!!!
WHEN ENTERING PASSWORDS, ALWAYS FOLLOW THE CURRENT KEYBOARD LAYOUT AND BUTTONSCAPS LOCK AND NUM LOCK !!!
ALSO DISABLE PUNTO SWITCHER !!! (if installed)
Very often I come across the fact that users forget about the layout and change the password in the Russian layout, and then, when entering the OS, they try to type it in English.
The same goes for the CAPS LOCK and NUM LOCK buttons.
And PUNTO SWITCHER can change the layout in the middle of typing a password (I have come across such cases).
In this case, the password is entered incorrectly, the user cannot enter the system.
Those who encounter this for the first time often get lost and think that they have broken their PC or Windows and begin to panic.
If the password does not work when entering the OS, check the layout again, the CAPS LOCK and NUM LOCK buttons, and try to enter again.
If the OS is not configured (not configured by default) a limit on the number of unsuccessful attempts, then the password can be entered an infinite number of times, and if configured, then the recording is blocked after a certain number of unsuccessful attempts.
To do this, press "Start" - "End of session" - "Change user".
After that, you should see something like this (part of the screen is shown so that the clarity of the inscriptions does not disappear during compression):

In the middle of the screen there is a hint "To get started, click your username", at the bottom left is the "Turn off computer" button.
On this screen, the PC user is asked to select his account (you can hover the mouse and click the left mouse button) and enter a password.
If you end the previous session after "Start" - "End session" - "Change user", then the programs of the previous user will work - this can be seen in the line under the name - "Programs in progress: 4".
And if through "Start" - "End session" - "Exit", then all programs started by the user will be terminated.
System programs of the OS, as well as programs running as system programs, for example, antivirus, continue to work when changing users.
It is convenient to use when you need to quickly boot the OS under a different user.
If suddenly, when the PC boots up, the "Administrator" will not be visible, then press the Alt + Ctrl + Del key combination, a window for entering a name and password should appear.
In it you need to type accordingly "Administrator" and the correct password, after which this entry will be loaded.
On subsequent downloads, the name "Administrator" will already be in the required field. On my PC, this happened a couple of days (and 4-5 reboots) after setting up new users, and I press the Alt + Ctrl + Del key combination twice to bring up the window for entering a name and password, although once should be enough.
Try to log in with each user to check if the password is correct and to create user profile folders on disk.
Profile folders are folders in " C: \ Documentsand Settings \».

After checking simple passwords, try to create more complex ones that suit you, and check them.
Different passwords must be created for all users.
After creating and loading a new account, the user will see on the desktop the program shortcuts that have been installed for all users.
Some programs have the option of choosing during installation: "For all users" or "For the current user".
New users' desktop settings will be created "by default", but each user can customize it to suit their needs.
In the OS in question, all users are divided into groups, depending on what kind of work they do. The OS already has built-in groups, as shown in the picture below.
OS users can also create other groups if they are members of the OS Administrators group.

Working with groups is useful in organizations with many users.
for instance, a shared folder with files for a department is created, access to this folder is allowed to a group of users.
When joining or leaving a department, a user account is added or removed from the group, and nothing changes in the folder properties.
Similarly, if you need to open access to a folder for the entire department, then access is opened for the entire group, and not by enumerating all the necessary users.
In the case of a home PC, it makes no sense to create new groups. few users.
When you create a new account, it falls into the group " Users". This is enough to run programs, work with documents, the Internet.
To install and configure programs, you must be a member admin groups.
Initially, users do not have access to the profiles of other users; when they try to access, the OS will display a message, as shown in the picture below.
In this example, the user " Children"Tries to access user profile" Parents».

User " Parents»Must be added to the Administrators group.
To do this, join the group " Administrators", Make a double click, the window" Properties: Administrators».
At the bottom left there is a button " Add", You have to press it.
After that, the window “ Choice: Users».
In it you need to press the button " Additionally»At the bottom left.

The user search window will appear.
In it you need to press the button " Search»Right in the middle. Then find the account in the list "Parents", select it and click " OK».

In the window " Choice: Users"A line like this will appear:
"MICROSOF-9960C1 \ Parents".
The first part is the name of the PC, the second is the name of the entry.
After that, you need to click " OK».
As a result, the window “ Properties: Administrators"Should look like the image below.

We press " OK"And we get that the" Parents "user can view the profile of the" Children "user, but on the contrary not.
As a result, the “Children” user cannot change the files in the “Parents” user profile without using special system methods and programs.
If you need to install new programs or games or remove old ones, you can do this from the user "Admin" or "Parents".
If the program or game after installation does not create shortcuts and / or groups of shortcuts for the "Children" user, then the shortcut for launching this program must be placed in the " C: \ Documents and Settings \ Children \ Desktop \", The" Kids "user will see this shortcut on his desktop.
How to configure access to a folder on another partition / disk, I will tell you in the next article.
Article author: Maxim Telpari
PC user with 15 years of experience. Support specialist video course "Confident PC user", after studying which you will learn how to assemble a computer, install Windows XP and drivers, restore the system, work in programs and much more.
Make money with this article!
Sign up for an affiliate program. Replace the course link in the article with your affiliate link. Add the article to your site. You can get a reprint version.

How to set access rights in 1C 8.3 program?
In this article, we will consider how to work with users in 1C Accounting 8.3:
- create a new user
- configure rights - profiles, roles and access groups
- how to configure restriction of rights at the record level (RLS) in 1C 8.3 - for example, by organization
The instruction is suitable not only for an accounting program, but also for many others built on the basis of BSP 2.x: 1C Trade Management 11, Salary and Personnel Management 3.0, ERP 2.0, Small Firm Management and others.
In the 1C program interface, user management is carried out in the "Administration" section, in the "Setting up users and rights" item:
How to create a new user in 1C
To create a new user in 1C Accounting 3.0 and assign him certain access rights, in the Administration menu there is an item “User and rights settings”. We go there:

The list of users is managed in the "Users" section. Here you can create a new user (or user group), or edit an existing one. Only a user with administrative rights can manage the list of users.
Let's create a user group called "Accounting", and in it two users: "Accountant 1" and "Accountant 2".

To create a group, press the button that is highlighted in the picture above and enter the name. If there are other users in the infobase who are suitable for the role of an accountant, you can immediately add them to the group. In our example, there are none, so we click "Save and Close".
Now let's create users. Place the cursor on our group and press the "Create" button:

In the full name we will enter "Accountant 1", we will set the login name "Bukh1" (this is what will be displayed when entering the program). We will indicate the password "1".
Be sure to make sure that the boxes "Login to the program are allowed" and "Show in the selection list" are checked, otherwise the user will not see himself during authorization.
Leave the "Start mode" as "Auto".
Setting up access rights - roles, profiles
Now you need to specify the "Access Rights" for this user. But first you need to write it down, otherwise a warning window will appear, as shown in the picture above. Click "Write", then "Access Rights":

We select the profile "Accountant". This profile is standard and configured for the basic rights required by an accountant. Click "Write" and close the window.
In the "User (creation)" window, click "Save and close". We also create a second accountant. We make sure that users are signed in and can work:

It should be noted that the same user can belong to several groups.
We chose access rights for accountants from those that were included in the program by default. But there are situations when you need to add or remove some right. To do this, it is possible to create your own profile with a set of necessary access rights.
Let's go to the section "Access group profiles".
Let's say we want to allow our accountants to view the log.
It is quite time consuming to create a profile from scratch, so let's copy the Accountant profile:

And let's make the necessary changes to it - add the "View the registration log" role:

Let's give the new profile a different name. For example "Accountant with additions". And check the box "View the logs".
Now we need to change the profile of the users whom we added earlier.
Restriction of rights at the record level in 1C 8.3 (RLS)
Let's figure out what the restriction of rights at the record level means, or as it is called in 1C - RLS (Record Level Security). To get this opportunity, you need to check the appropriate box:

The program will require confirmation of the action and will inform you that such settings can greatly slow down the system. It is often necessary that some users do not see the documents of certain organizations. Just for such cases, there is a setting for access at the write level.
We go back to the profile management section, double-click on the “Accountant with additions” profile and go to the “Access restrictions” tab:

Select “Access type”, “Organizations”, “Access values”, select “All are allowed, exceptions are assigned in access groups”. Click "Save and Close".
Now we return to the "Users" section and select, for example, the user "Accountant 1". Click the "Access Rights" button:
Using the "Add" button, select the organization, the data on which will be seen by "Accountant 1".
Note! Using the mechanism of differentiation of rights at the record level may affect the performance of the program as a whole. Note for the programmer: the essence of RLS is that the 1C system adds an additional condition to each request, requesting information about whether the user is allowed to read this information.
Other settings
Sections "Copying settings" and "Clearing settings" questions do not cause their names speak for themselves. These are settings for the appearance of the program and reports. For example, if you have customized the beautiful appearance of the Nomenclature reference book, it can be replicated to other users.
In the "User settings" section, you can change the appearance of the program and make additional settings for the convenience of work.
The checkbox "Allow access to external users" allows you to add and configure external users. For example, you want to organize an online store based on 1C. The customers of the store will just be external users. Setting up access rights is carried out in the same way as for ordinary users.
Based on materials: programmist1s.ru